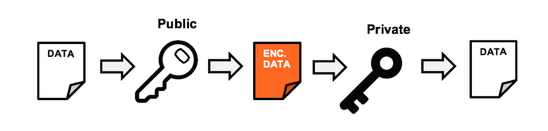
Mobile Application Management (MAM)
The biggest challenge for BYOD devices is data security and leakage, a common method to enforce data protection is through Exchange ActiveSync and/or Mobile Device Management (MDM) tools such as AirWatch, Intune and others.
Both ActiveSync and MDM comes with the option of device wipe and enforcing device PIN. If the device is lost or the employee is terminated, the company could remote wipe the device to protect its data. While device wipe is great from the company’s perspective, it is almost always met with resistance from the employees because everyone fears the company has the power to wipe their personal data such as photos and contacts from their own personal devices.… [Keep reading] “Mobile Application Management (MAM)”