SailPoint IdentityNow Active Directory Source TLS Configuration
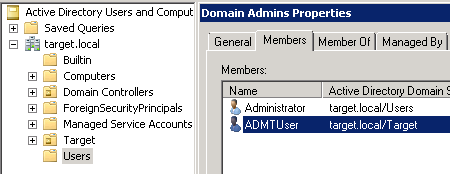
Recently I needed to enable a SailPoint IdentityNow Active Directory Source to use TLS. Looking for information on how to complete this saw me read many articles in SailPoint Compass. However, none of them were written specifically for IdentityNow Active Directory Source TLS Configuration. Mostly they were for the IQService and Identity IQ. Putting pieces of this information together I got an existing Source (even though it is mentioned this shouldn’t work) updated and working for TLS.… [Keep reading] “SailPoint IdentityNow Active Directory Source TLS Configuration”