We recently came across an issue with a customer where they had configured a standard SSO experience with Office 365 using ADFS and it was working perfectly except for a specific use case. When a user accesses the office store via the Office 365 portal (e.g. portal.office.com/store) they got into an endless SSO login loop. Specfically, they would see the following:
- Connection to Portal.Office.com
- Redirection to login.microsoftonline.com
- Redirection to adfs.customerdomain.com (automatically signed in because of WIA SSO)
- Redirection to login.microsftonline.com
- Redirection to Portal.Office.com\Store page but loads partially and then redirection to login.microsoftonline.com
- Redirection to adfs.customerdomain.com (automatically signed in because of WIA SSO)
- Rinse and repeat steps 4-6 ad nauseum
Normally, steps 1-4 is expected, because what is normally happening here in laymen’s terms are:
- Portal.office.com provides a response to the user’s browser saying “please provide sign in credentials, and do so via redirecting to this url”
- login.microsoftonline.com provides a reponse to the user’s browser saying “we know you are trying to access @customerdomain.com resources, which is federated, so please connect to adfs.customerdomain.com and get a valid auth token to present to us”
- User connects to adfs.customerdomain.com, and because it’s in it’s trusted sites list, and trusted sites is configured to perform windows integrated auth (WIA), the user’s browser uses the computers cached kerberos/ntlm auth token to sign into ADFS. ADFS responds with a valid SAML token which the user can present to Azure AD.
- User connects back to login.microsoftonline.com and presents the auth token. From there it is validated and an auth token browser cookie is created.
- At this point, the user would normally then connect to portal.office.com and access the relevant resources.
Now this was certainly the case for the majority of services in Office 365, including the main portal, Exchange Online, Sharepoint etc. It was just the Office Store that was the problem, and bizarrely it was doing a partial load and then getting into the loop.
The resolution to the problem was discovered by doing a Fiddler trace of the sign in traffic.
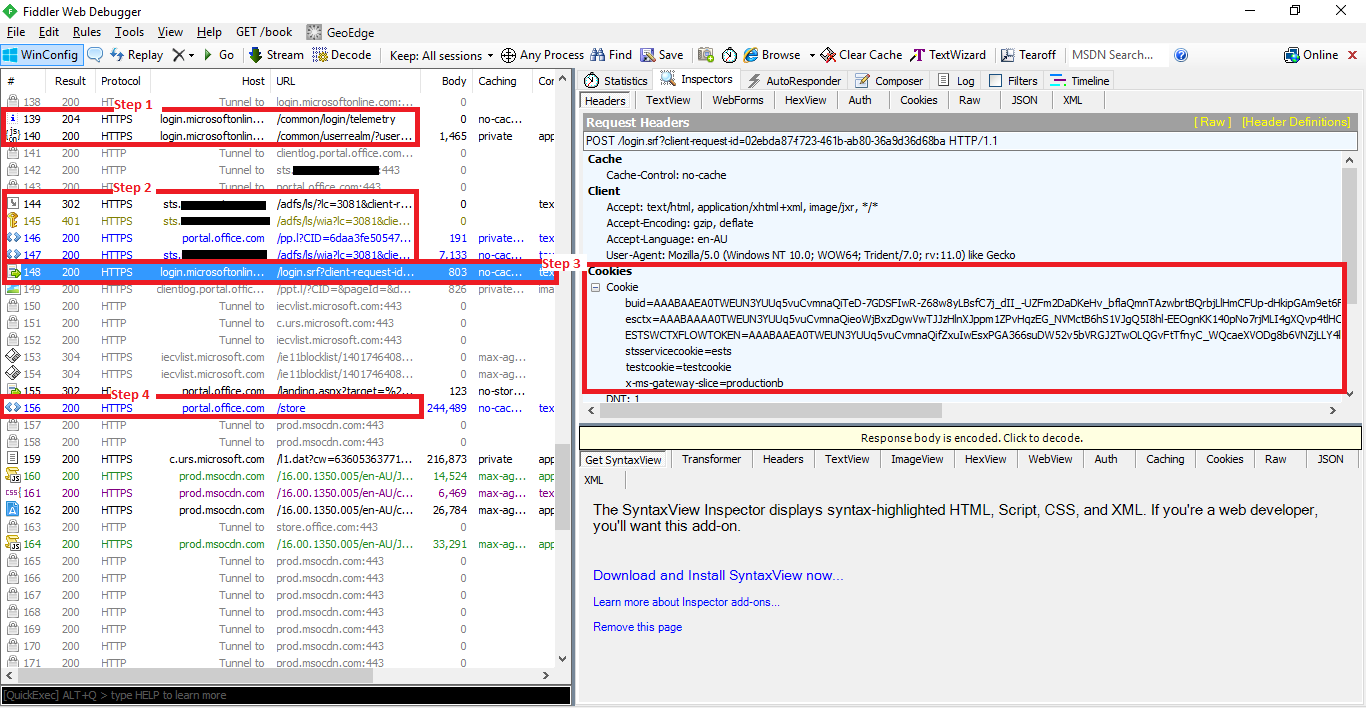
First, we confirmed the normal ADFS SSO components were working (highlighted in red)
- Connection to login.microsoftonline.com
- Redirection to our ADFS servers (sts.{domain}.com) against the WIA path
- Connection back to login.microsoftonline.com with the SAML token response
- Subsequent connection to portal.office.com/store which is what we’re trying to access
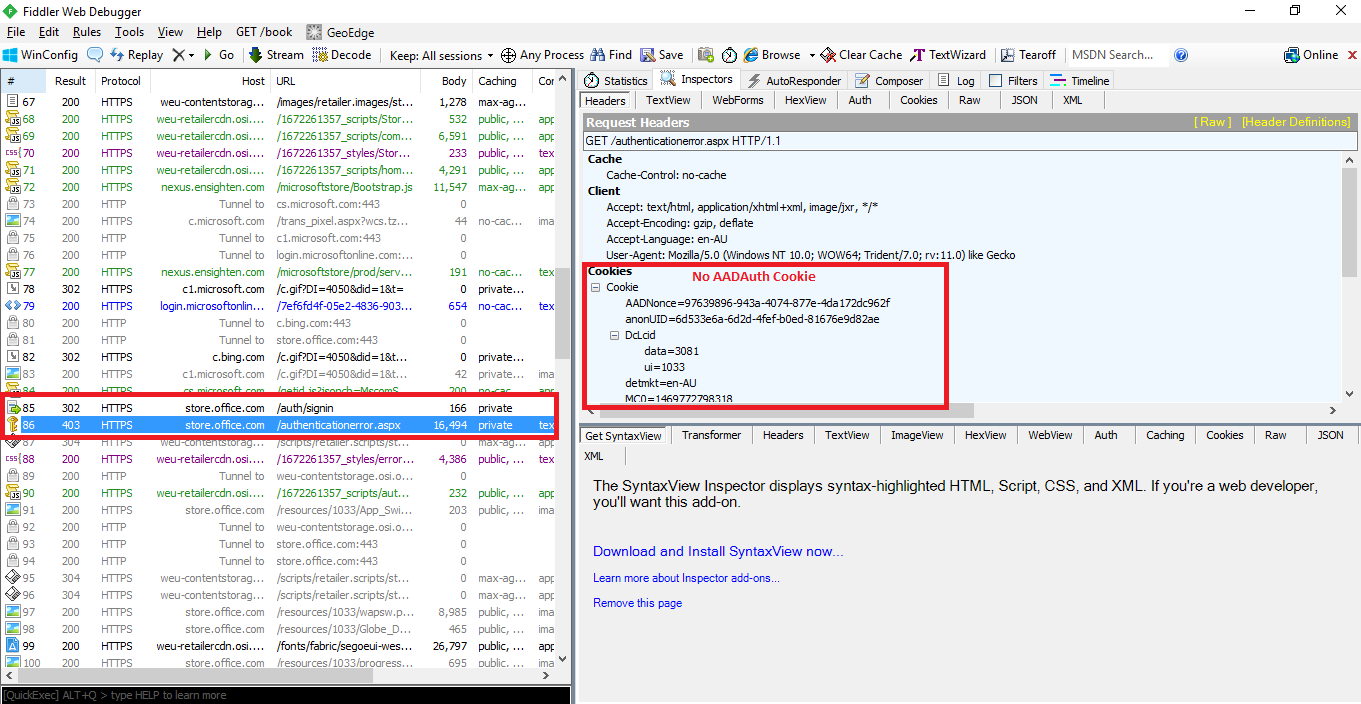
The cause of the looping however can be seen further down in the fiddler trace, shown here:
From this we can see what would be an unexpected connection to a different domain url, store.office.com, and looking at it we see an authentication error, and no auth cookies are being presented to it.
A quick inventory of the configuration on the client gave us the answer as to why. While the customer had done the common practice of including the key Office 365 URLs into their trusted sites (office365.com, outlook.com, sharepoint.com etc.), they did not include store.office.com. This in itself is not specifically a problem, BUT they also had ‘mixed’ mode set up where their ‘Internet Zone’ was set to run in Protected Mode, while their ‘Trusted Sites’ and ‘Intranet Zone’ were configured to have Protected Mode turned off.
For a bit of background around what IE Protected Mode is, refer to this article, but the short version is, Protected mode is a security feature in IE which ensures that sites run in an ‘isolated instance’. An effect of this isolation is that sites in protected mode cannot access the regular cookie cache.
As such, there was a ‘zone mismatch’ between the two, and what effectively was happening was:
- ADFS sign in was working as expected, and the user was successfully accessing portal.office.com resources and creating an auth cookie
- Portal.office.com/store however was actually loading content that was hosted under the site store.office.com
- store.office.com needed authentication credentials in order to correctly serve the content. But because it was not included in trusted sites, that content request was running in ‘protected mode’.
- Because of the isolation, it couldn’t see the valid auth token which was stored in the regular cookie cache, and so triggers an auth sign in request to login.microsoftonline.com to get one. And thus begins the endless authentication cycle.
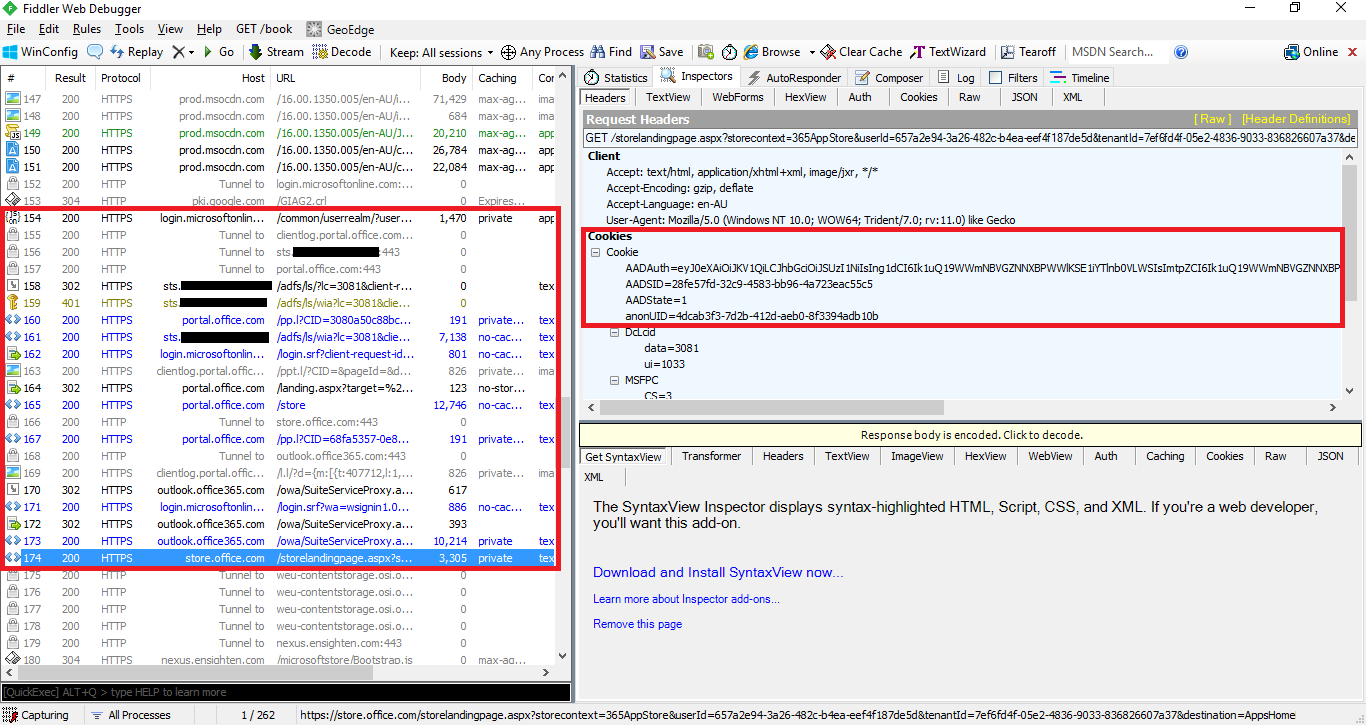
The simple fix for this was simply adding the *.office.com into the trusted sites zone to ensure that it did not execute in protected mode. Once we did it, we could see that when a connection to store.office.com is made, the appropriate auth token is presented and the page load works as expected:
Now, I’m not personally aware of a Microsoft guidance in terms of what should go into trusted sites for Office 365 functionality, but generally at Kloud we recommend the following to be used to avoid SSO issues:
- *.sharepoint.com
- *.office.com
- *.microsoftonline.com
- *.lync.com
- *.outlook.com
- URL of ADFS Server (e.g. sts.customerdomain.com)
Hopefully that gives you a bit of insight around the thinking, components and tools needed in debugging SSO issues with ADFS and Office 365!

Thank you very much! You just saved me at least a days worth of digging around.
Awesome, always glad to hear that these posts can help others!