Debugging an Office 365 ADFS/SSO issue when accessing Office Store in browser
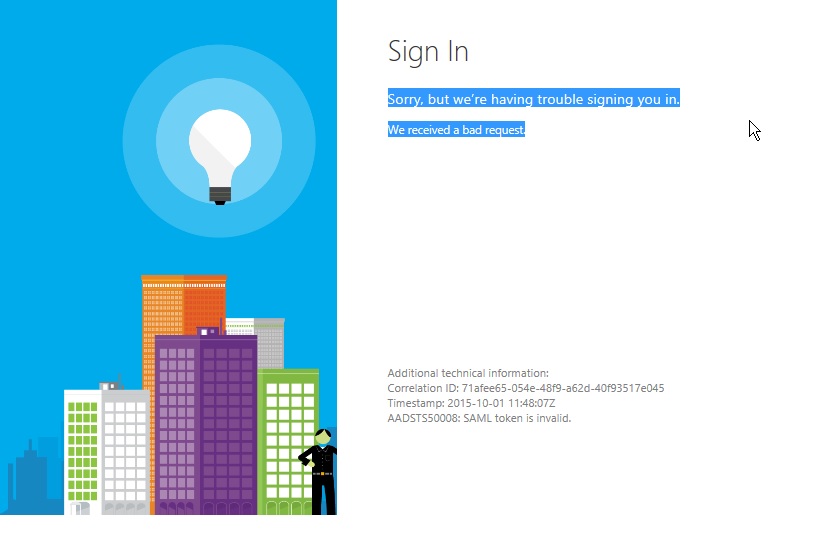
We recently came across an issue with a customer where they had configured a standard SSO experience with Office 365 using ADFS and it was working perfectly except for a specific use case. When a user accesses the office store via the Office 365 portal (e.g. portal.office.com/store) they got into an endless SSO login loop. Specfically, they would see the following:
- Connection to Portal.Office.com
- Redirection to login.microsoftonline.com
- Redirection to adfs.customerdomain.com (automatically signed in because of WIA SSO)
- Redirection to login.microsftonline.com