Azure AD Domain Services
I recently had what I thought was a rather unique requirement from a customer.
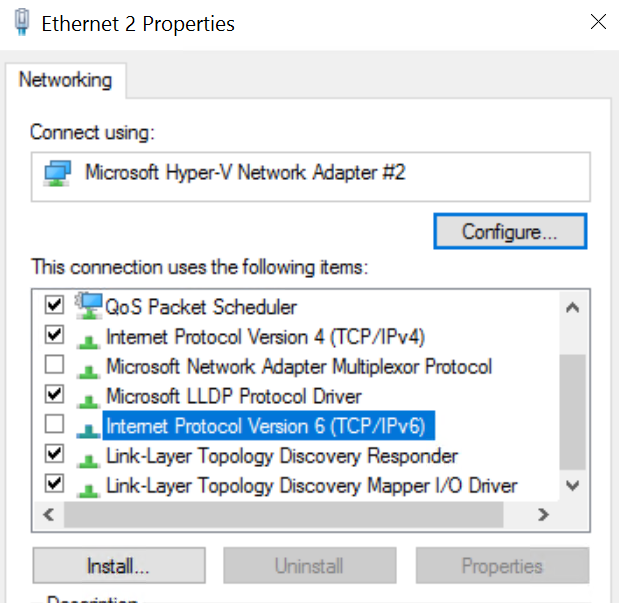
The requirement was to build Azure IaaS virtual machines and have them joined to a managed domain, while also being able to authenticate to the virtual machines using Azure AD credentials.
The answer is Azure AD Domain Services!
Azure AD Domain Services provides managed domain services such as domain join, group policy and Kerberos/NTLM authentication without the need for you to deploy and manage domain controllers in the cloud.… [Keep reading] “Azure AD Domain Services”