Microsoft as part of the uplift in Authentication Methods capability have extended the Graph API to contain User Azure MFA information. My customers have been requesting MFA User Reporting data for some time. How many users are registered for Azure MFA? What and how many methods are they registered with? The new Graph API functions provide this information and we no longer have to use the legacy MSOLUser PowerShell cmdlet to obtain the strongAuthenticationMethods information. The new API’s provide;
- self-service password reset and multi-factor authentication (MFA) information for all registered users
- how many users in your organization are registered for self-service password reset and multi-factor authentication capabilities
Azure MFA User Reporting Management Agent
With this new functionality exposed, I’ve built an Azure MFA Management Agent for Microsoft Identity Manager to consume information from the credentialRegistrationDetails API, which can then be used in Identity Workflows to trigger notifications to users that don’t have enough registered methods (e.g. if you require 2 MFA challenge methods for Azure Password Reset) or users aren’t registered for the Authenticator App.
The Management Agent brings in all the attributes that the credentialRegistrationDetails API provides and generates two additional attributes;
- hasAuthApp
- A boolean attribute indicating whether a user is registered with an Authenticator App (e.g Microsoft Authenticator)
- authMethodsCount
- A count of the number of methods a user is registered with in Azure MFA
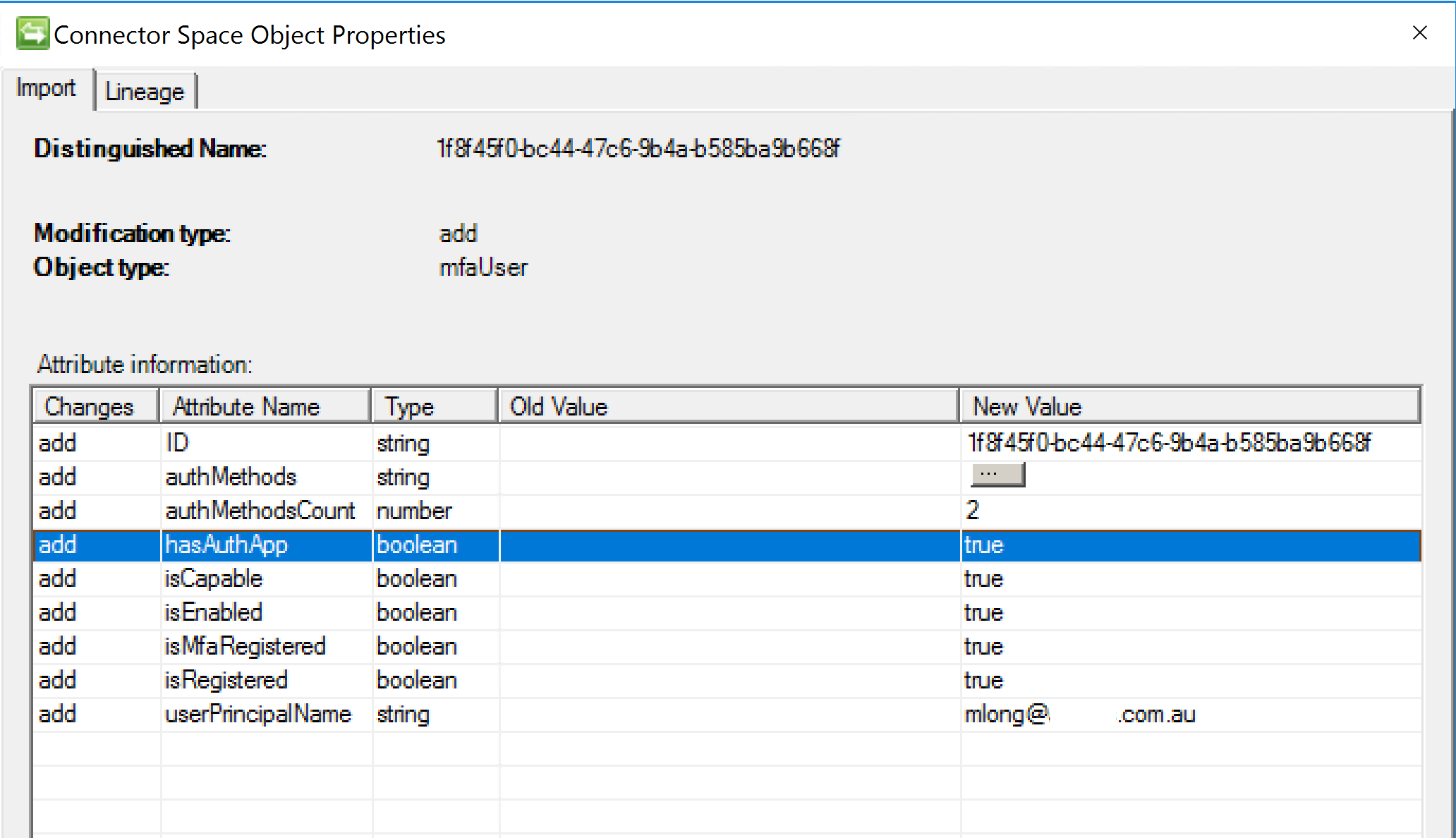
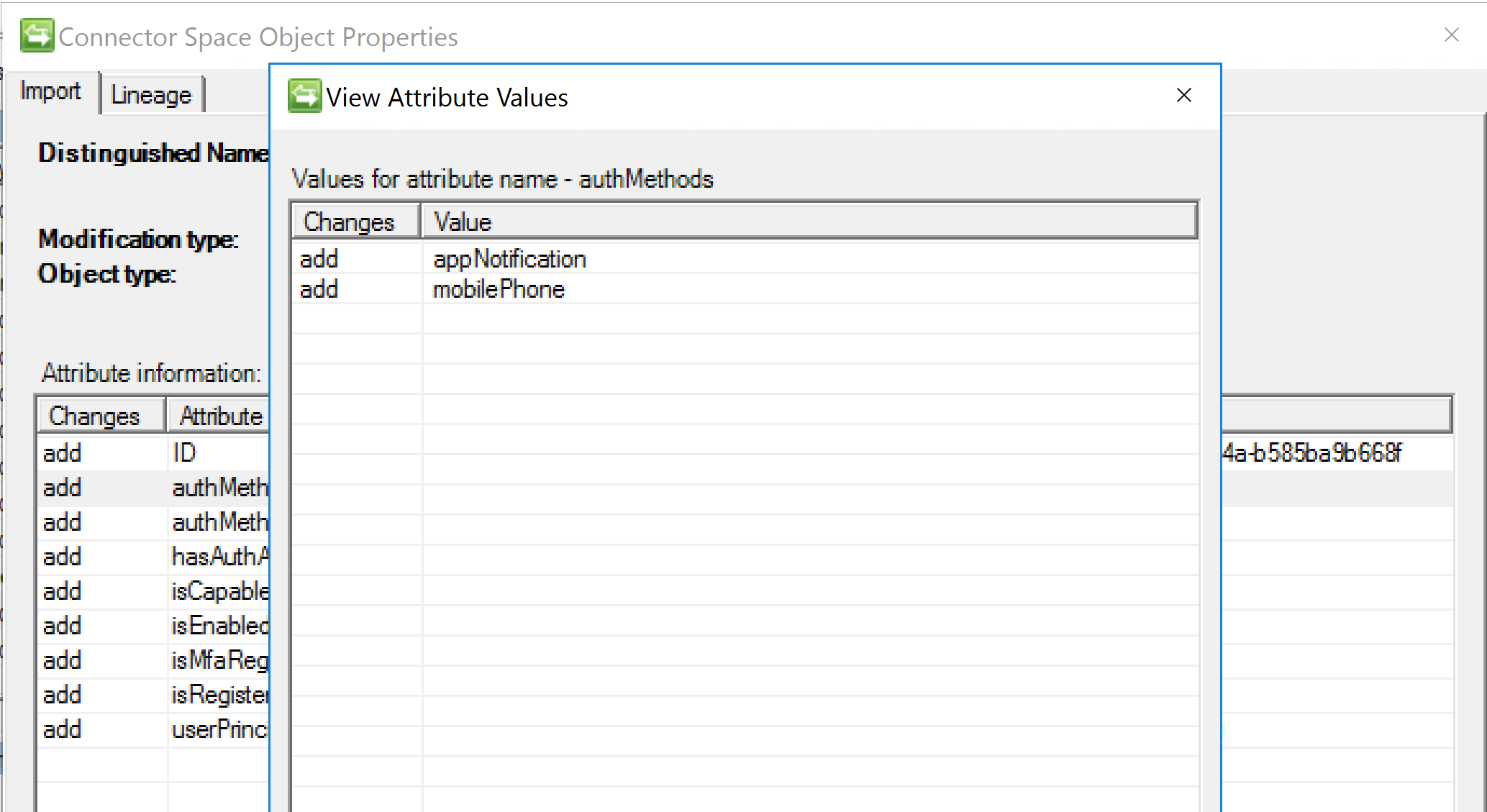
The authMethods is a multi-valued attribute in MIM as shown below.
Management Agent Capabilities
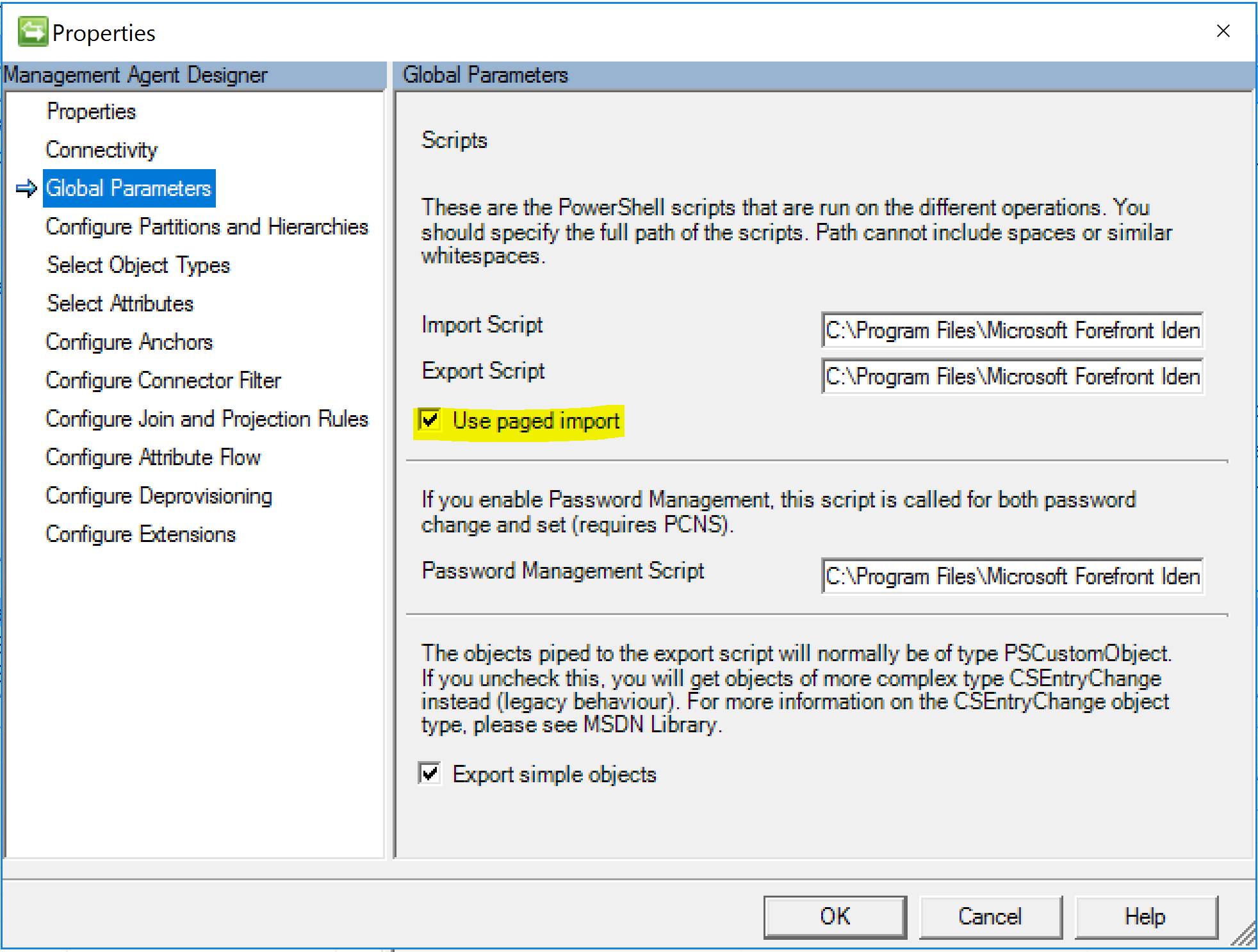
The MA will perform a Full Import each time. It uses the Granfeldt PowerShell Management Agent for which you can find more details about here. The Import script below is configured for Paged Imports based on the page size you configure in your Run Profile. Make sure you tick the Paged Imports option on the Global Parameters tab.
Schema Script
The schema script is below. It creates an ObjectType of mfaUser on the MA. The attributes are all the ones exposed via the API with the addition of the authMethodsCount and hasAuthApp generated attributes for use with reporting and MIM Set logic.
Import Script
The Import Script is a Full Sync each time with a filter to return users who are Registered for MFA. The query/filter is on line 128.
The script uses my oAuth authentication automation method detailed in this post. The Import script relies on an Azure AD Registered Application that has the Reports.Read.All permission. Update the script in line 29 and 30 for your registered Azure AD App ClientID and Secret.
For the first Authentication request (prior to using/running the MA) manually run the script and use the Get-AzureAuthN function (it is remarked out below for normal MA operation) to authenticate and authorise the application. Subsequent authentication events will use the stored refresh token (in my example below put in the C:\Program Files\Microsoft Forefront Identity Manager\2010\Synchronization Service\Extensions\AzureMFA path) to get a new access token using the Get-NewTokens function. Update references to C:\Program Files\Microsoft Forefront Identity Manager\2010\Synchronization Service\Extensions\AzureMFA if you create your MA in a different path.
Summary
We now have the information to report on who’s registered for Azure MFA and with what methods. We can use this to trigger notifications to prompt users to register additional methods, or add a specific method. Also we can use the summary information for MFA Enrolment reporting.
