
During December 2018 – February 2019 Microsoft have run an online Microsoft Graph Security Hackathon on Devpost.
The criteria of the hackathon was;
- Build or update a functioning Microsoft Graph-powered solution that leverages the Microsoft Graph Security API
Following the announcement of the Hackathon I was encouraged by Kloud management to enter. During the busy month of December I started to formulate a concept for entry in the Hackathon taking learnings from the hackathon I entered in 2018. Over the Xmas holiday period I started working on my entry which continued into January and February at nights and weekends.
Problem
A Security Administrator within an Organisation enables security related configuration options on an Azure Tenant to implement security controls that align an organisation with Microsoft recommendations and best practice.
The Azure Security Score provides an evaluation on the alignment of an organisation with best practice, however to some extent it still requires end users to have the right configuration for security related elements of their profile. But as a Service Desk Operator or Cyber Security Officer there isn’t a single view of a user’s security posture that can give you an individual user security score summary. My solution……
Microsoft User Security Evaluation Reporter (USER)
Microsoft User Security Evaluation Reporter (USER) is an Azure AD and Active Directory tool for use by the Service Desk and Cyber Security Officers to get instant visibility of an organisations Azure Security Score that allows them to then evaluate current risks within an organisation right down to individual users.
When the Microsoft USER loads the current Azure Security Score is retrieved, evaluated and displayed for alignment with Microsoft Recommendations. Also, on load the last 5 Active Security Risk Events are displayed.
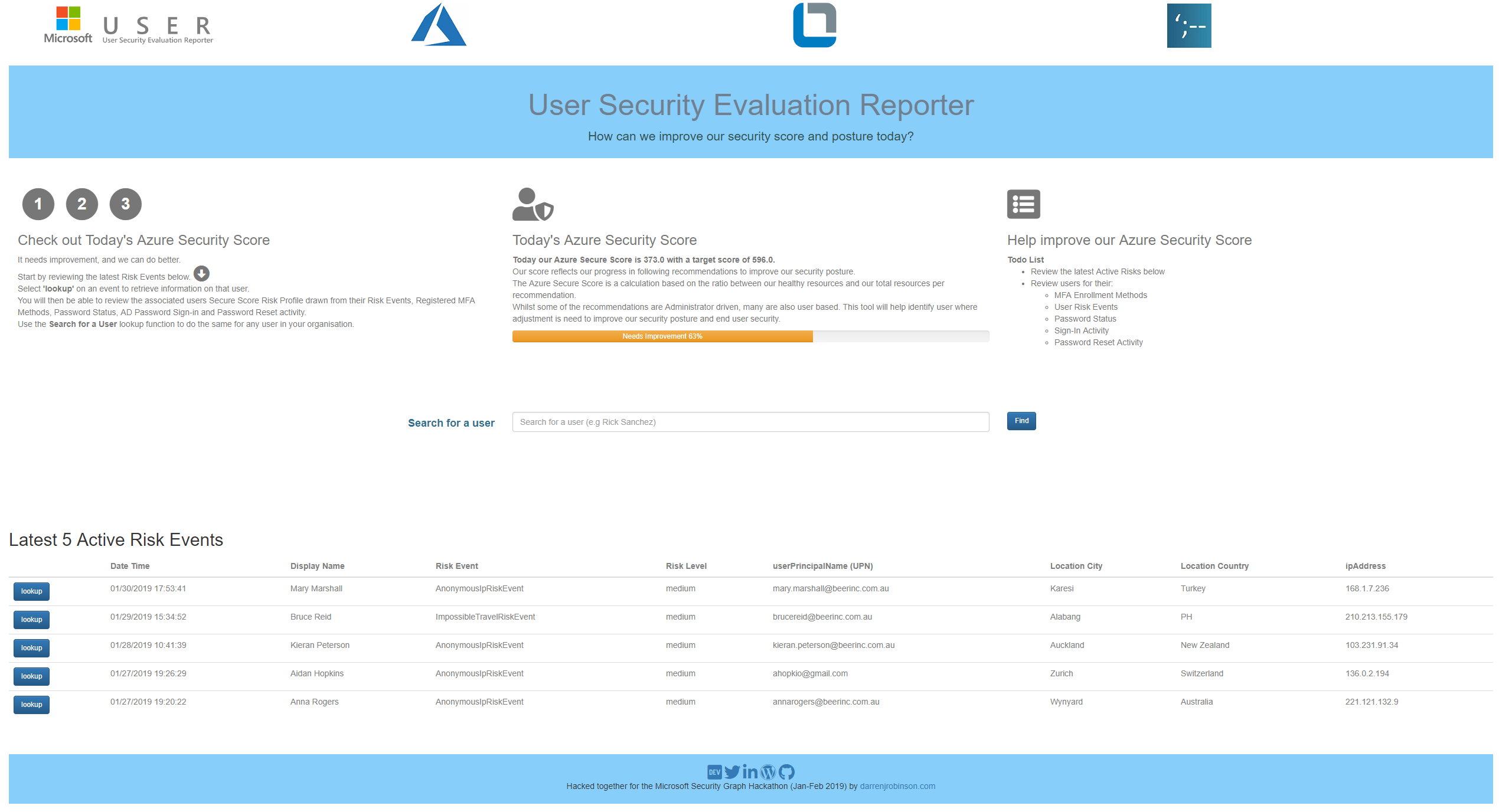
The Service Desk Operator or Cyber Security Officer can select one of the recent Security Events or search for a user and drill down into the associated identity. They will be quickly able to understand the users’ individual security posture aligned with best practice.
What are the recent Security Risk Events for that user? Does that user;
- Have MFA enabled? Is MFA enabled with an Authenticator App as the primary method?
- Is the users Active Directory password in the Pwned Passwords v4 list from Have I Been Pwned?
- Has the user recently being attempting Azure Password Reset functions?
- What are the last 10 logins for that user?
- What is the base user information for that user and what devices are registered to that user? Are they Azure AD Joined?
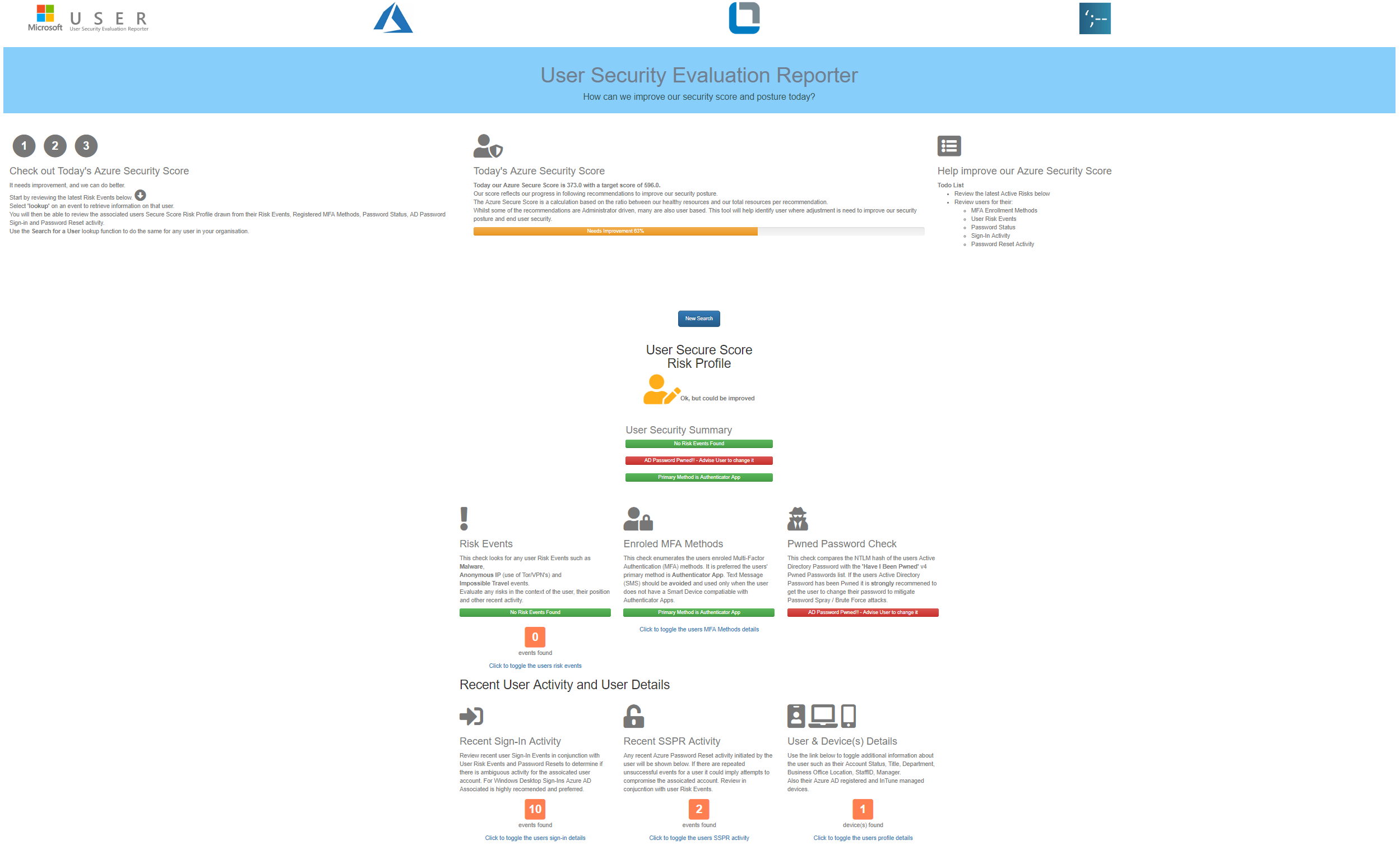
The clip below gives a walk through with more detail of my Microsoft USER tool.
How I built it
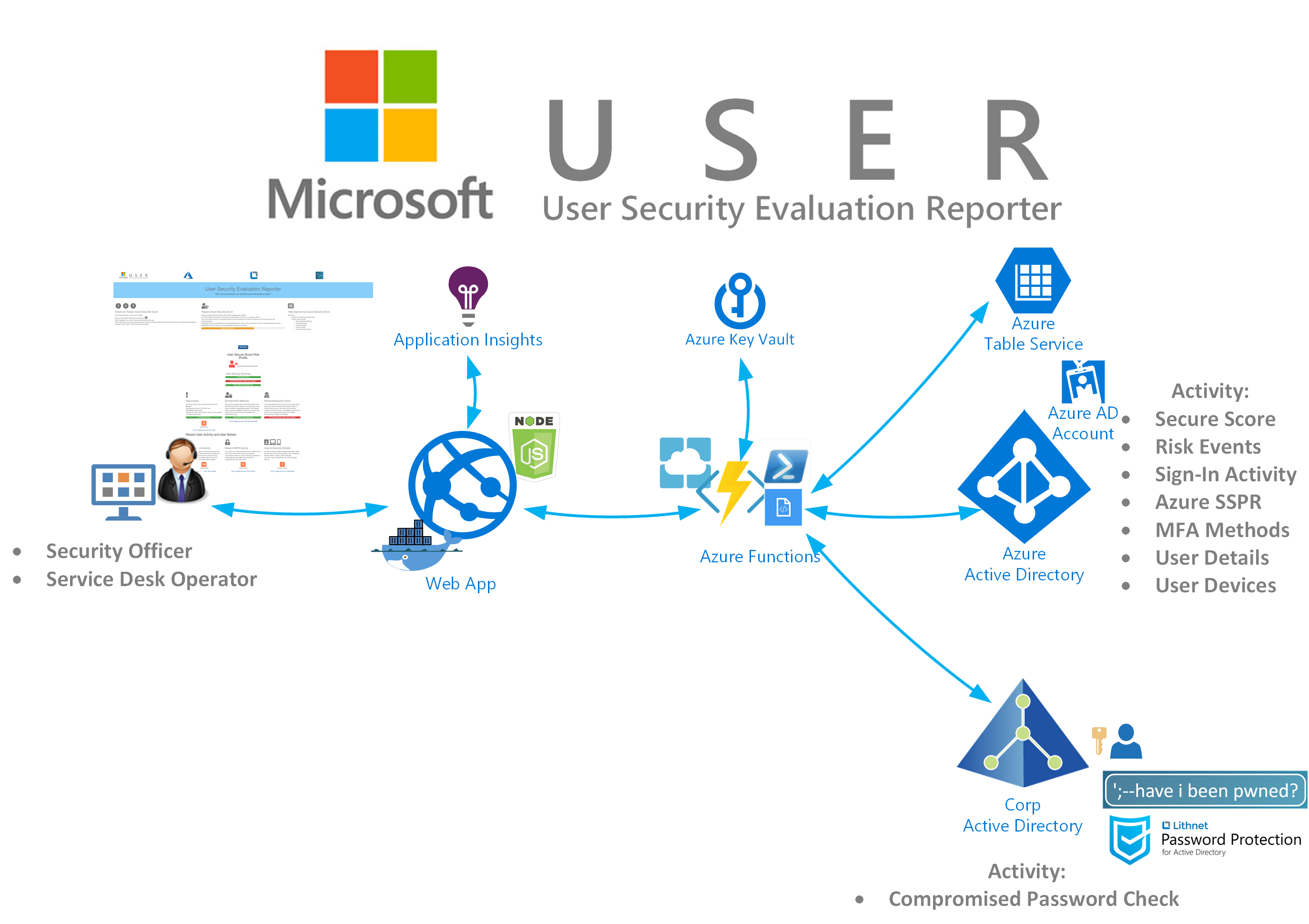
The solution is built using;
- NodeJS and Javascript
- leveraging Azure Functions to interface with Azure AD, Microsoft Graph, Azure Table Service
- Lithnet Password Protection for Active Directory that in turn leverages the Have I Been Pwned v4 dataset
- All secrets are stored in Azure Key Vault.
- The WebApp is Application Insights enabled.
- The WebApp is deployed using a Docker Container into Azure App Service
The architecture is shown below.
The Code
A Repo with the code can be found here. Keep in mind I’m not a developer and this is my first WebApp that was put together late at night and over weekends and only tested in Chrome and Edge. The Readme also contains hopefully everything you should need to deploy it.

Thanks Darren, looking forward to giving this a go!