As mentioned in my previous post, Using ADFS on-premises MFA with Azure AD Conditional Access, if you have implemented Azure AD Conditional Access to enforce MFA for all your Cloud Apps and you are using the SupportsMFA=true parameter to direct MFA execution to your ADFS on-premises MFA server you may have encountered what I call the ‘Double Auth’ prompt issue.
While this doesn’t happen across all Cloud Apps, you will see it on the odd occasion (in particular the Intune Company Portal and Azure AD Powershell Cmdlets) and it has the following symptoms:
- User signs into Azure AD App (e.g. Azure AD Powershell with Modern Auth support)
- User sees auth prompt, enters their username, which redirects to ADFS
- User enters credentials and clicks enter
- It looks like it signs in successfully but then ADFS reappears and the user is prompted to enter credentials again.
- After the second successful attempt, the user is then prompted for MFA as expected
Understanding the reason behind why this happens is reliant on two things:
- The background I provided in the blog post I referenced above, specifically that when SupportsMFA is being used, two requests to ADFS are sent by Azure AD instead of one as part of the authentication process when MFA is involved.
- Configuration and behaviour of the prompt=login behaviour of Azure AD, which is discussed in this Microsoft Docs article.
So to delve into this, let’s crack out our trusty Fiddler tool to look at what’s happening:
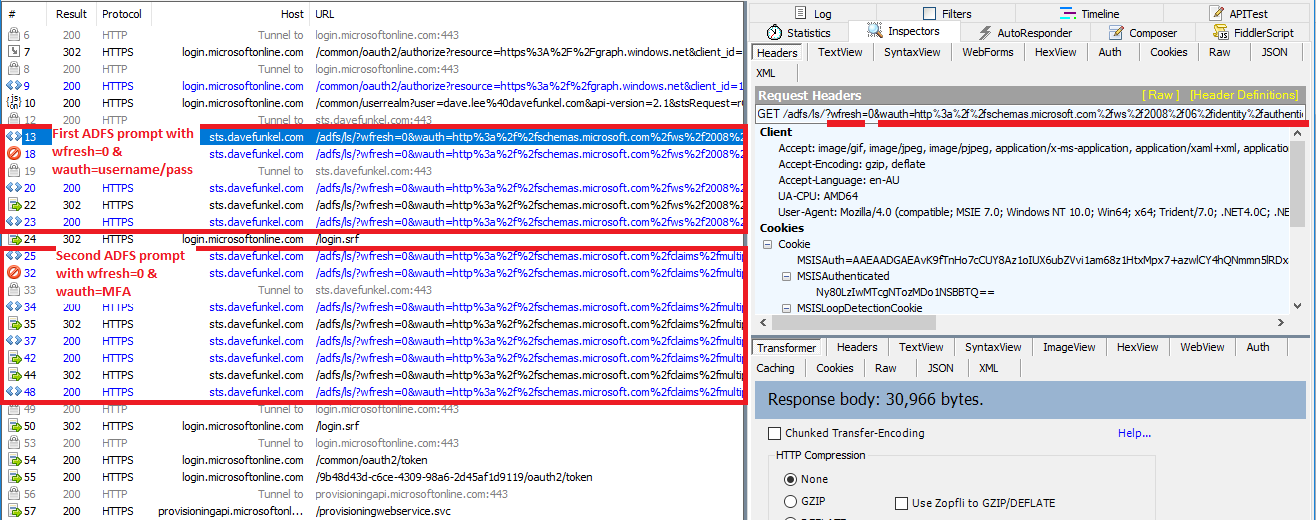
Highlighted in the image above is the culprit. You’ll see in the request strings that the user is being sent to ADFS with two key parameters wauth=… and wfresh=0. What is happening here is that this particular Azure AD application has decided that as part of sign in, they want to ensure that ‘fresh credentials’ are being provided (say, to ensure the correct user creds are used). They do this by telling Azure AD to generate a request with prompt=login, however as noted in the article referenced, because some legacy ADFS systems don’t understand this ‘modern’ parameter, the default behaviour is for Azure AD to pre-emptively translate this request into two ‘WS-Fed’ parameters that they can understand. In particular, wfresh=0 as per the WS-Fed specs means:
… If specified as “0” it indicates a request for the IP/STS to re-prompt the user for authentication before issuing the token….
The problem of course is that ADFS sees the wfresh=0 parameter in both requests and will abide by that behaviour by prompting the user for credentials each time!
So, the fix for this is fairly simple and is in fact (very vaguely) called out in the technet article I’ve referenced above – which is to ensure that Azure AD uses the NativeSupport configuration so that it sends the parameter as-is to ADFS to interpret instead of pre-emptively translating it.
The specific command to run is:
Set-MsolDomainFederationSettings –DomainName yourFederatedDomain.com -PromptLoginBehavior NativeSupport
The prerequisite to this fix is to ensure that you are either running:
- ADFS 2016
- ADFS 2012 R2 with the July 2016 update rollup
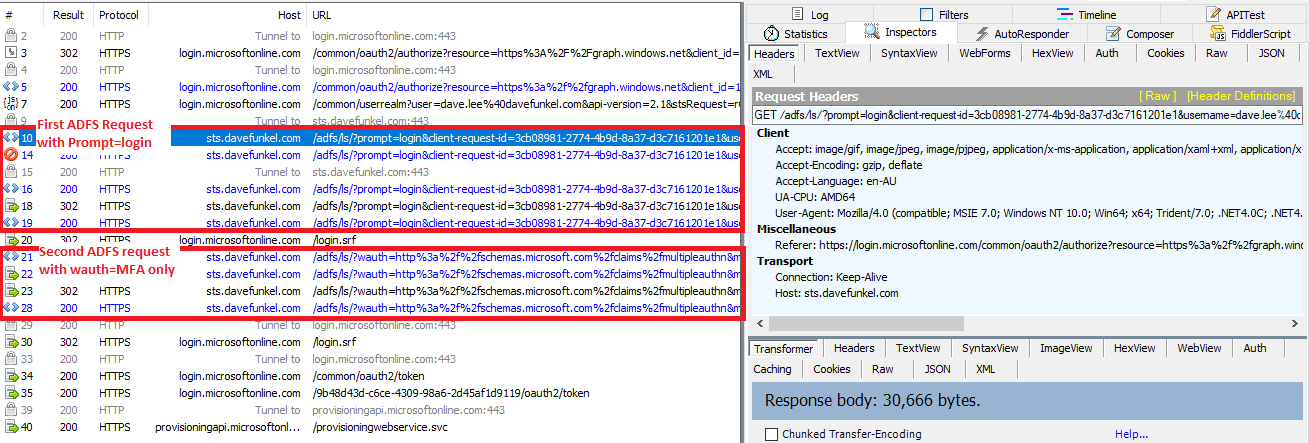
Once this update is applied (remember that these DomainFederationSettings changes can take up to 15-30 mins) you’ll be able to see the difference via Fiddler – ADFS is sent with a prompt=login parameter instead and its only for the first request so the overall experience is the credential prompt only occurs once.
Hope that saves a few hairs for anyone out there who’s come across this issue!
[UPDATE 12/09/17] Looks like there’s a Microsoft KB article around this issue now! Helpful for those who need official references: https://support.microsoft.com/en-us/help/4037806/federated-users-in-azure-active-directory-may-have-to-sign-in-two-time

Great write-up! Thanks for the heads up.
Really great post thanks explaining the issue. I’m running ADFS 2016 with cert MFA integrated with Azure. I tried setting it to nativesuppprt but still get the dreaded multi login prompt. My MFA is set to “false” as I use a mix of certs for some users and standard Office365 MFA for others. Anything else I need to check that you know of? The issue is exactly as you described above – 2 logins before MFA prompt, and finally you can authenticate fine.