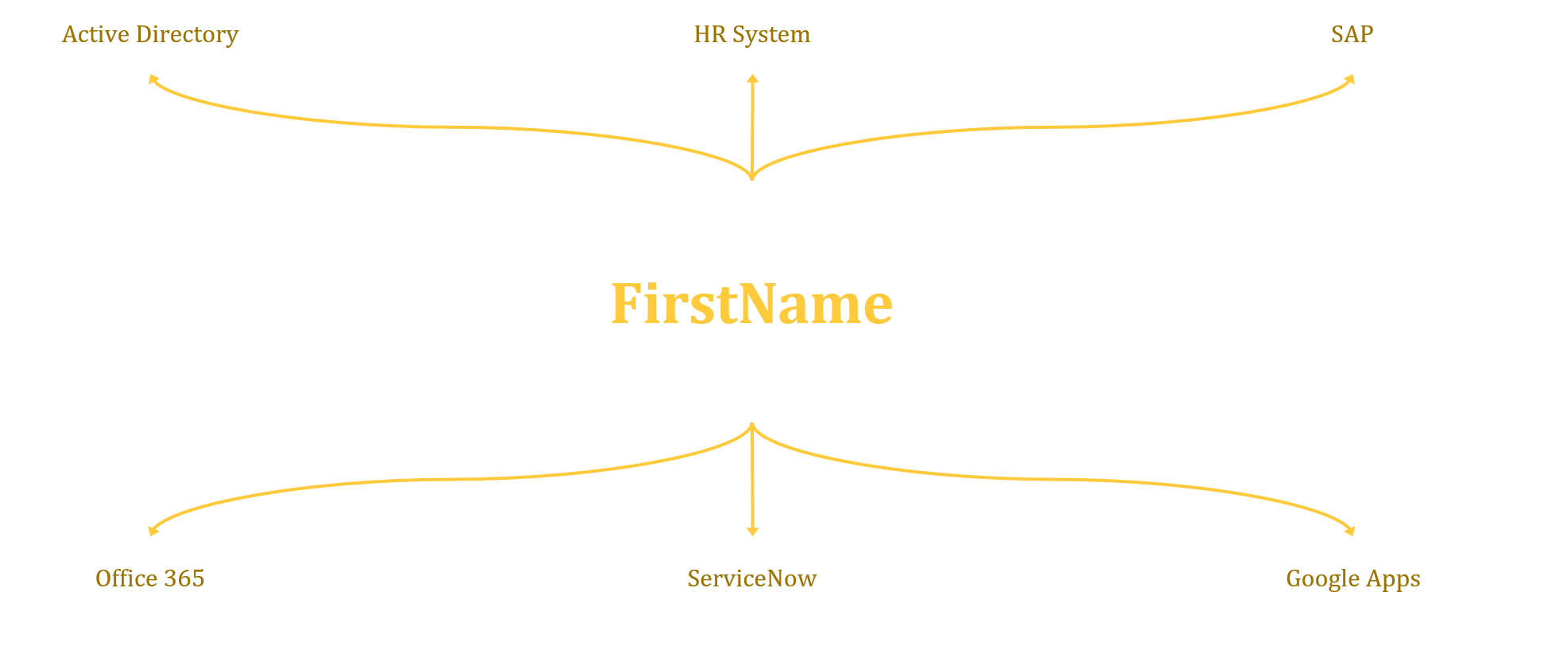
Defining IT Strategy
Information Technology (IT) Strategy is a comprehensive plan that outlines how technology should be used to meet IT and business goals.
The following approach can be used to define your organisation’s IT Strategy.
Inputs:
- Organisational Business Priorities
- Organisational Key Behaviours
- How Business will be Supported by IT
- Technology Influences
- IT Strategic Principles
- IT Service Management Operating Principles
First of all, in order to define an IT Strategy, we need to obtain the above inputs (as much as possible).… [Keep reading] “Defining IT Strategy”