Still in many Organization hard coded credentials are stored in Application config files for making application-to-application connection, in scripts (ex: scheduled tasks) and config files. Generally, these are high privileged service accounts and its passwords are set to be never changed.
Keeping hard coded credentials always risk to the organizations security posture. CyberArk provides a solution called Application Identity Manager using which, the passwords of Privileged Service Accounts can be stored centrally in Password Vault, logged, rotated and retrieved in many different ways.
CyberArk supports two approaches to eliminate hard-coded credentials, which are;
- Credentials Provider (CP). This required an agent needs to be installed on each server where the application or script is running.
- Central Credential Provider (CCP).
In this post I’m giving more details on how to retrieve credentials via CCP using Java REST API call. Applications that require credentials to access a remote device or to execute another application remotely can request the relevant credentials from the CCP via REST or SOAP calls.
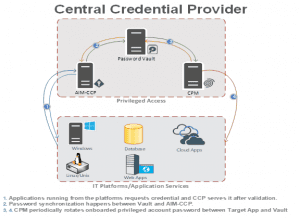
Pre-Requisites:The CCP installation consist of two parts, which are;
1) Credential Provider for Windows ( 2012 R2, 2016)
2) Install the Central Credential Provider web service (IIS 6, 7.5, or 10)
Client Requirements:
The Central Credential Provider works with applications on any operating system, platform or framework that can invoke REST or SOAP web service requests.
CCP Supported Client Authentication:
1) Client certificates
2) The address of the machine where the application is running
3) Windows domain Operating System user
Overview
In this example I’ve used Java to make REST API call to CCP Web Services using Certificate and Client IP authentication. This approach will work with any programming languages like .Net, Python, PowerShell etc.
1. On board Required Application into CyberArk via Password Vault Web Access (PVWA) Web Portal.
2. Create Required Platform and Safe.
3. On-board Required Privileged Service Account into CyberArk via PVWA
4. Add Application we have created in step1 as the member of this Safe with Retrieve permission enabled
5. Add Provider Users as a member to the Safe, which was created as part of CCP initial installations.
6. Add the Certificate into CCP’s IIS server, the same certificate will be used for client authentication
7. Add the certificate into java keys store using Java key tool command
8. Run the java Code.
Implementations:
On-board Application => Login to PVWA =>Go to Application Tab =>Add Application : provide Application name, Owner and other details. Go to Allowed machine Tab=> Enter the IP Address of the machine where the java code is running. I’ve also added time restriction which ensures credentials will be released only within the time limit after the successful authentication.
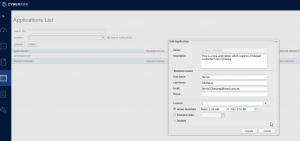
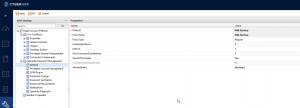
Create Platform and Safe: Login to PVWA =>Go to Administration=>Platform Management => Select Windows Domain Accounts => Duplicate it and modify according to the Password requirements.
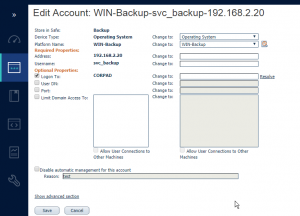
On-board Account and Add Members: Login to PVWA =>Go to Accounts => Account View => Add Account => Enter the actual Privileged Account details by selecting the Safe and Platform we have created in the previous steps. In this example I’ve chosen AD as my target account but we can any platform accounts as per the need since CyberArk support all most all of the platforms.
Add Application as a Safe Member: Login to PVWA =>Go to Policies =>Access Control =>Select the Safe=> Edit members => Add Application as member with Retrieve permissions and Add Provider user with Retrieve and List permissions
Add Certificate into IIS Server: Either we can use Self Signed or CA Signed client Certificate. I’ve added a signed AD Domain certificate for PVWA SSL connection, so I’m going to use the same certificate into my Client Java code. To add Certificate into Java key Store: I’ve java installed in my client machine (192.168.2.41) where my java code will run to make REST API calls. The below key tool command must be executed via CMD.
keytool -importcert -storepass changeit -keystore "C:\Program Files\Java\jdk1.8.0_181\jre\lib\security\cacerts" -alias compsrv01 -file certnew.cer
Java Code:
Note : if you look at the java code there is no hard coded credentials or tokens used to authenticate into CCP, Its simply uses the certificate for authentication.
Java Output:
The outcome of the above REST API call will be a JSON and we can get the user name, password (content) from it. These credentials will be dynamically referred in the target scripts, applications which will then use the credentials to perform its tasks.
![]()
