DR Failover for Skype for Business Standard Edition
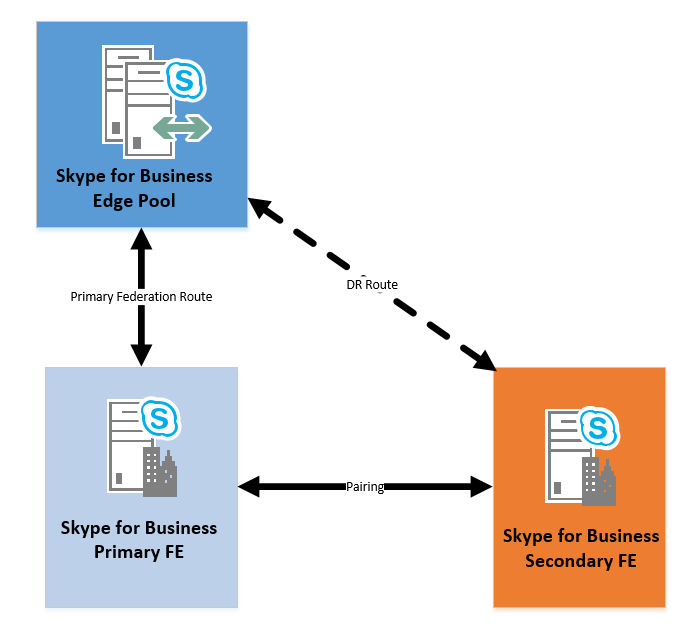
The article takes you through step by step of carrying out both health check and invoking disaster recovery (DR) a standard edition environment. The diagram below shows the layout of the environment where the DR was carried out on:
Before proceeding to test DR you need to make sure the appropriate registrar information is available/configured in the environment otherwise you will get the following error during Pool Failover process:
Please check that the pool <Prod_S4B> is healthy as conditions such as high CPU, low available memory
or any disabled services can delay (or in some cases result in unsuccessful) fail over operations.… [Keep reading] “DR Failover for Skype for Business Standard Edition”
