Send mail to Office 365 via an Exchange Server hosted in Azure
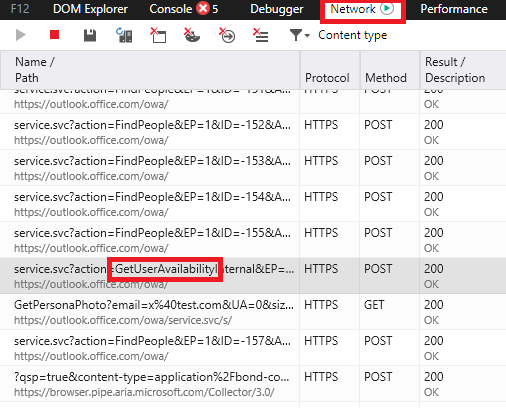
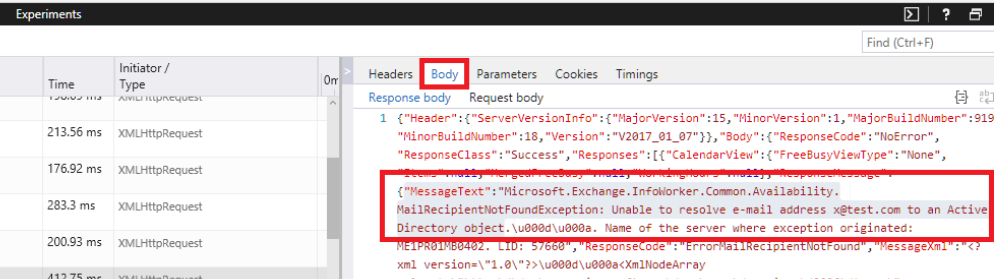
Those of you who have attempted to send mail to Office 365 from Azure know that sending outbound mail directly from an email server hosted in Azure is not supported due to elastic nature of public cloud service IPs and the potential for abuse. Therefore, the Azure IP address blocks are added to public block lists with no exceptions to this policy.
To be able to send mail from an Azure hosted email server to Office 365 you to need to send mail via a SMTP relay.… [Keep reading] “Send mail to Office 365 via an Exchange Server hosted in Azure”