Automating Azure Instrumentation and Monitoring – Part 3: Custom Metrics
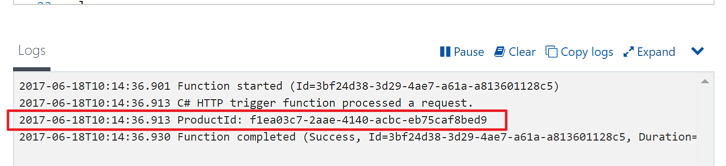
One of the core data types that Azure Monitor works with is metrics – numerical pieces of data that represent the state of an Azure resource or of an application component at a specific point in time. Azure publishes built-in metrics for almost all Azure services, and these metrics are available for querying interactively as well as for use within alerts and other systems. In addition to the Azure-published metrics, we can also publish our own custom metrics.… [Keep reading] “Automating Azure Instrumentation and Monitoring – Part 3: Custom Metrics”