
27 Nov 18 Part 3 is available here that details customizing an image and accessing it via other SSH clients with elevated access.
In Part-1 of this series posted yesterday I showed that with Windows 10/Windows Server 2019 we can now have isolated virtual environments for PowerShell Desktop in Azure through containerization.
In this post I’ll show how I plan to leverage this capability from a mobility perspective. What we need to do first is enable elevated (privileged) access to our VM. My Client will be Azure Cloud Shell. My target/host is the Windows 10 1809 Virtual Machine I deployed in the last post.
Enabling SSH Key Based Privileged Authentication to our Windows 10 VM
To setup Key Based Access (over password access, which is required for elevated access) we need to configure the SSH Server and our Client.
SSH Server
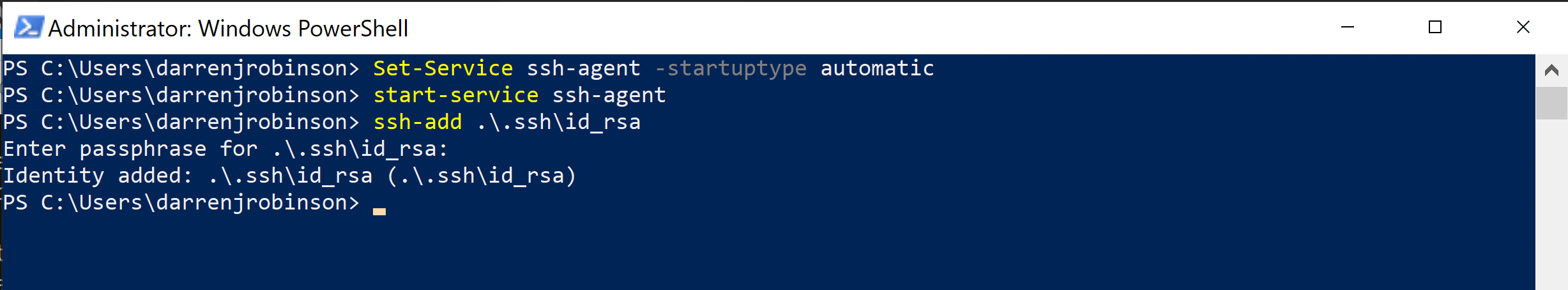
On the Windows 10 Azure VM where we installed OpenSSH as per the first post here, we need to start the SSH-Agent. By default it is set to Disabled. Change the Startup Type, Start it and test it by adding the local user to the Agent. Using an elevated PowerShell session on the Azure Windows VM run;
Set-Service ssh-agent -startupType automatic Start-Service ssh-agent cd ~\ ssh-add .\.ssh\id_rsa
SSH Client
As I’m using Azure Cloud Shell as my client, I started a Cloud Shell Session in my browser.
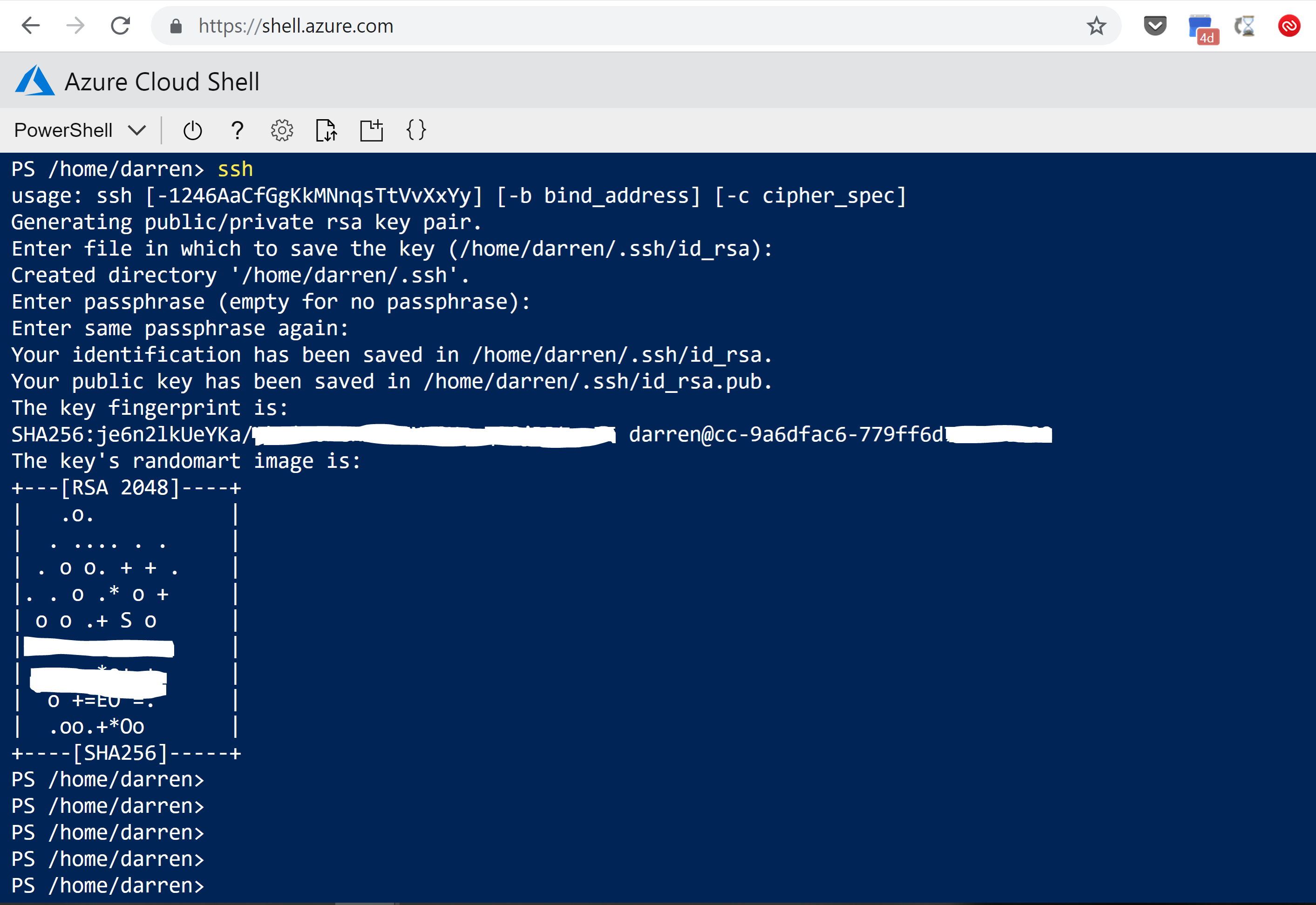
- In Azure Cloud Shell generate a SSH Key using SSH-Keygen
- Remember your passphrase as this will be required for accessing the Windows 10 Azure VM
- Copy the key to the Windows 10 Azure VM
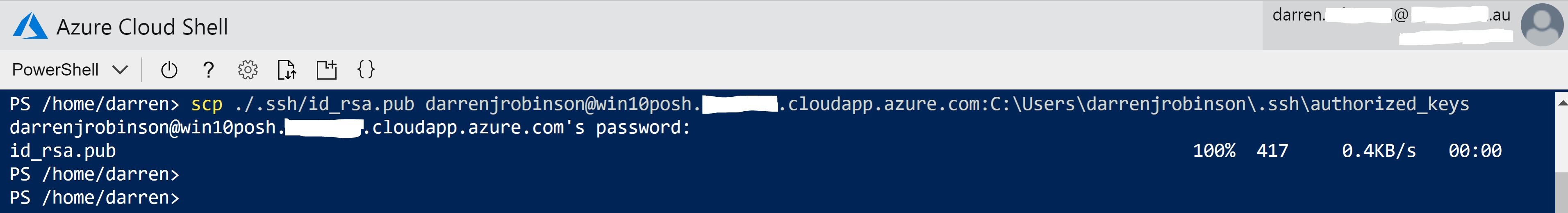
- Run the command below (after changing it for your username and Windows VM IP Address) and provide your password to copy up the file
cd ~/ scp ./.ssh/id_rsa.pub username@Win10ServerIPAddress:C:\Users\userprofilename\.ssh\authorized_keys\
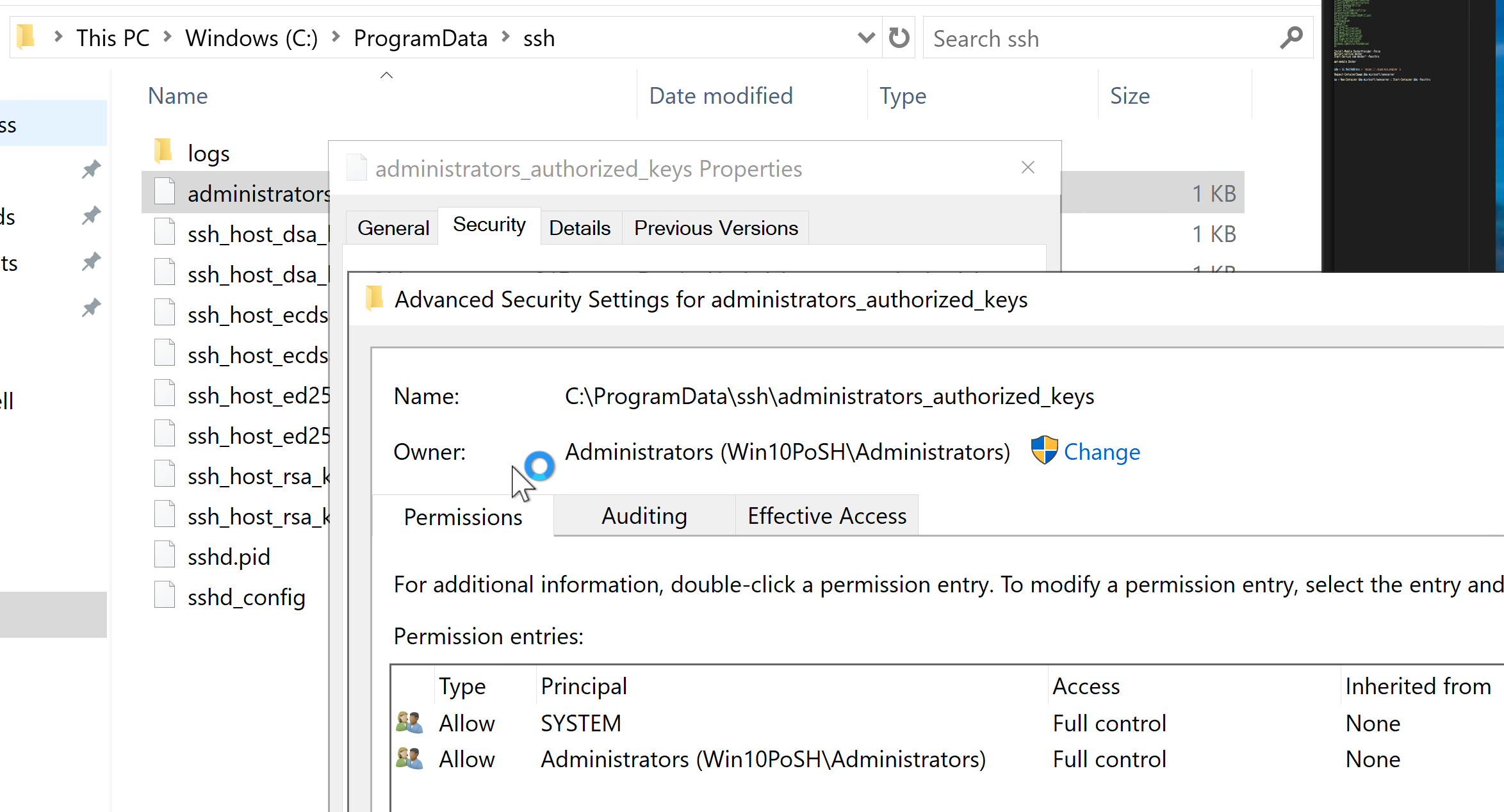
- On the Server if C:\ProgramData\ssh\administrators_authorized_keys exists add your Public key that you copied into your home folder above into it. If C:\ProgramData\ssh\administrators_authorized_keys doesn’t exist then copy the authorized_keys file from your .ssh home directory (e.g c:\users\darrenjrobinson\.ssh ) to C:\ProgramData\ssh\administrators_authorized_keys
- Edit the permission on the administrators_authorized_keys file.
- Right-Click the file => Properties => Security => Advanced => Disable Inheritance => Choose “Convert inherited permissions into explicit permissions on this object”
- Remove Authenticated Users so that only System and Administrators remain as per the screen shot below. Then select Apply and then OK.
Testing SSH with Key Access
From our Azure Cloud Shell SSH to your Windows 10 Host;
ssh username@ipaddress
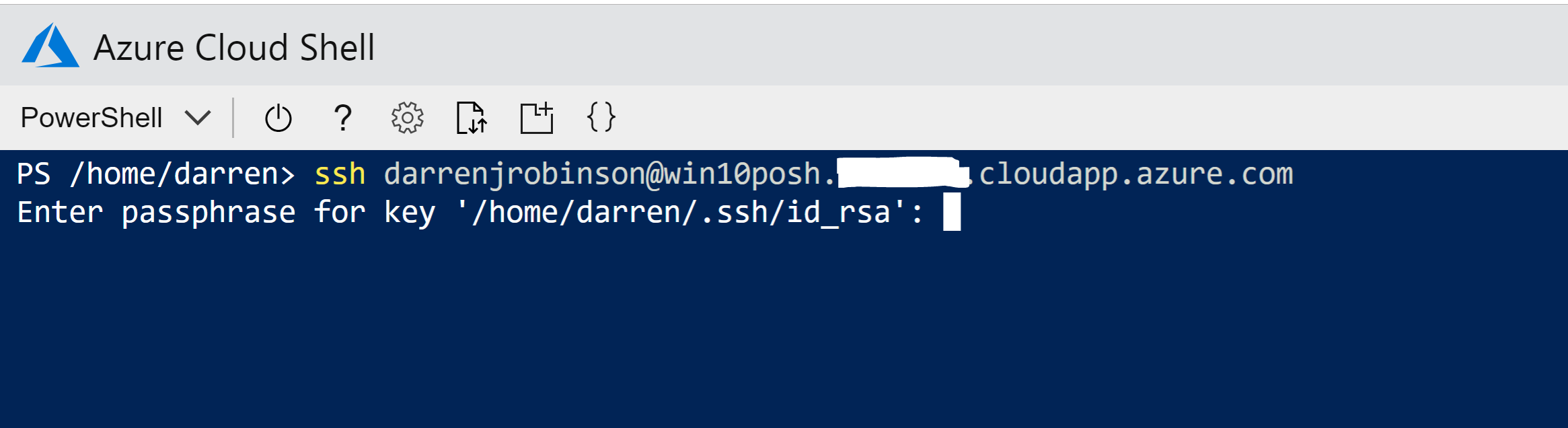
You will be prompted for the passphrase you gave when you generated the SSH key. Enter that and you will be authenticated using SSH to the Windows 10 VM.
Docker Access from Azure Cloud Shell in Browser
Now that we have Privileged Access to our Windows 10 VM, let’s try running a Windows 10 1809 Container and executing a PowerShell command to query the version of PowerShell available.
docker run -it mcr.microsoft.com/windows:1809 powershell $psversiontable
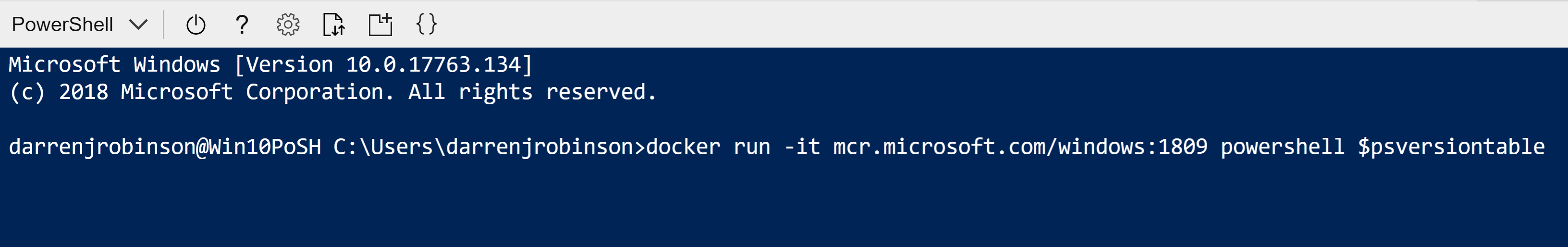
Wait a few seconds (maybe longer depending on the spec of your VM) and
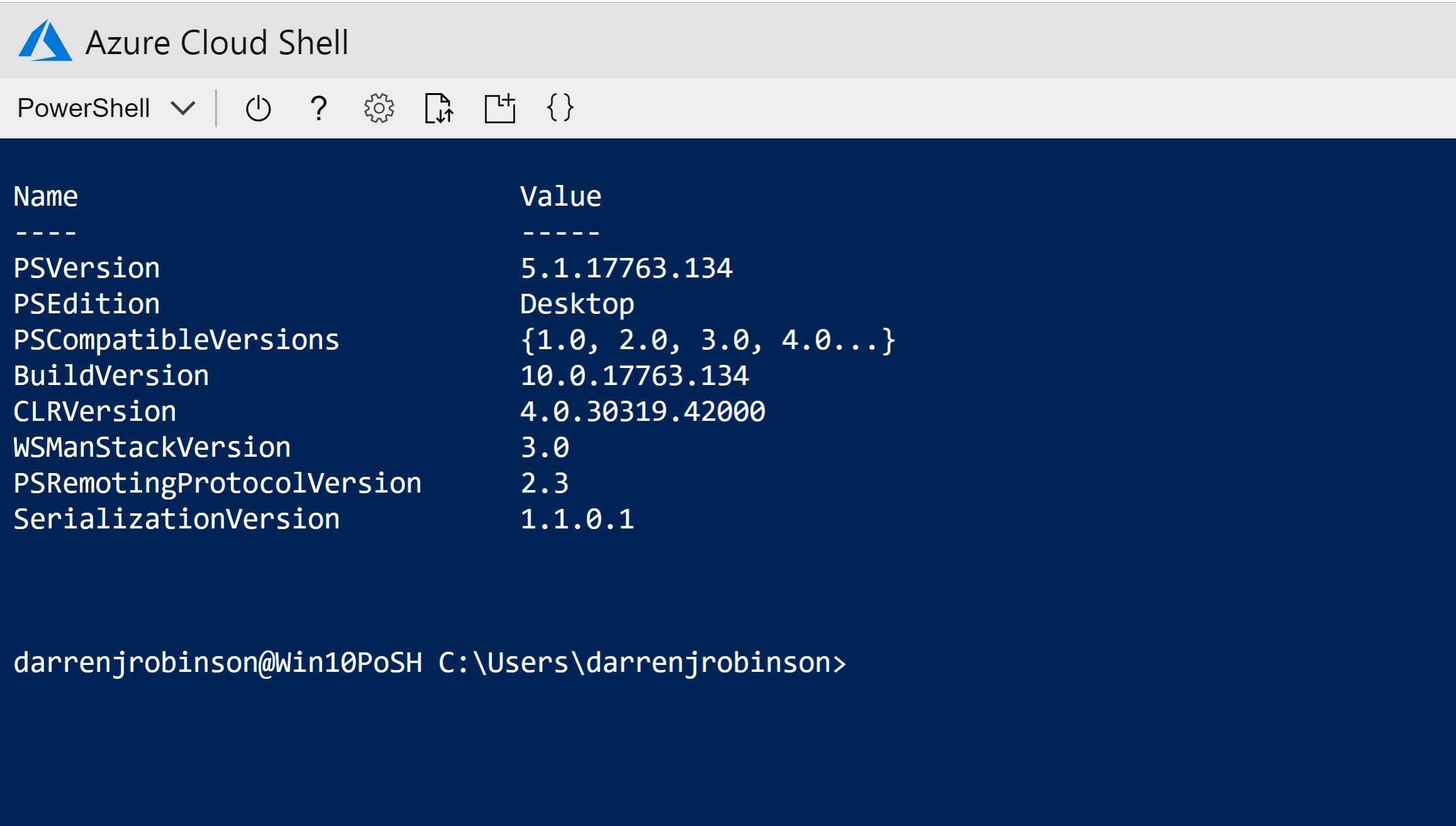
Fantastic, we have a Container with PowerShell Desktop that we have accessed via Cloud Shell in a Browser.
Docker Access from Azure Cloud Shell in iOS Azure App
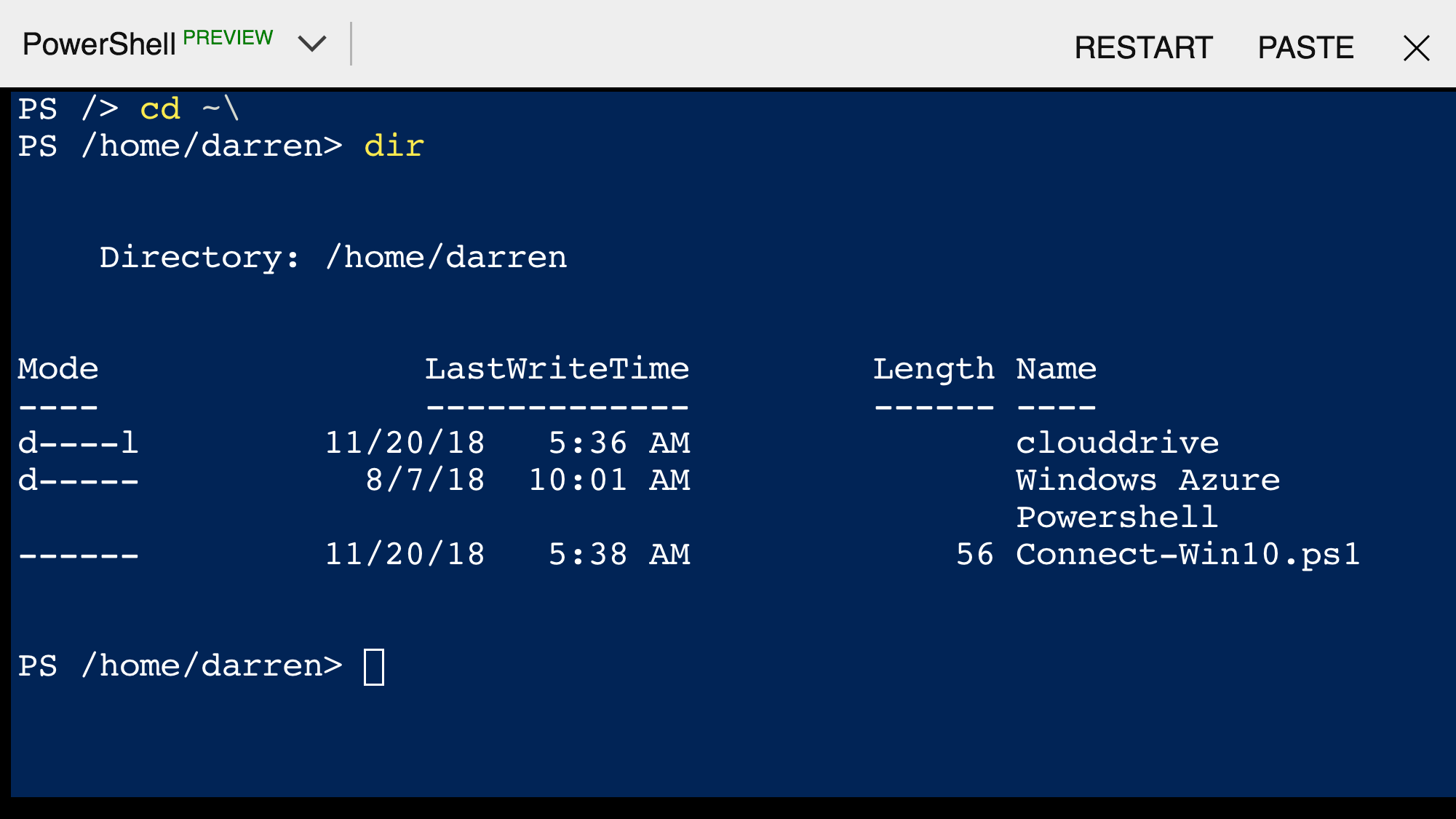
Using the Azure iOS App on my iPhone I started a Cloud Shell session and changed to my home directory cd ~\ where I had put a file named Connect-Win10.ps1 which contains
ssh username@ipaddressOfWin10Host
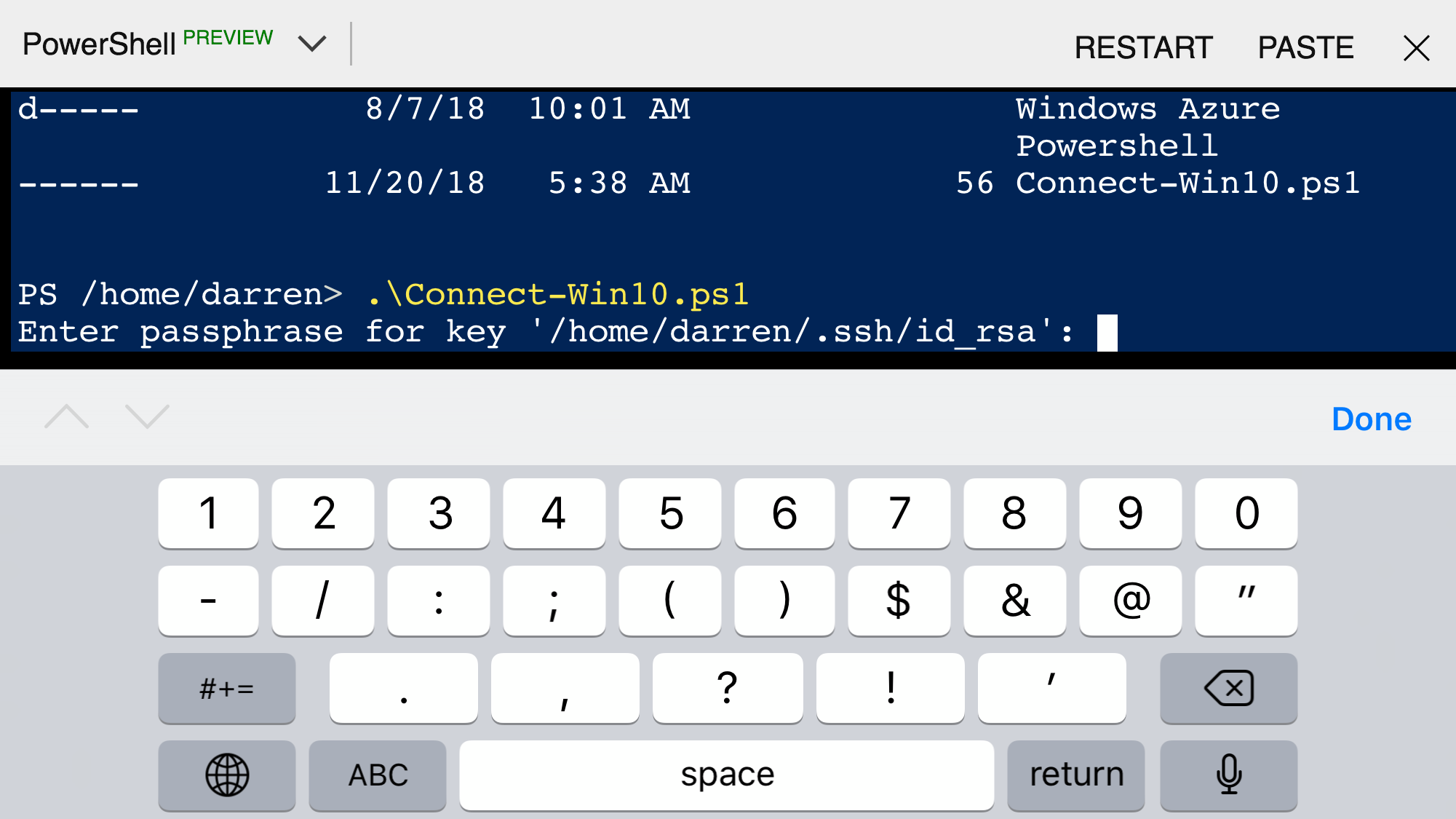
I executed it and it prompted me for the passphrase for my SSH Key which I entered
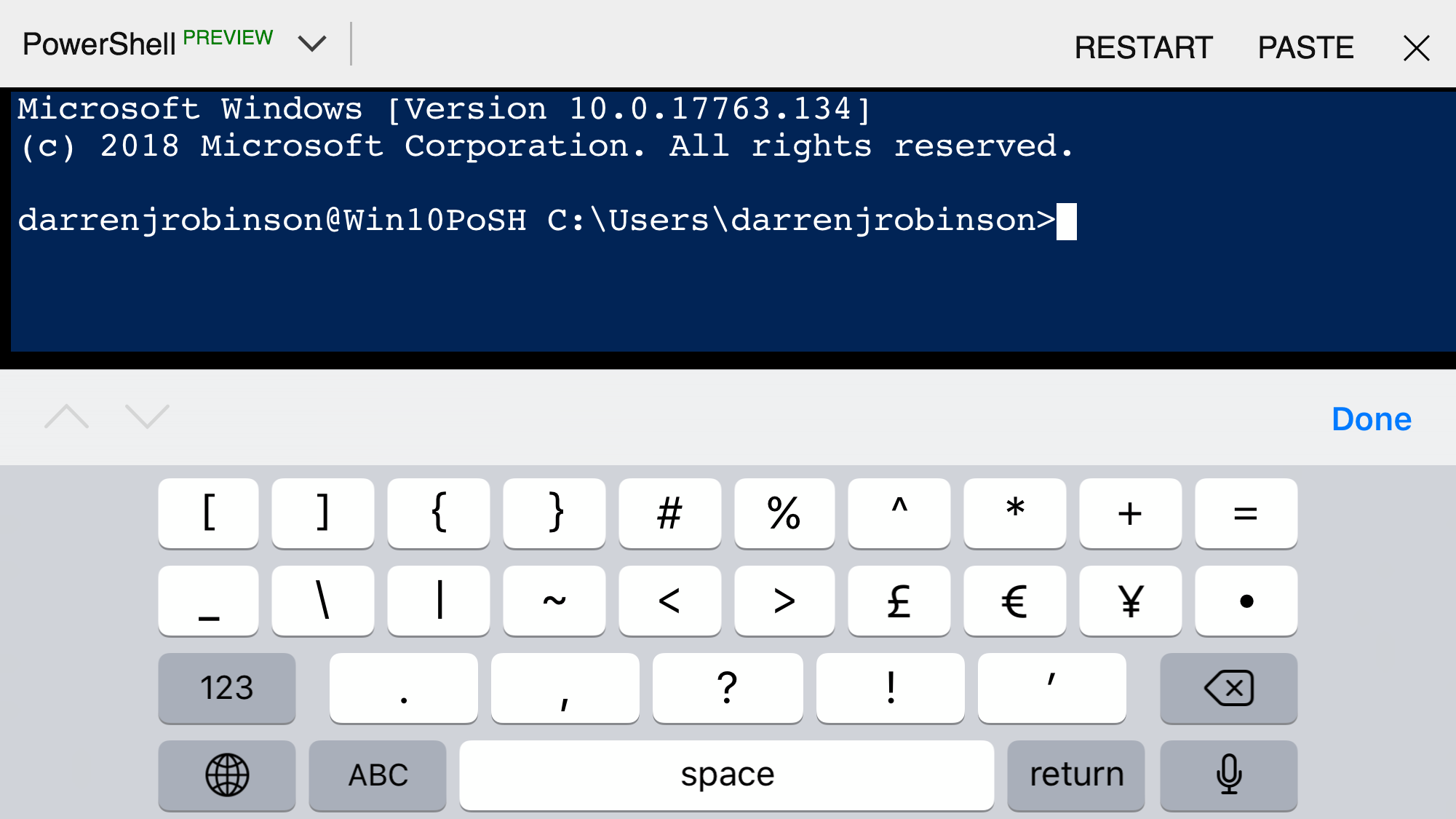
and I was then SSH’d into the Windows 10 VM.
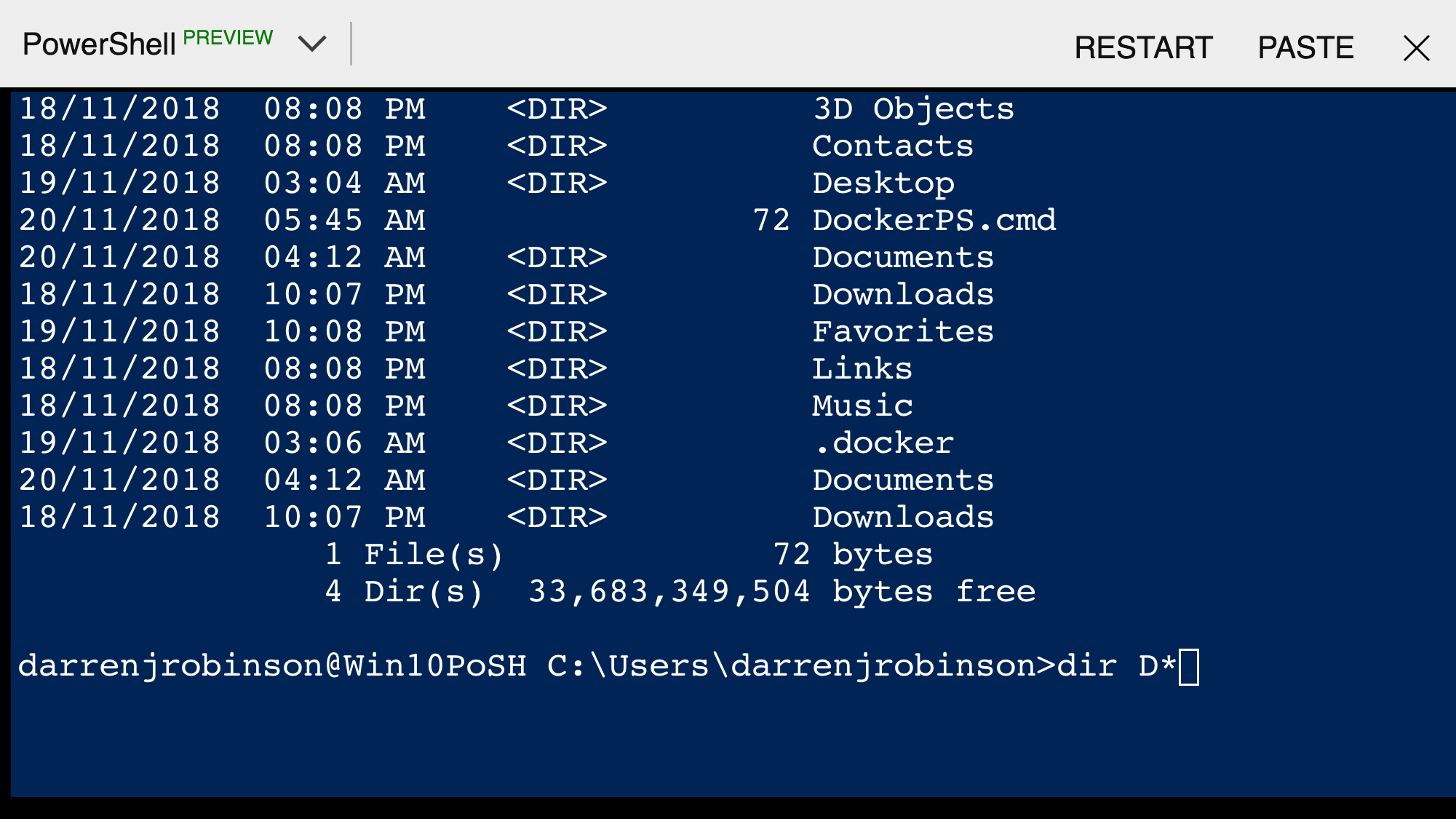
I did a dir d* and saw the DockerPS.cmd file I’d previously created. It contains the following command.
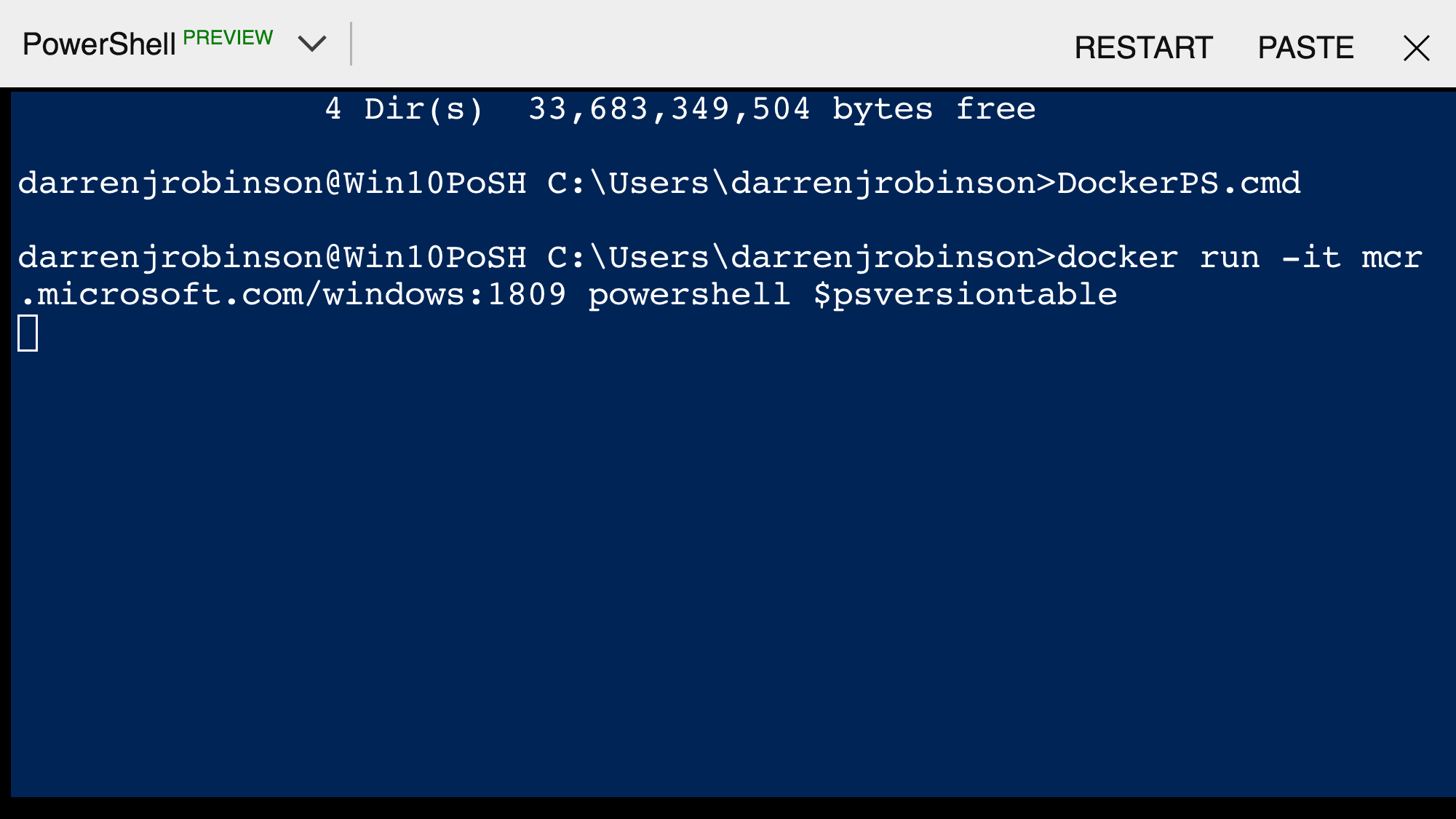
docker run -it mcr.microsoft.com/windows:1809 powershell $psversiontable
Running that file
starts the Docker Windows 1809 Container with the PowerShell command
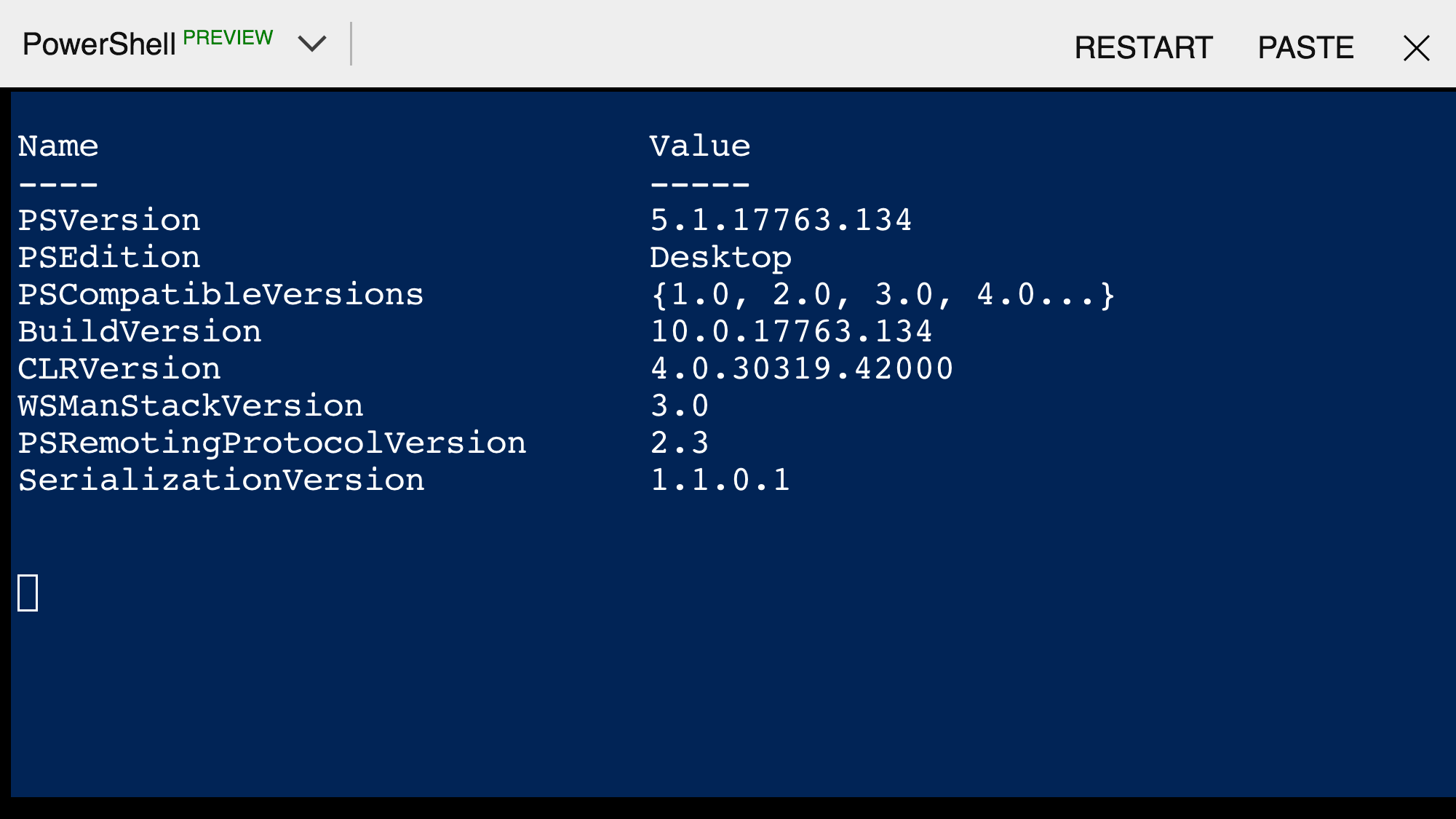
and I can see from my phone I’m have access to a PowerShell Desktop via Azure Cloud Shell and Docker from inside a Windows 10 VM based in Azure.
Summary
This post has demonstrated that it is possible to get an elevated privileged session into a Windows 10 host using SSH, from which Docker Containers can be orchestrated and executed. By doing this from Azure Cloud Shell, it means that I can essentially login to a browser or app from anywhere in the world and access my Virtual PowerShell environments that in turn will allow world domination. Muwahahahah.
Got thoughts or feedback on this? Twitter || Blog

Comments are closed.