Working with Linux technologies exposes you to a huge number of open source tools that can simplify and speed up your development workflow. Interestingly enough, many of these tools are now flooding into the Windows ecosystem allowing us to increase the portability of our development assets across multiple operating systems.
Today I am going to demonstrate how easy it is to install OpenSSL on Windows and how simple it is to quickly create self-signed certificates for our development TLS needs that will work on a range of operating systems.
We will start by installing the following tools:
1. Chocolatey
https://chocolatey.org/
“Chocolatey is a package manager for Windows (like apt-get or yum but for Windows). It was designed to be a decentralized framework for quickly installing applications and tools that you need. It is built on the NuGet infrastructure currently using PowerShell as its focus for delivering packages from the distros to your door, err computer.”
2. Cmder
https://chocolatey.org/packages?q=cmder
“Cmder is a software package created out of pure frustration over the absence of nice console emulators on Windows. It is based on amazing software, and spiced up with the Monokai color scheme and a custom prompt layout. Looking sexy from the start”
Benefits of this approach
- Using OpenSSL provides portability for our scripts by allowing us to run the same commands no matter which OS you are working on: Mac OSX, Windows or Linux.
- The certificates generated through OpenSSL can be directly imported as custom user certificates on Android and iOS (this is not the case with other tools like makecert.exe, at least not directly).
- Chocolatey is a very effective way of installing and configuring software on your Windows machine in a scriptable way (Fiddler, Chrome, NodeJS, Docker, Sublime… you name it).
- The “Cmder” package downloads a set of utilities which are commonly used in the Linux world. This once again allows for better portability of your code, especially if you want to start using command line tools like Vagrant, Git and many others.
Magically getting OpenSSL through Cmder
Let’s get started by installing the Chocolatey package manager onto our machine. It only takes a single like of code! See: https://chocolatey.org/install
Now that we have our new package manager up and running, getting the Cmder package installed becomes as simple as typing in the following instruction:
C:\> choco install cmder
reference: http://cmder.net/
The Cmder package shines “big time” because it installs for us a portable release of the latest Git for Windows tools (https://git-for-windows.github.io). The Git for Windows project (aka msysGit) gives us access to the most traditional commands found on Linux and Mac OSX: ls, ssh, git, cat, cp, mv, find, less, curl, ssh-keygen, tar ….
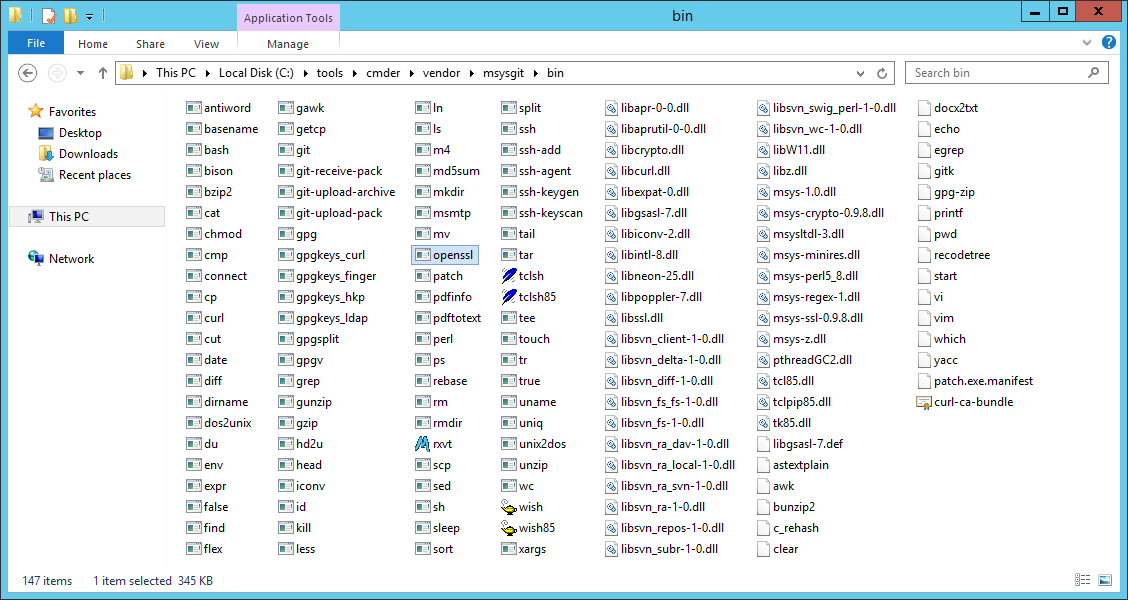
… and OpenSSL.
Generating your Root CA
The following instructions will help you generating your Root Certificate Authority (CA) certificate. This is the CA that will be trusted by your devices and that will be used to sign your own TLS HTTPS development certs.
We now double-click on the myRootCA.pfx file to fire up the Windows Certificate Import Wizard and get the Root CA imported into the Trusted Root Certification Authorities store. Too easy… let’s move on to signing our first TLS certs with it!
Generating your TLS cert
The following commands will quickly get the ball rolling by generating and signing the certificate request in interactive mode (entering cert fields by hand). In later stages you might want to use a cert request configuration file and pass it in to the OpenSSL command in order to make the process scriptable and therefore repeatable.
Just for the curious, I will be creating a TLS cert for “sweet-az.azurewebsites.net” to allow me to setup a local dev environment that mimics an Azure Web App.
Just as we did in the previous step, we can double click on the packaged myTSL.pfx file to get the certificate imported into the Local Machine/Personal Windows Certificate Store.
Testing things out
Finally we will just do a smoke test against IIS following the traditional steps:
- Create an entry for the hostname used in the cert in your hosts file:
127.0.0.1 sweet-az.azurewebsites.net - Create an 433 binding for the default site in IIS Management Console.
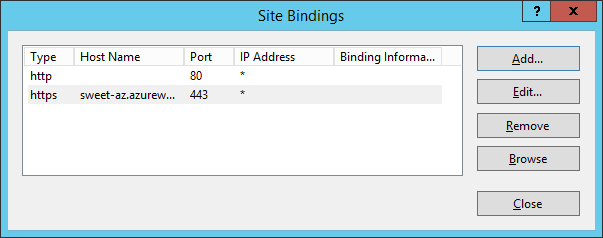
Let’s confirm that everything has worked correctly by opening a browser session and navigating to our local version of the https://sweet-az.azurewebsites.net website.
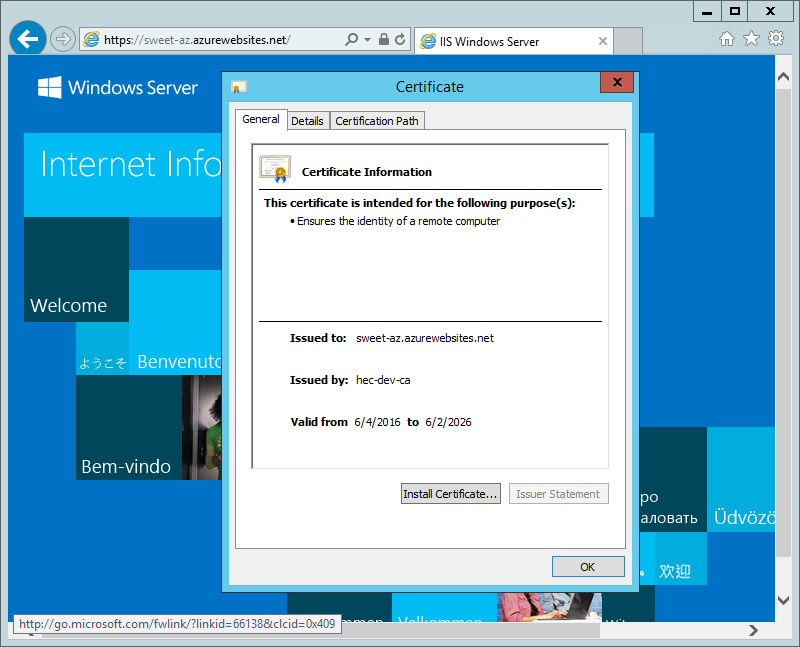
That’s all folks!
In following posts I will cover how we get these certs installed and trusted on our mobile phones and then leverage other simple techniques to help us developing mobile applications (proxying and ssh tunneling). Until then….
Happy hacking!

I did this in my lab. I have also automated the renewal.
Good stuff! Extending on the renewal.. just found this video “ACME servers” (sounds like a joke)
https://www.youtube.com/watch?v=5S8ms93mVC4
https://letsencrypt.github.io/acme-spec/
On the Git for Windows portability subject, there are still some differences when porting the code across multiple platforms. Enough to still make you waste a bit of time. Lets hope the ubuntu on windows package can solve that once it is made easily turned on on windows 10 and others.