
This is the first post in a series where I will provide a number of base-level Management Agents for Microsoft Identity Manager to integrate with SailPoint IdentityNow. Whilst the two products have areas of competing/equivalent functionality there are other aspects where integration of the two compliment each other. Whilst that is not the purpose of this post, through the series of upcoming posts it will be relatively easy to extrapolate how the two products can happy co-exist and orchestrate each other for certain functions.
This Management Agent is for Microsoft Identity Manager to have visibility of IdentityNow Roles (see customisation at the end for me functionality).
For more information on IdentityNow Roles see this post where I detailed Creating Roles as well as updating/managing them via API. The MA also consumes whether the Role is requestable that I covered in this post.
Notes
- The Management Agent is a Full Sync only Management Agent. This is because the IdentityNow API doesn’t expose differential style requests. That is also why this is a single function Management Agent (just for Roles).
- The Management Agent is configured for Paging the results back into Identity Manger. For more details on that see this post.
Prerequisites
- On your MIM Sync Server you will need the PowerShell Community Extensions (PSCX) for the Get-Hash cmdlet
- The Management Agent uses IdentityNow v3 Authentication. You will need to request the API Keys from your SailPoint Customer Success Manager. Details on v3 Authentication can be found in this post
- The Management Agent leverages the Granfeldt PowerShell Management Agent. Start here to get up to speed with that. As detailed above this is an Import only MA so I’m not providing an Export Script and the Password is redundant. The script files need to be present but will be empty
Schema Script
The Schema Script below covers the core attributes associated with IdentityNow Roles.
Import Script
As IdentityNow v3 API Authentication requires a number of artifacts, we need to make sure we secure them all appropriately.
For the Admin Username and Password we will do that by exporting them to an XML file using Export-CLIXML and then in the Import Script, import them using Import-CLIXML. Those cmdlets respect the context by which the credentials were exported and will only be able to access them when imported under that same context. As our Management Agent will be run by the MIM Sync Server Service Account we need to create the credentials file using that login. To do that;
- temporarily reconfigure the MIM Sync Service Account so that it can logon locally
- On the MIM Sync Server open Local Security Policy = > Local Policies => User Rights Assignment => Deny log on locally and remove the MIM Sync Server Service Account
- repeat for Deny access to this computer from the network
- Logon to the MIM Sync Server using the MIM Sync Server Service Account
- Run the following to create the credential file and put the credential file in the Extensions\yourRolesMA directory
$adminUSR = [string]"Partner_Admin".ToLower() $adminPWDClear = 'myStr0ngP@$$w0rd' $adminPWD = ConvertTo-SecureString $adminPWDClear -AsPlainText -Force $Credentials = New-Object System.Management.Automation.PSCredential $adminUSR,$adminPWD $Credentials | export-clixml c:\temp\RoleAdminCred.xml
- IMPORTANT: Add the MIM Sync Server Service Account back into the Deny access to this computer from the network and Deny Logon Locally policies
The IdentityNow v3 API Credentials are stored on the Management Agent Connectivity Configuration page. The Username and Password Authentication options take the v3 API Client ID and API Client Secret respectively.
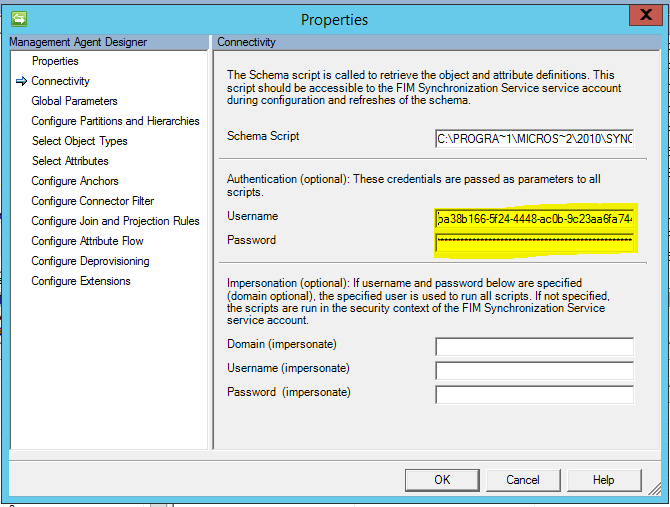
Make the following updates for your implementation:
- Line 24 for your IdentityNow Organisation name
- Line 27 for the location and name of the credentials file created above
Customisation
Depending on what you want to do with it, will depend on how you want Identity Manger to consume the data. You will likely want to;
- Create a new ObjectType in the Metaverse along with the attributes associated with the Roles
- Flow the information in and perform any logic
- Create Roles in IdentityNow
- Update Roles in IdentityNow
Summary
Using this base management we can get connectivity and visibility of IdentityNow Roles in Microsoft Identity Manager.
