
Introduction
UPDATE: August 2018 As promised below I've finally written up my Azure AD B2B Invitation Management Agent. You can find it in this post here. UPDATE: June 2018 When I originally wrote this post the intent was to test the ability of the Graph MA to export to Azure AD. That works. That then extended to messing with an identity type other than member (which works to an extent) but I detailed guests. However that is incomplete. I do have a working solution that utilises the Graph Invitation API via my favourite PowerShell MA (Granfeldt PS MA) and the PowerShell cmdlet New-AzureADMSInvitation from the Azure AD PowerShell Module. That solution involves the MS Graph MA connected to a Partner tenant to get visibility of partner users and then creating relevant users in the home tenant via a PowerShell MA and the New-AzureADMSInvitation cmdlet. Another MS Graph MA connected to the home tenant provides easy visibility of additional guest user attributes for ongoing functions such as reporting and de-provisioning. I will write that up later in July. Stay tuned and keep the above in mind when reading this post.
Just landed from the Microsoft Identity Manager Engineering Team is a new Management Agent built specifically for managing Azure Users and Groups and Contacts.
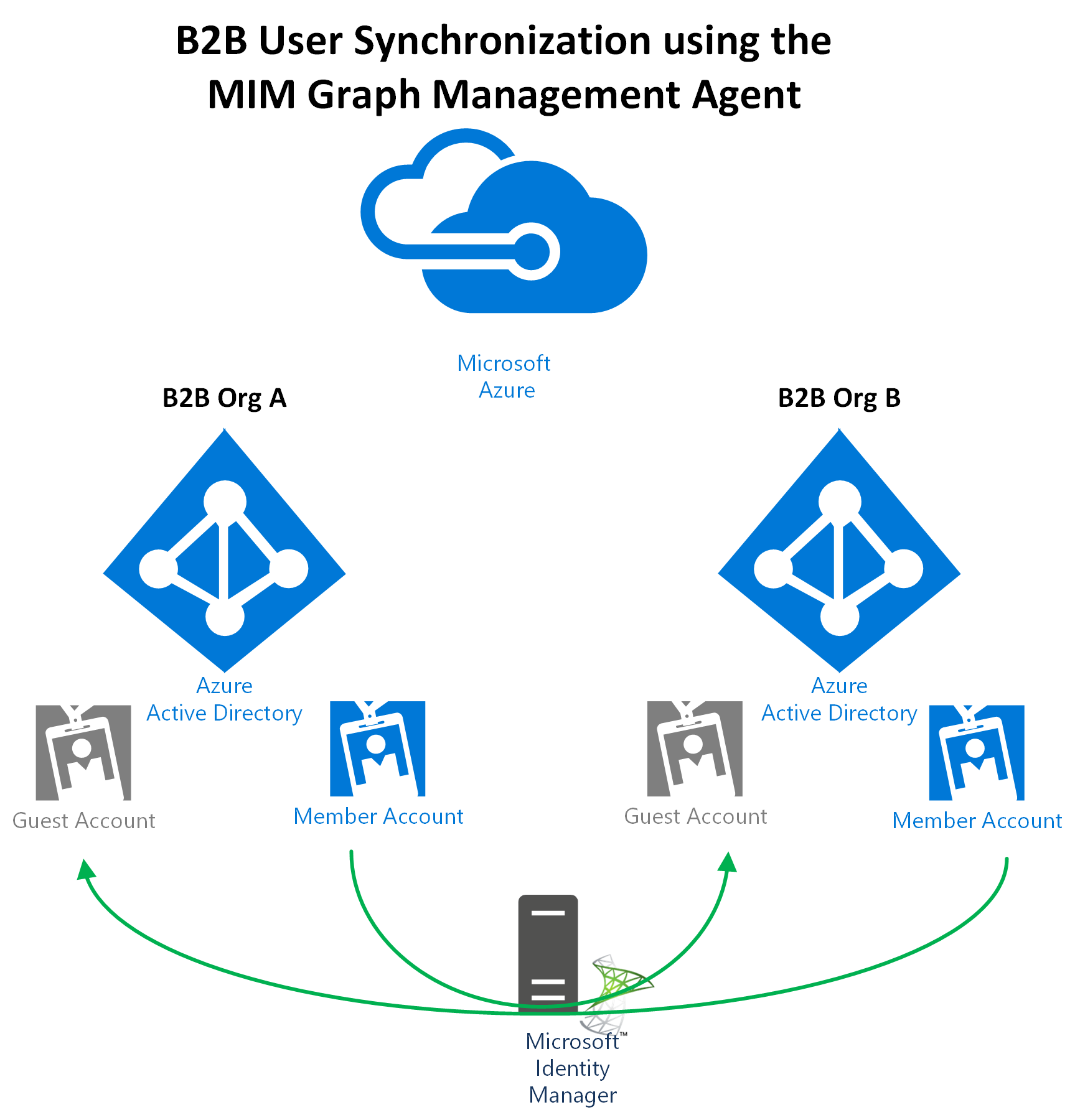
Microsoft have documented a number of scenarios for implementing the management agent. The scenarios the MA has been built for are valid and I have customers that will benefit from the new MA immediately. There is however another scenario I’m seeing from a number of customers that is possible but not detailed in the release notes. That is B2B Sync between Azure Tenants; using Microsoft Identity Manager to automate the creation of Guests in an Azure Tenant.
This could be one-way or multi-way depending on what you are looking to achieve. Essentially this is the Azure equivalent of using FIM/MIM for Global Address List Sync.
Overview
The changes are minimal to the documentation provided with the Management Agent. Essentially;
- ensure you enable Write Permissions to the Application you create in the AAD Tenant you will be writing too
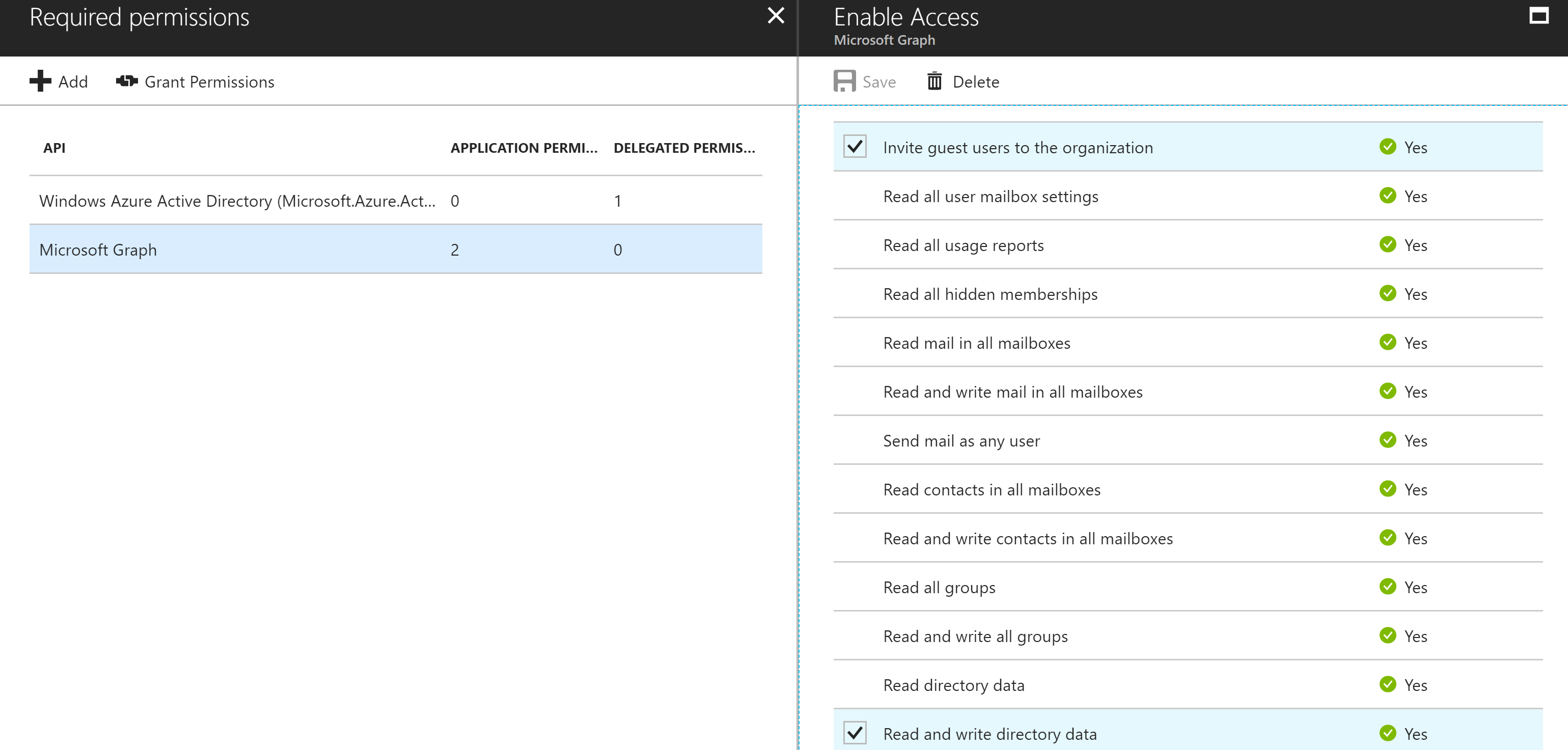
- Enable the Invite Guest users to the organization permission on the AAD Application
- Create an Outbound Sync Rule to an AAD Tenant with the necessary mandatory attributes
- Configure the Management Agent for Export Sync Profiles
In the scenario I’m detailing here I’m showing taking a number of users from Org2 and provisioning them as Guests in Org1.
What I’m detailing here supplements the Microsoft documentation. For configuring the base MA definitely checkout their documentation here.
Microsoft Graph Permissions
When setting up the Graph Permissions you will need to have Write permissions to the Target Azure AD for at least Users. If you plan to also synchronize Groups or Contacts you’ll need to have Write permissions for those too.
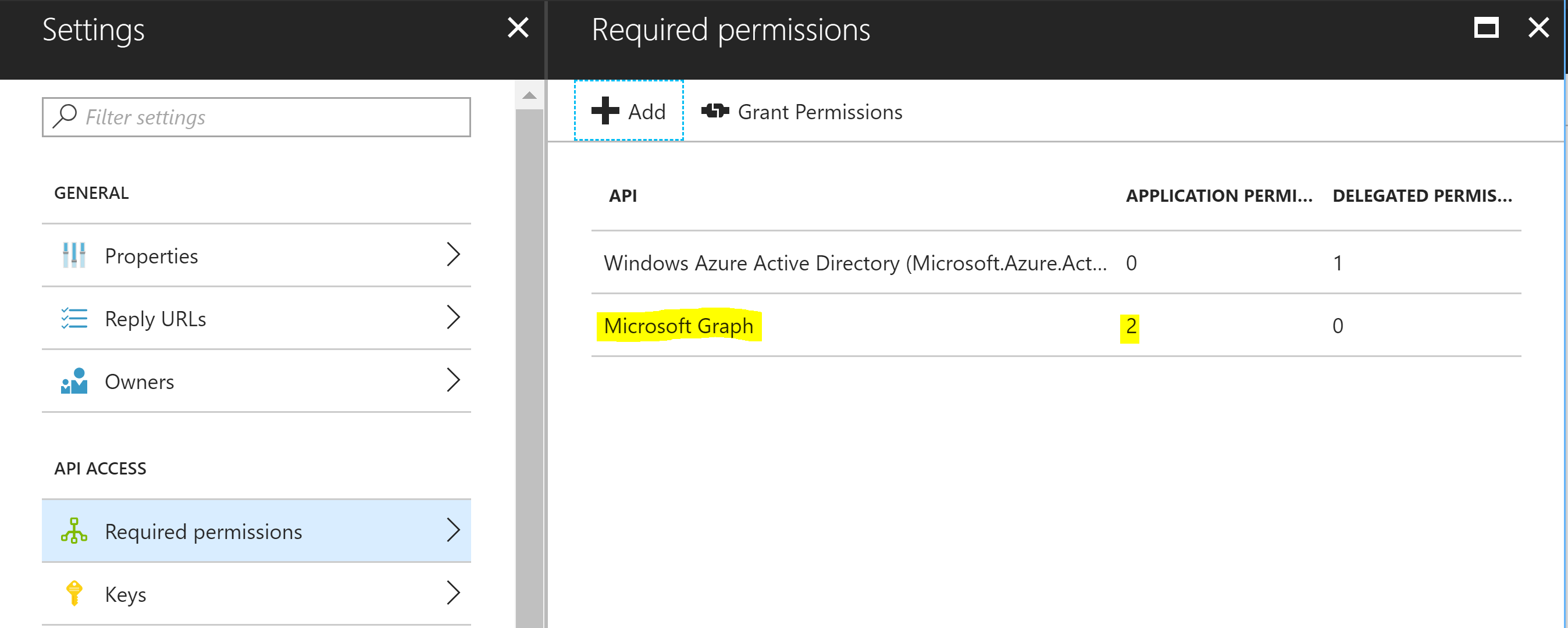
In addition as we will be automating the invitation of users from one Tenant to another we will need to have the permission ‘Invite guest users to the organization’.
With those permissions selected and while authenticated as an Administrator select the Grant Permissions button to assign those permissions to the Application.
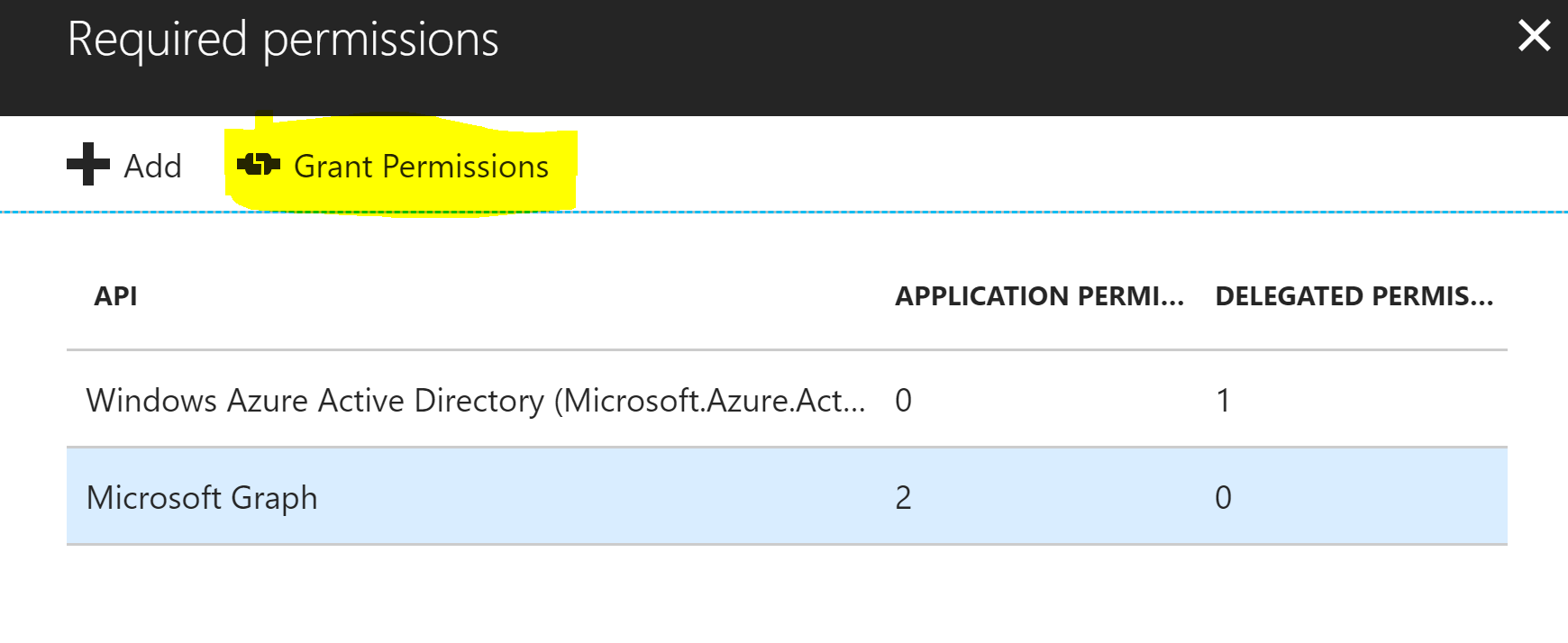
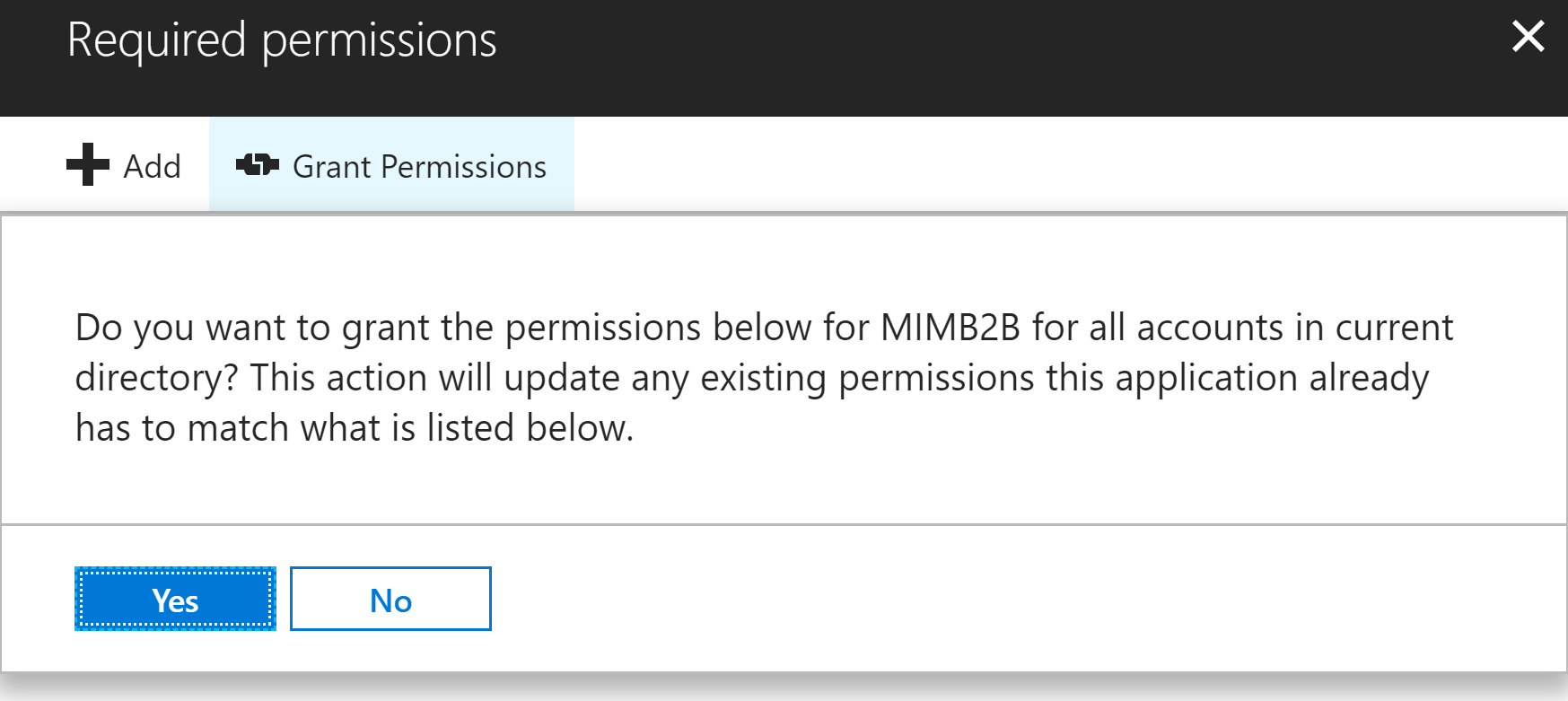
Repeat this in both Azure AD Tenants if you are going to do bi-directional sync. If not you only need write and invite permissions on the Tenant you will be creating Guest accounts in.
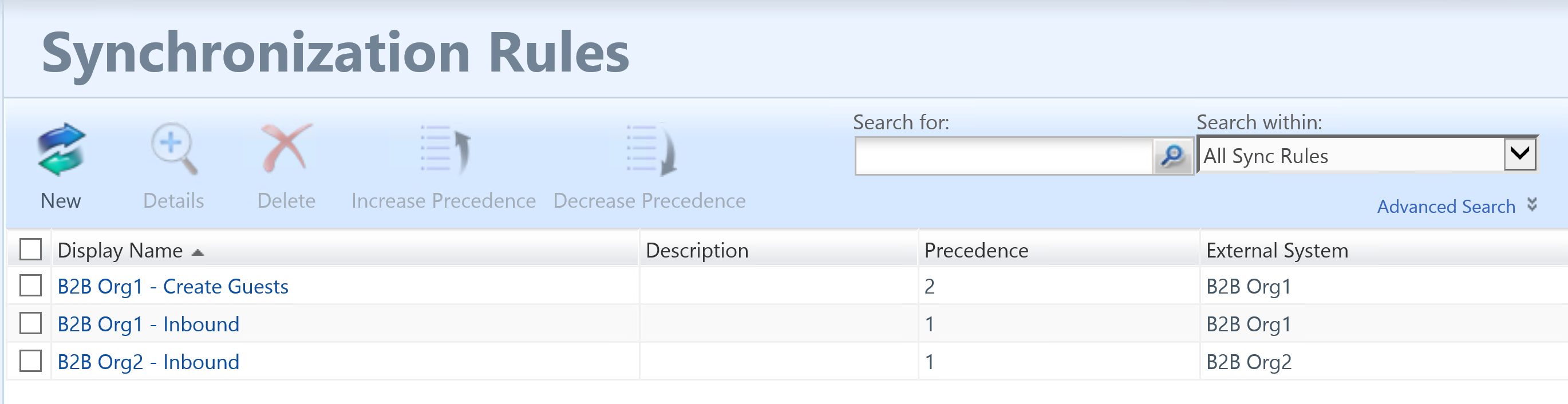
Creating the Import/Inbound Sync Rules Azure Tenants
Here is an example of my Import Sync Rules to get Members (Users) in from an Azure Tenant. I have an inbound sync rule for both Azure Tenants.
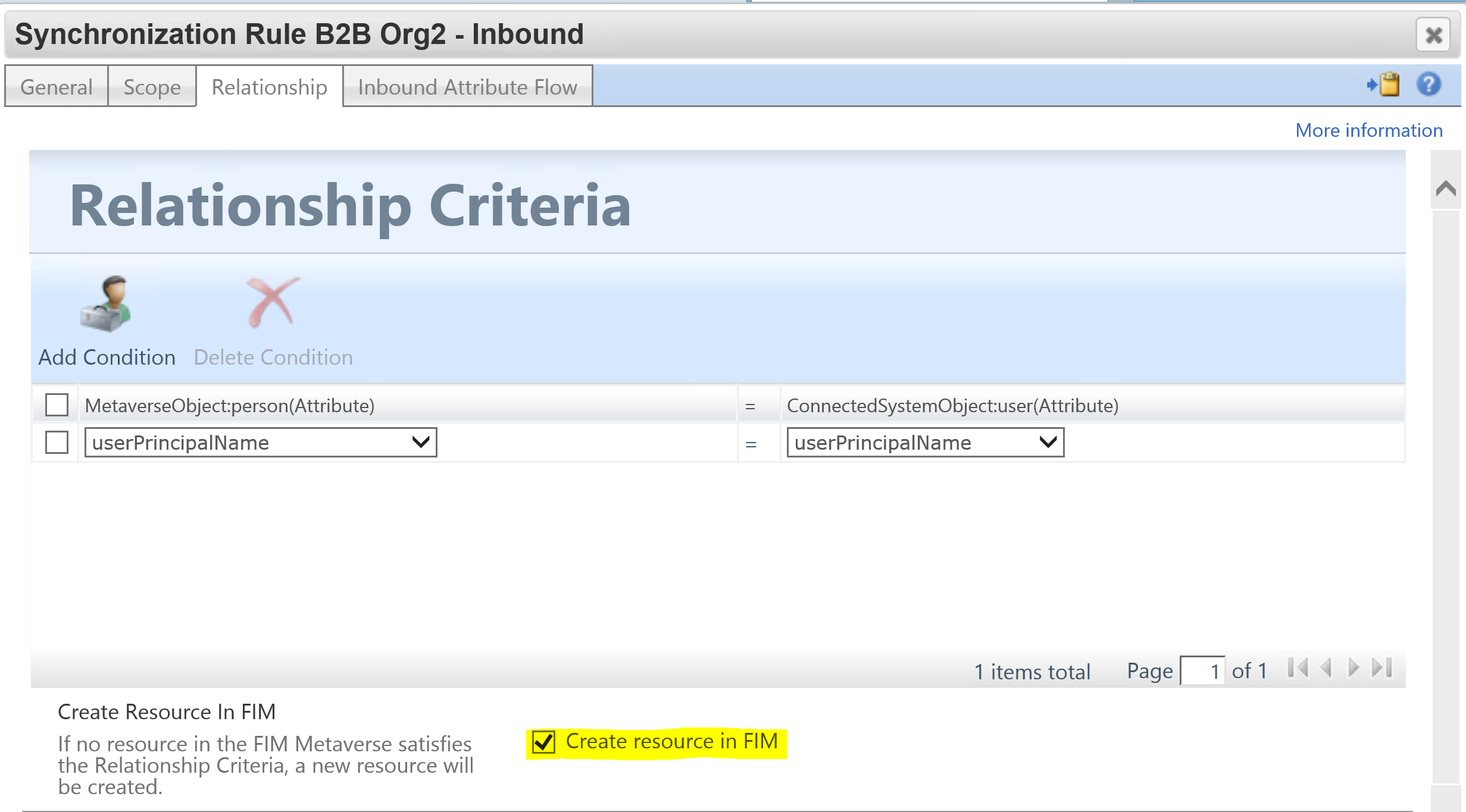
Make sure you have ‘Create Resource in FIM‘ configured on the source (or both if doing bi-directional) Graph Connector.
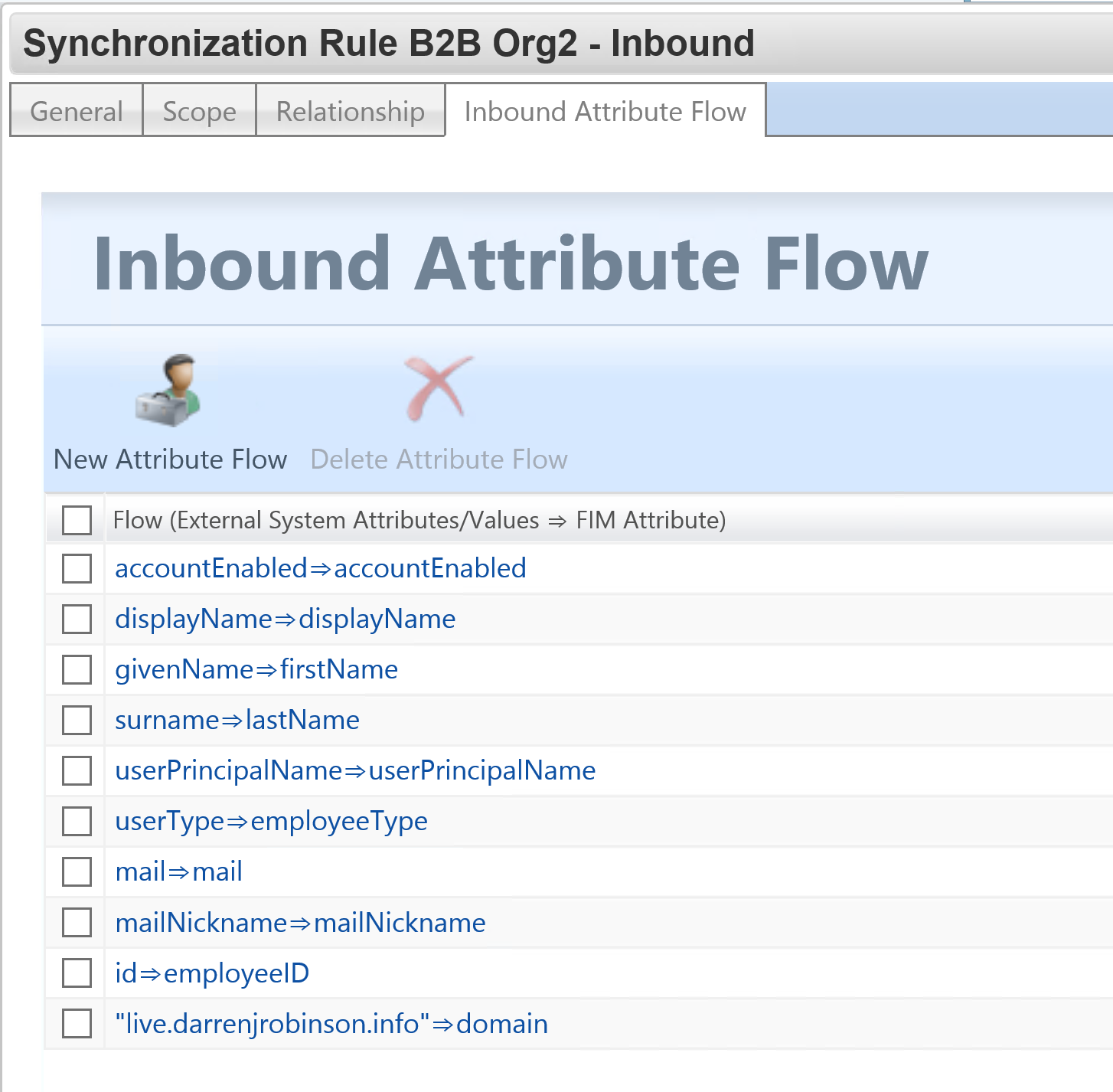
The attribute flow rules I’ve used are below. They are a combination of the necessary attributes to create the corresponding Guest account on the associated management agent and enough to be used as logic for scoping who gets created as a Guest in the other Tenant. I’ve also used existing attributes negating the need to create any new ones.
Creating the Export/Outbound Sync Rule to a Partner B2B Tenant
For your Export/Outbound rule make sure you have ‘Create resource in external system’ configured.
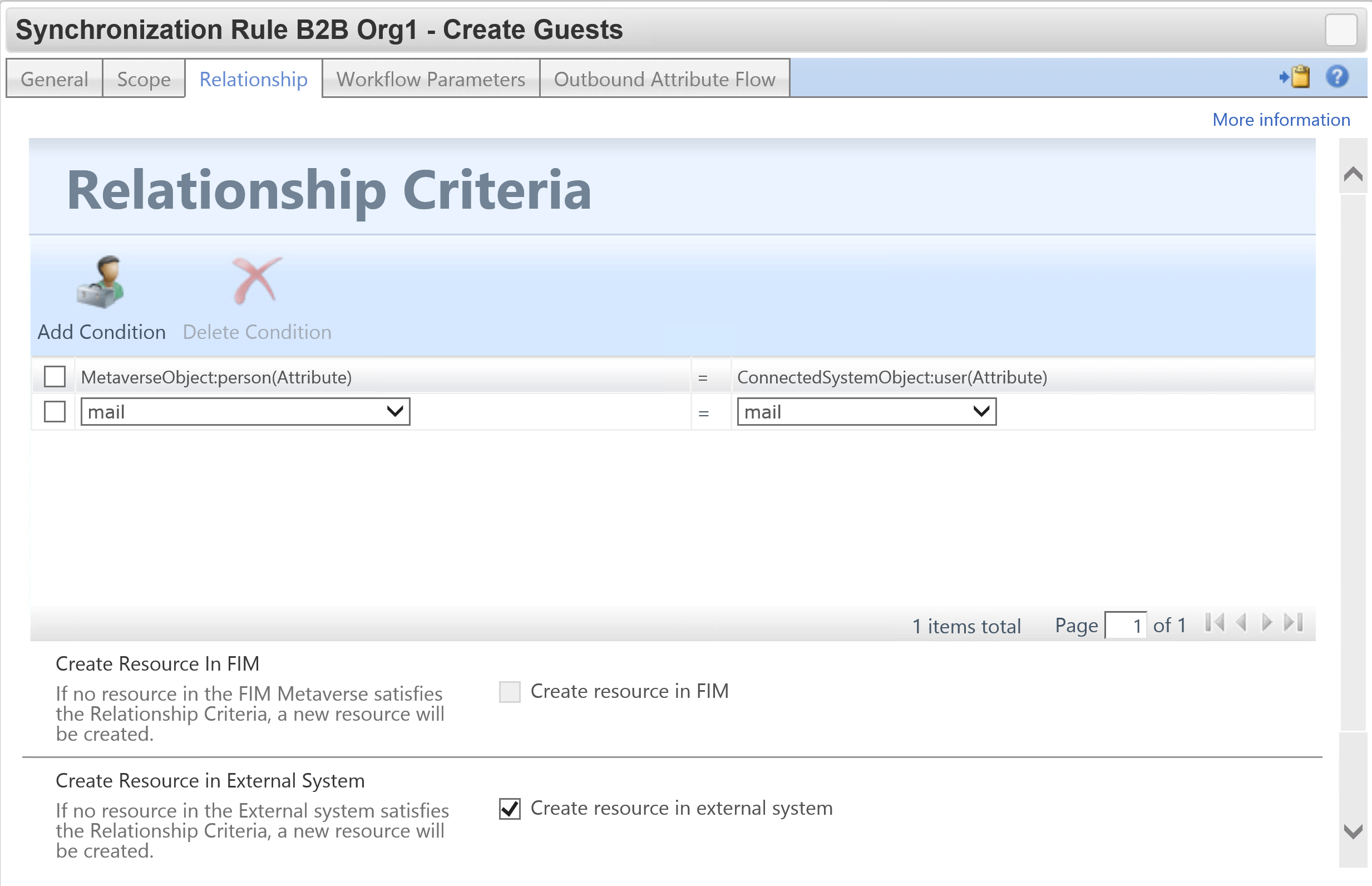
There are a number of mandatory attributes that need to be flowed out in order to create Guests in Azure AD. The key attributes are;
- userType = Guest
- accountEnabled = True
- displayName is required
- password is required (and not export_password as normally required on AD style MA’s in FIM/MIM)
- mailNickname is required
- for dn and id initially I’m using the id (flowed in import to employeeID) from the source tenant. This needs to be provided to the MA to get the object created. Azure will generate new values on export so we’ll see a rename come back in on the confirming import
- userPrincipalName is in the format of
-
- SOURCEUPN (with @ replaced with _ ) #EXT# DestinationUPNSuffix
-
- e.g user1_org2.com#EXT#org1.com
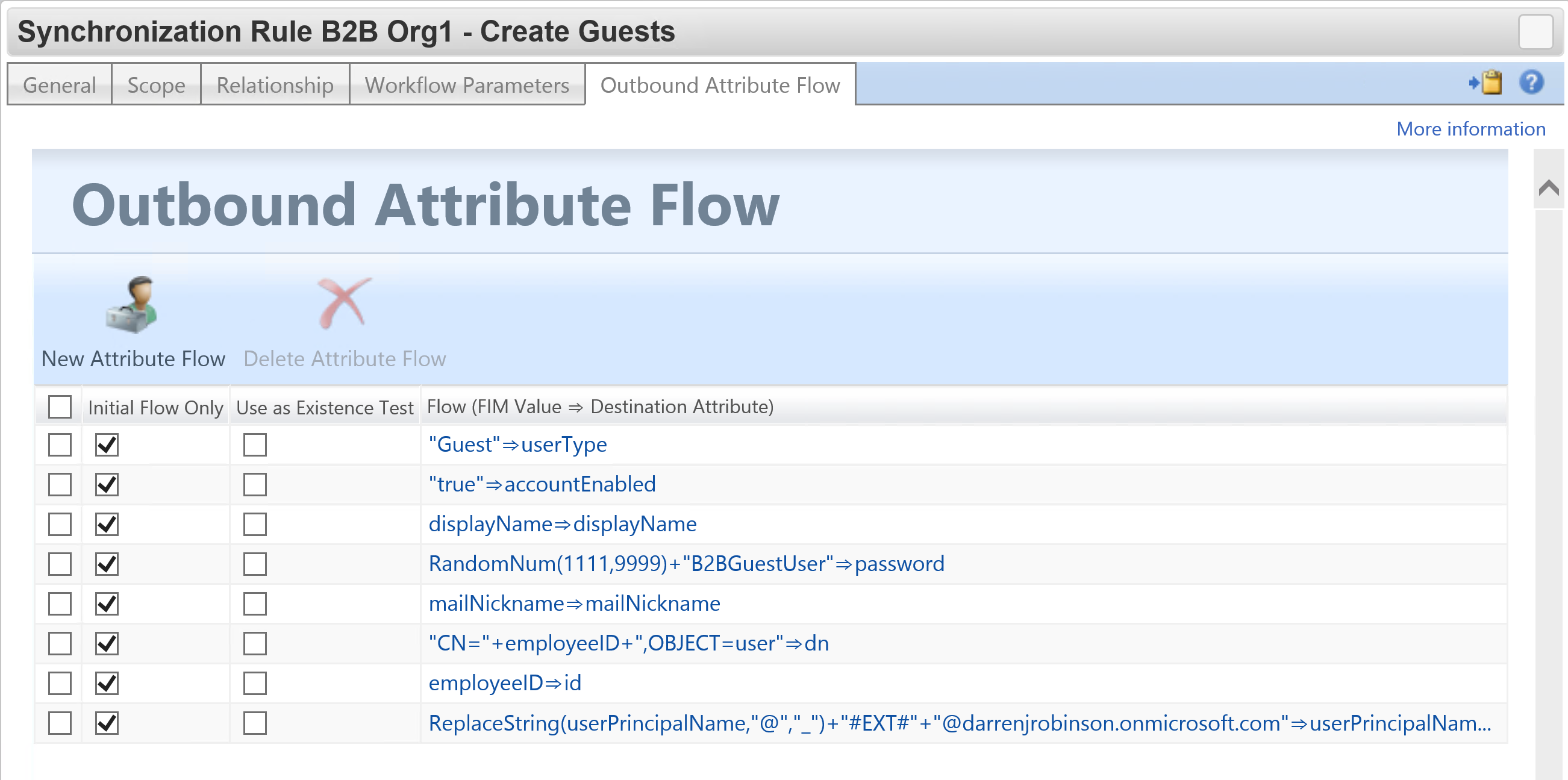
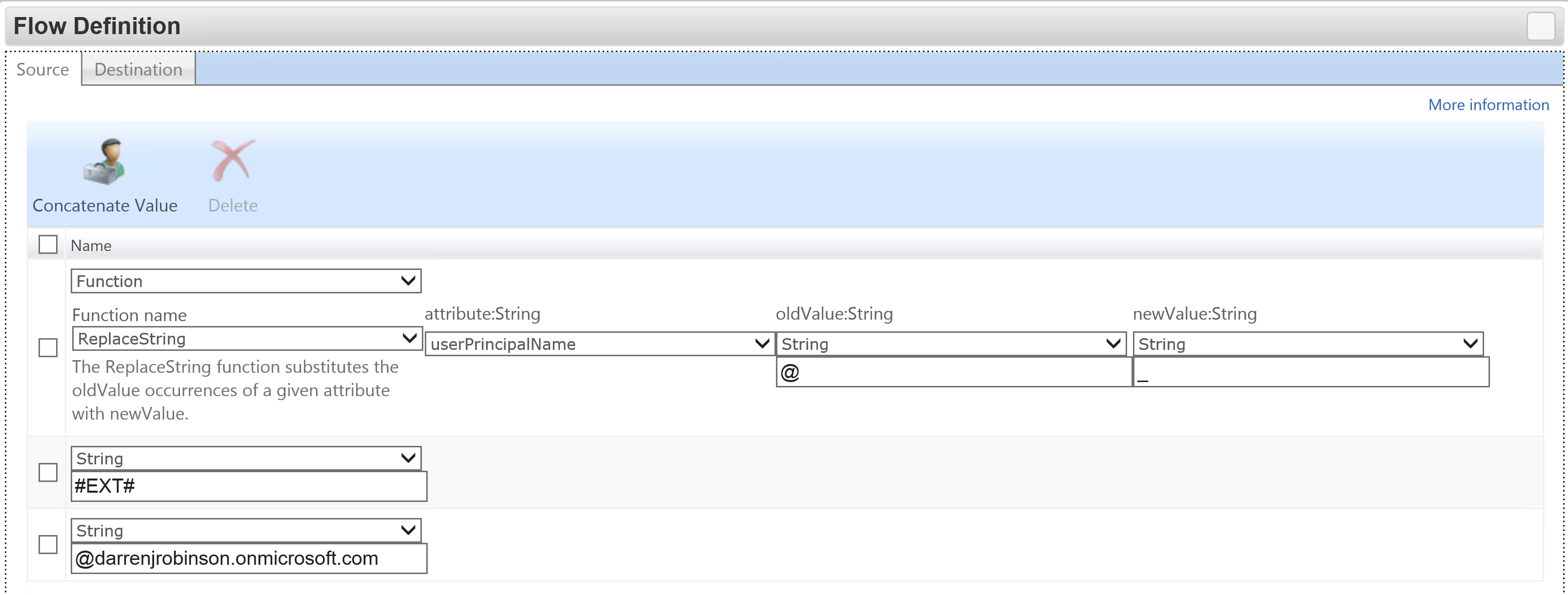
Here is an example of building a UPN.
Sets, Workflows and MPR’s
I didn’t need to do anything special here. I just created a Set based on attributes coming in from the source Azure Tenant to scope who gets created in the target Tenant. An MPR that looks for transition into the Set and applies the Workflow that associates the Sync Rule.
End to End
After synchronizing in from the source (B2B Org 2) the provisioning rules trigger and created the Users as Guests on B2B Org 1.
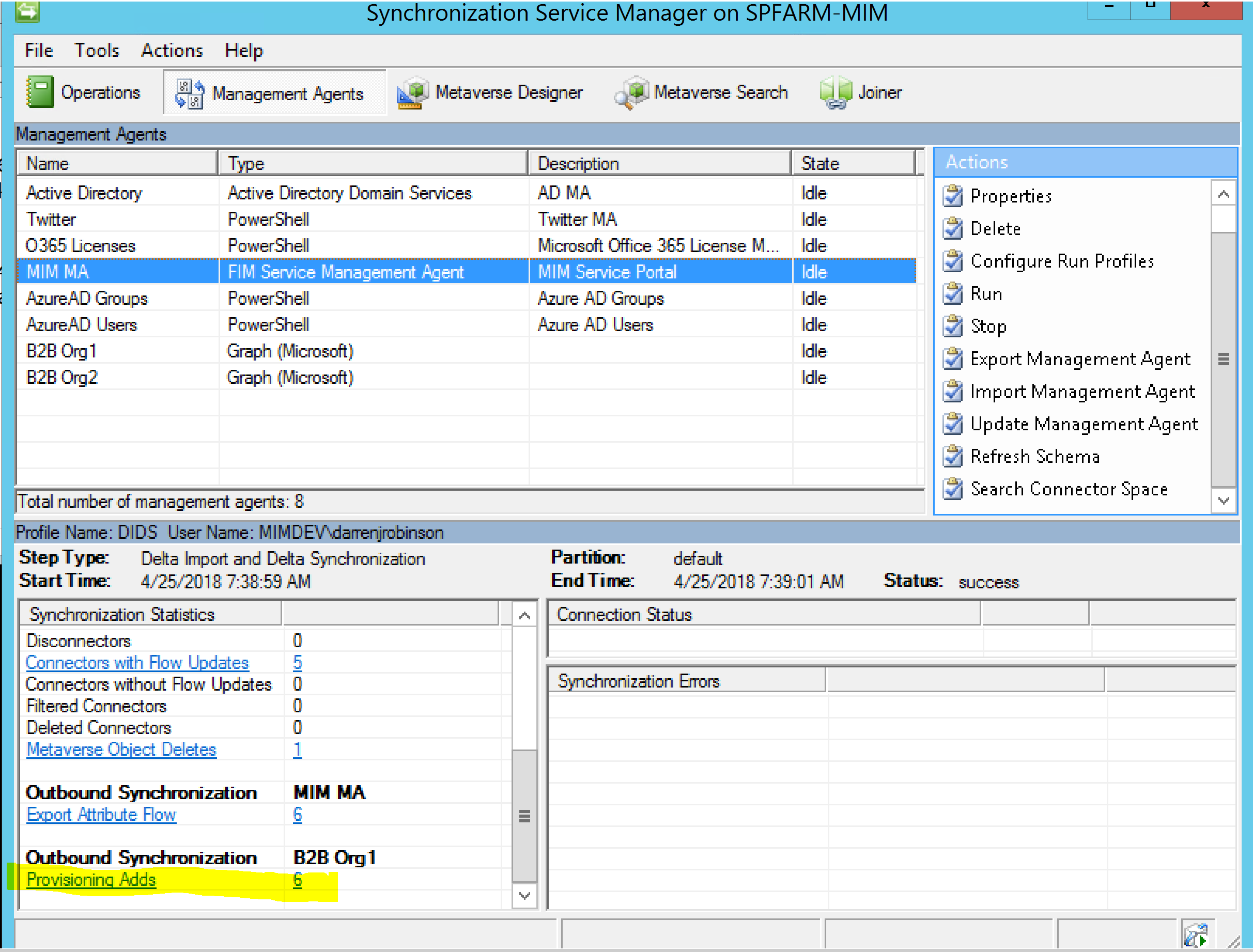
Looking at the Pending Export we can see our rules have applied.
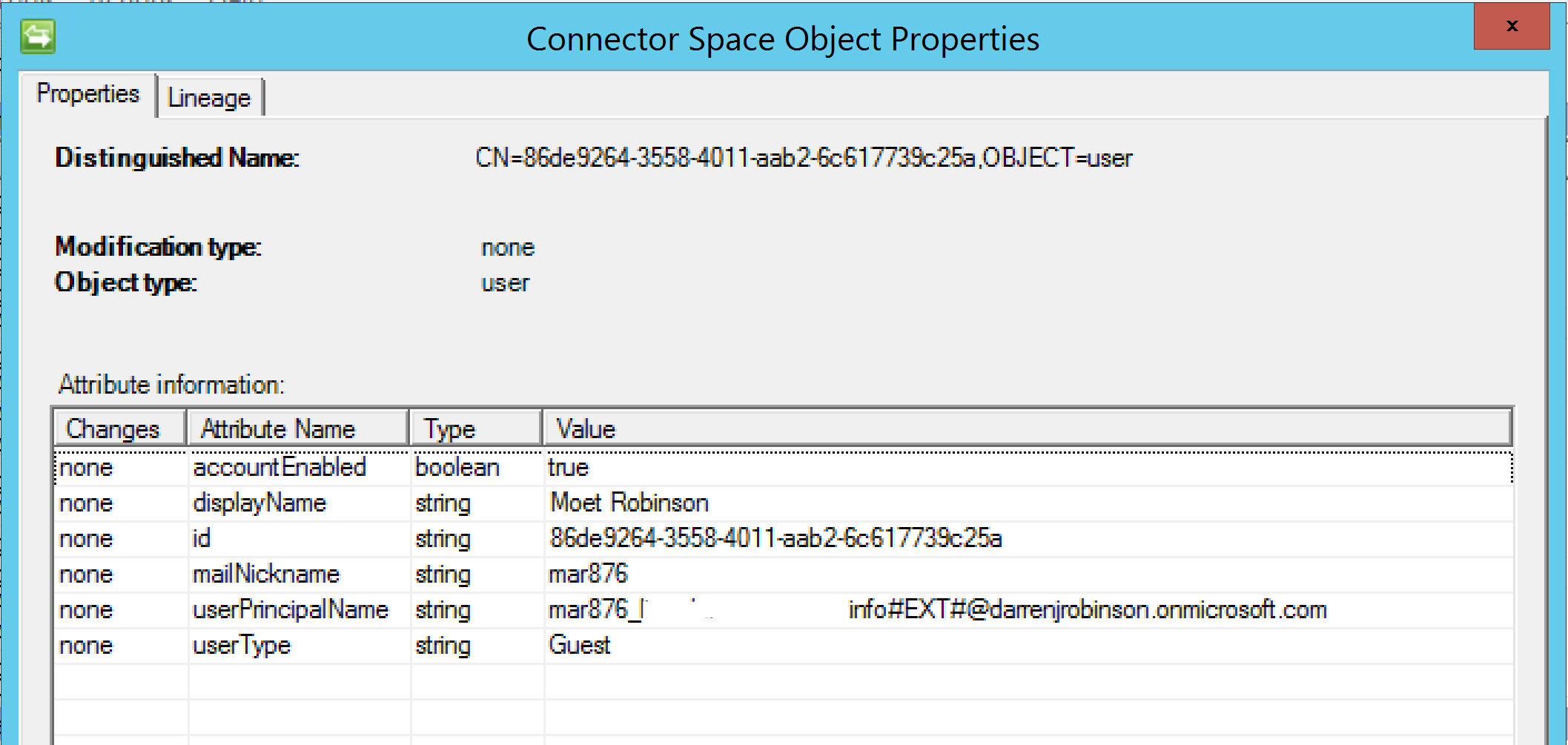
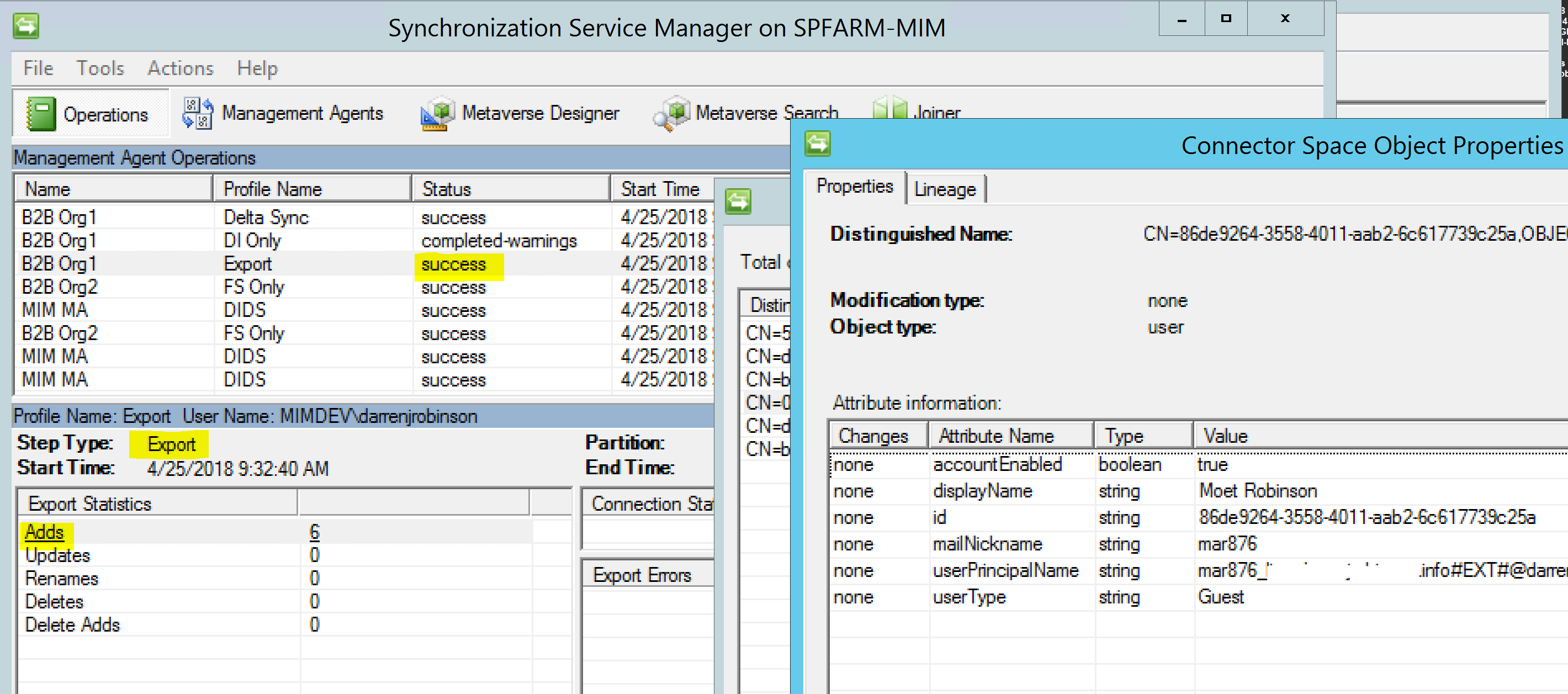
On Export the Guest accounts are successfully created.
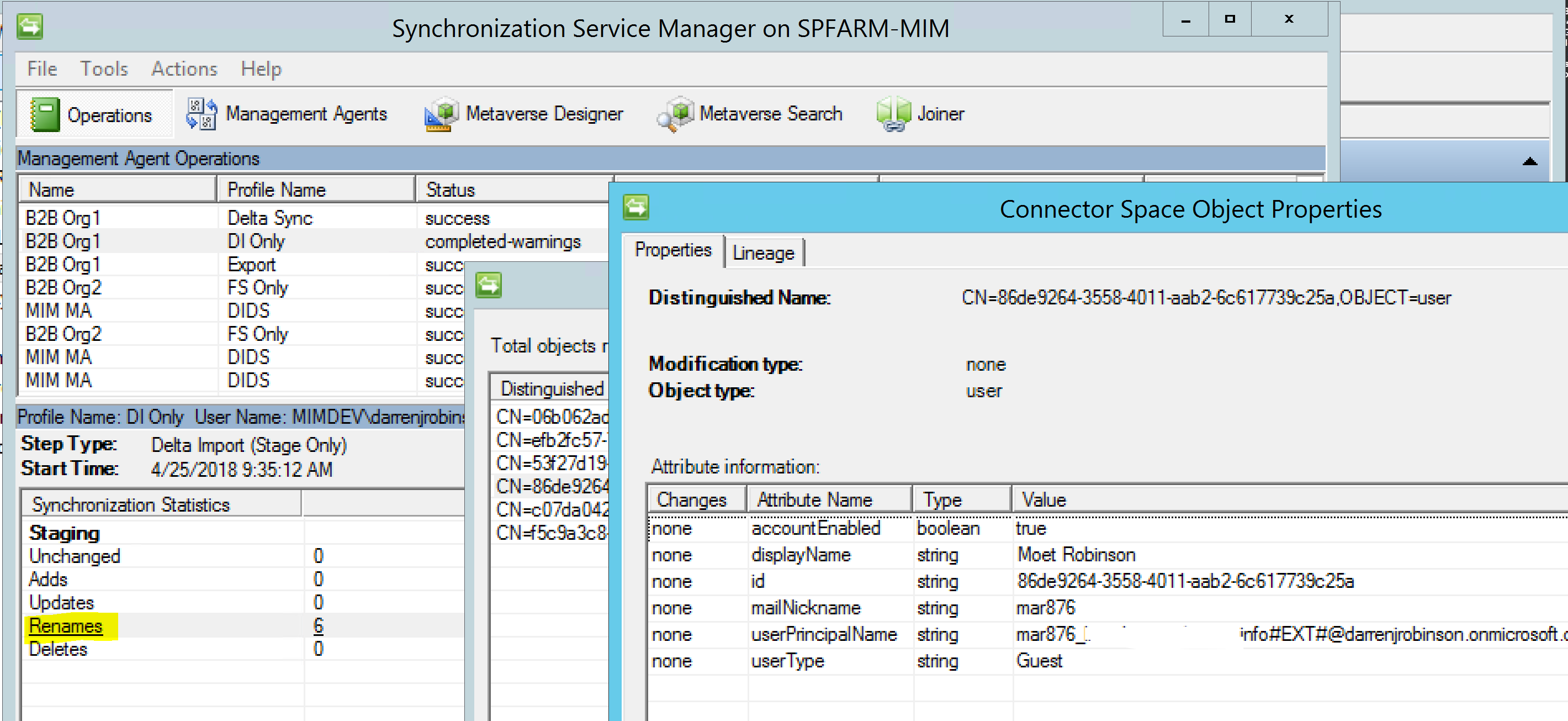
On the confirming import we get the rename as Azure has generated a new CN and therefore DN for the Guest user.
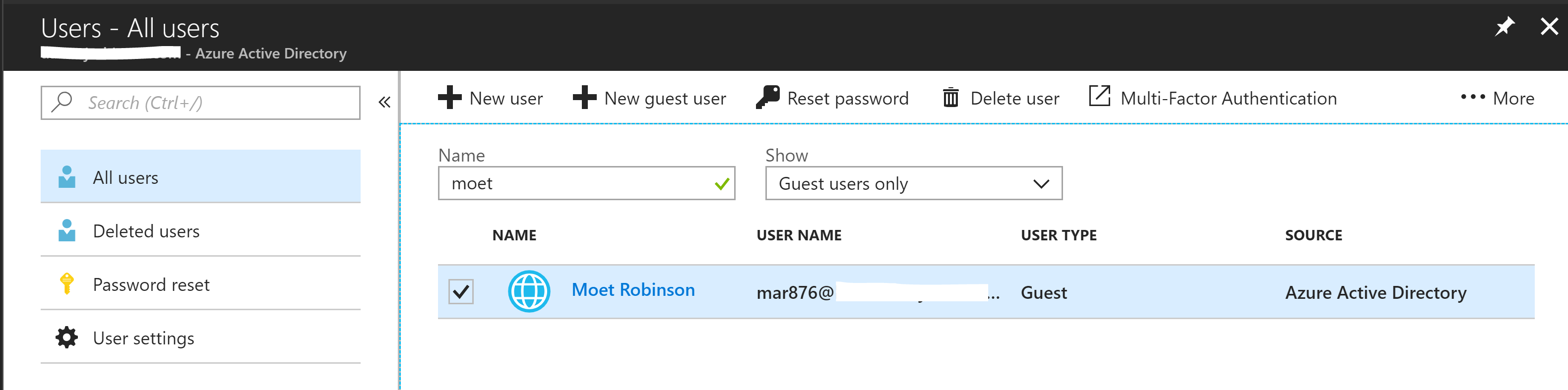
Looking into Azure AD we can see one of our new Guest users.
Summary
Using the Microsoft Azure B2B Graph Management Agent we can leverage it to create users from one Tenant as Azure AD Members in another Tenant. Stay tuned for another post detailed the solution detailed in the Update in the Introduction.

Great write up of a scenario with the MIM GraphAPI Connector. I think that team have done a great job with the release, and good to see the user cases! However I do I want to point out, that in the GraphAPI connector at the time of this post an Add is going to create a local AAD user, with a userType=Guest, but it’s not the same as a Guest user added via the Invitation API – https://docs.microsoft.com/en-us/azure/active-directory/b2b/customize-invitation-api Notice the source in your screenshots is Azure Active Directory A user which is redeemed to an external Azure AD will have the credential managed in that external Azure AD tenant, not the local one as seen here.
Check out the information here on adding users without invitations as well: https://docs.microsoft.com/en-us/azure/active-directory/b2b/add-user-without-invite
Hello, when will you share the solution using PowerShell MA? Thanks.
Early August as I’m travelling overseas on holidays.
Apologies for the delay as I’ve been traveling a lot the last 6 weeks. Posted now. https://blog.darrenjrobinson.com/automating-azure-ad-b2b-guest-invitations-using-microsoft-identity-manager/