Introduction
One of the foundations of Identity Management is the ability to join an identity between disparate connected systems. As we extend our management of identities into cloud services this adds a few twists.
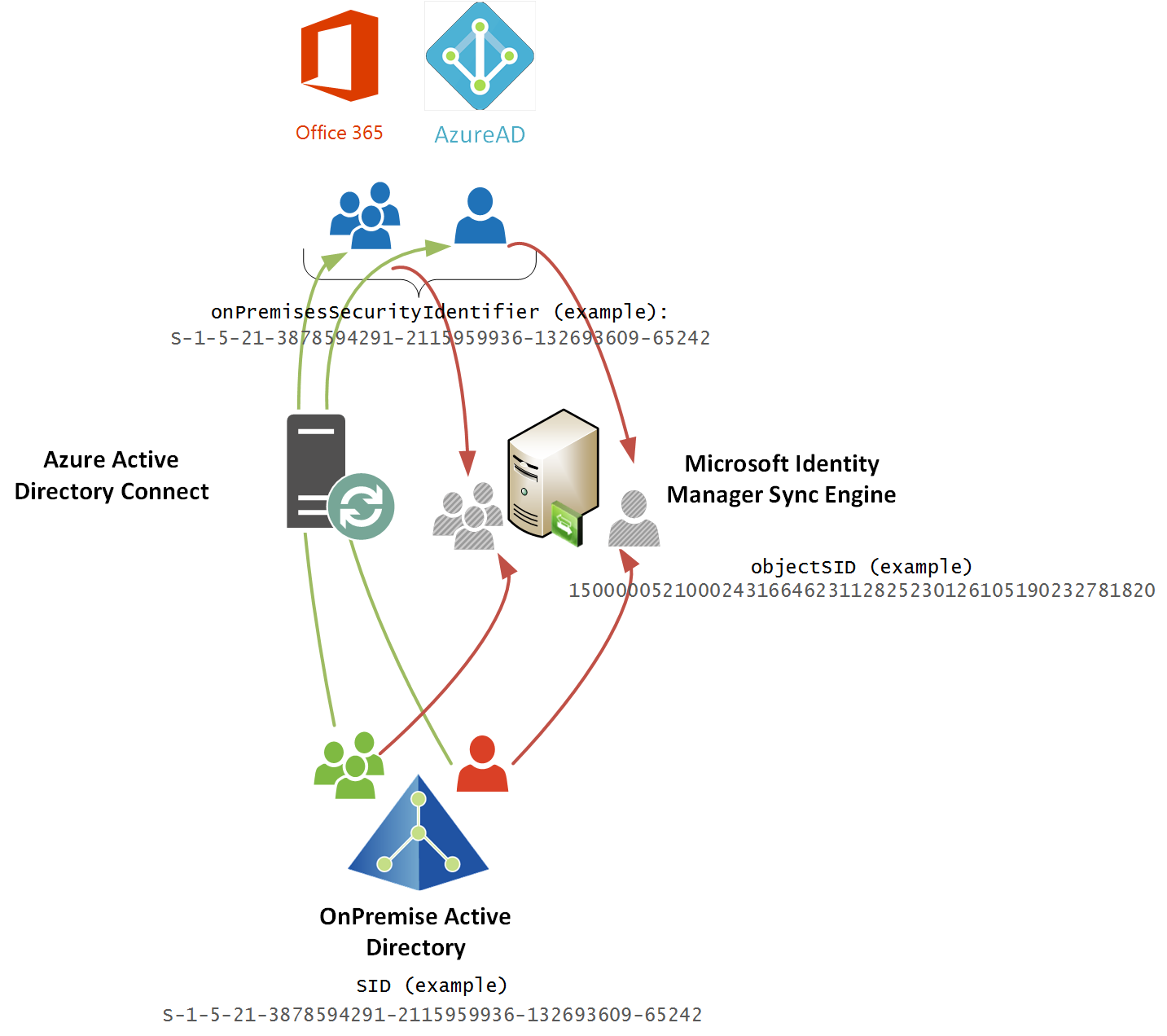
A key concept is to use an anchor that is persistent. Something that doesn’t change through a users life-cycle. A user’s Security IDentifier (SID) in Active Directory is perfect. It doesn’t change when a user or group may get renamed. What gets interesting is how the SID is represented when returned using different methods. That is what I quickly cover in this post.
Overview
The defacto method for connecting your OnPremise Active Directory to Azure Active Directory is to use Azure Active Directory Connect. AADC will synchronise users and groups SID’s to the corresponding object in AAD into the onPremisesSecurityIdentifier attribute.
When the onPremisesSecurityIdentifier attribute is retrieved via the GraphAPI the format looks like this: S-1-5-21-3878594291-2115959936-132693609-65242
Using an Active Directory Management Agent for FIM/MIM and synchronizing the objectSID from the OnPremise AD represents the value in the Metaverse in binary format which when viewed as text looks like this: 15000005210002431664623112825230126105190232781820
Translating SID formats so we can join identities
What we need to do is translate the string representation of the SID returned from the GraphAPI and AzureAD so that we have it in a binary format. Then we can then use those attributes in join rules to match users/groups between AzureAD and our OnPremise Active Directory.
In my environments I’m using the out of the box FIM/MIM Active Directory Management Agent. For Azure AD/Office 365 I’m using the Granfeldt PowerShell Management Agent to integrate with Azure AD via the GraphAPI.
On my AzureAD PowerShell Management Agent I have an attribute named AADonPremiseSID configured with the format as Binary in my PSMA Schema.ps1 as shown below.
$obj | Add-Member -Type NoteProperty -Name "AADonPremiseSID|Binary" -Value 0x10
On my Azure AD PSMA I have the following lines in my Import.ps1 which essentially takes the value retrieved from the GraphAPI S-1-5-21-3878594291-2115959936-132693609-65242 and converts it to a binary array that in text looks something like 15000005210002431664623112825230126105190232721825400 and stores it in the AADonPremiseSID binary attribute in the connector space.
# Create SID .NET object using SID string from AAD S-1-500-........
$sid = New-Object system.Security.Principal.SecurityIdentifier $user.onPremisesSecurityIdentifier
#Create a byte array for the length of the users SID
$BinarySid = new-object byte[]($sid.BinaryLength)
#Copy the binary SID into the byte array, starting at index 0
$sid.GetBinaryForm($BinarySid, 0)
#Add the SID to the user in the connector space
$obj.Add("AADonPremiseSID",$BinarySid)
This then lets me join my users (and groups using the same method) between AD and AAD. Essentially a line to put it into Security Identifier format, two lines to convert it to a binary array and a line to store it in the connector space. Simple when you don’t over think it.
I’m posting this because I know I’m going to need to do this often. Hope it helps someone else too.

Do you know how to extra the security identifier (SID) from an Azure AD user?