The biggest challenge for BYOD devices is data security and leakage, a common method to enforce data protection is through Exchange ActiveSync and/or Mobile Device Management (MDM) tools such as AirWatch, Intune and others.
Both ActiveSync and MDM comes with the option of device wipe and enforcing device PIN. If the device is lost or the employee is terminated, the company could remote wipe the device to protect its data. While device wipe is great from the company’s perspective, it is almost always met with resistance from the employees because everyone fears the company has the power to wipe their personal data such as photos and contacts from their own personal devices.
What are the options when users do not use MDM:
Option 1: block access if not using a managed device, which makes sense from a security perspective but not so good from a productivity perspective.
Option 2: allow user to access using a thin client, for example OWA for email where the user enters the OWA URL into their browser and then their credentials, the email is stored on the server rather than on the client. The risk with this approach is:
- on a personal device many users do not use PIN or encrypt the device, anyone may be able to access the device if stolen
- user often saves the credential on their personal device so they don’t have to enter the password each time, this will also allow unauthorised users to see the previously browsed sites such as OWA.
- while Multifactor Authentication (MFA) can be enabled, if the smart phone is the 2nd factor, effectively the phone factor is bypassed when the same device is compromised.
Option 3: utilise Mobile Application Management (MAM). The security policy is applied at the application level instead of the device level. Data wipe will now be performed at the application level (AKA selective wipe). This will remove the corporate data while leaving the personal data intact.
MAM with Microsoft Intune allows a company to control:
- cut/copy/paste restrictions
- prevent “save as”
- prevent cloud backup
- jailbroken or rooted devices
- PIN requirement
- selective wipe of the application data
The screenshot below illustrates some of the security options available:
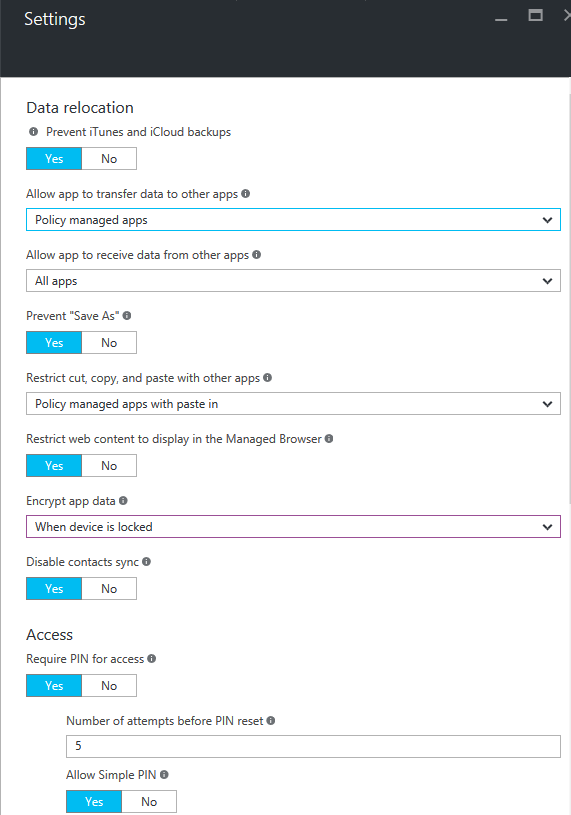
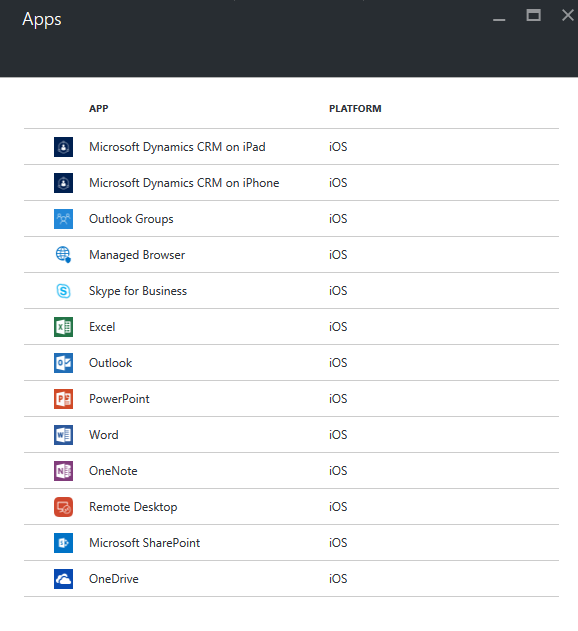
Some of MAM supported apps are show below, for the complete list go to Microsoft Intune Partners page.
To deploy Intune MAM, users will need either Intune or EMS licenses.
It is also possible to deploy both Intune MDM and MAM at the same time. A scenario for this is to allow corporate devices to be managed by MDM, and offering BYOD users a choice between MDM and MAM.
Microsoft TechNet has further information on Intune MAM
Create and deploy mobile app management policies with Microsoft Intune

This is the way forward, John Yu! 😉 😉
what about users that have both corporate and byod devices?
They will get to use both options (assuming both MAM and MDM are configured in Azure and the Intune portal)
– Corporate Device enrols via the Intune App, then it gets the MDM option
– BYOD does NOT enrol in Intune App, the Apps with get the MAM option
As we know business is mobile now and various organizations are providing devices to their employee for their work to be done. So MDM tools are the best choice for any company to set up employees’ smartphones and tablets with the apps they require. This can include a mix of commercially available business relevant apps approved by IT and apps developed in-house, specifically for the organization.
Currently, we have implemented MobiLock Pro as our MDM solutions to control & manage our devices at the workplace which is quite an effective solution for various small & large businesses.
Under wirelesssupport MDM solutions there is a problem which one is better BYOD or CYOD or COPE?
Now the trend of enterprise mobility is booming in the market and every business looking to invest in EMM as it provides them strategy to secure and manage the devices used during work hours.