Free/busy Exchange hybrid troubleshooting with Microsoft Edge
Those of you who have configured Exchange hybrid with Office 365 before know that free/busy functionality can be troublesome at times and not work correctly.
Instead of searching through Exchange logs I found that you can pin point the exact error message through Microsoft Edge to assist with troubleshooting.
To do so;
- Open Microsoft Edge and login to Office 365 OWA (https://outlook.office365.com/owa) with an Office 365 account
- Create a new meeting request
- Press F12 to launch developer tools
- Conduct a free/busy lookup on a person with a mailbox on-premises
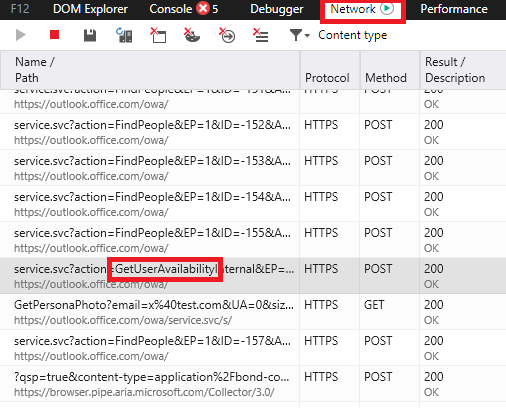
- Select the Network tab
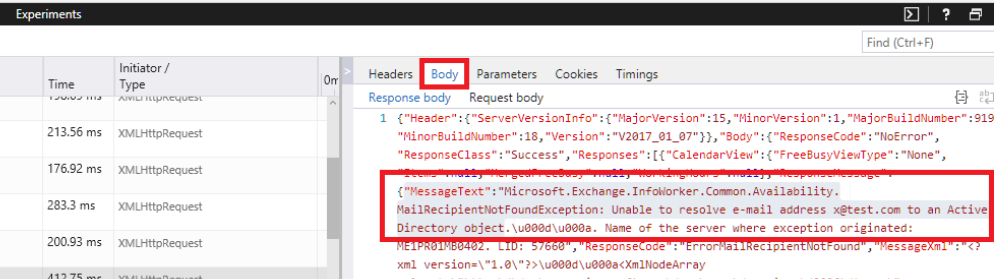
- Select the entry with “GetUserAvailability”
- Select the body tab (on the right hand side)
- The MessageText element will display the exact error message