What is Azure Key Vault
Azure Key Vault helps safeguard cryptographic keys and secrets used by cloud applications and services. By using Key Vault, you can encrypt keys and secrets (such as authentication keys, storage account keys, data encryption keys, .PFX files, and passwords) using keys protected by hardware security modules (HSMs).
Key Vault streamlines the key management process and enables you to maintain control of keys that access and encrypt your data. Developers can create keys for development and testing in minutes, and then seamlessly migrate them to production keys. Security administrators can grant (and revoke) permission to keys, as needed.
Anybody with an Azure subscription can create and use key vaults. Although Key Vault benefits developers and security administrators, it could be implemented and managed by an organization’s administrator who manages other Azure services for an organization. For example, this administrator would sign in with an Azure subscription, create a vault for the organization in which to store keys, and then be responsible for operational tasks, such as:
- Create or import a key or secret
- Revoke or delete a key or secret
- Authorize users or applications to access the key vault, so they can then manage or use its keys and secrets
- Configure key usage (for example, sign or encrypt)
- Monitor key usage
This administrator would then provide developers with URIs to call from their applications, and provide their security administrator with key usage logging information.
( Ref: https://docs.microsoft.com/en-us/azure/key-vault/key-vault-whatis ).
Current Scenario of the Key Vault.
In the current scenario , we are utilizing Key Vault for the provisioning of arm resources. Instead of any username and passwords , the template only contains references to these values stored in Azure Key Vault.
Theses secrets are extracted while the resources are being deployed using the template and the parameter file together.
Utilizing the Key Vault.
The following tasks are involved in utilizing the Key Vault
- Creating the key Vault.
- Adding Keys and Secrets in the Vault
- Securing the Key Vault
- Referencing Keys
Creating a Key Vault
Step 1 : Login to Azure Portal and click on All Services and select Key Vault
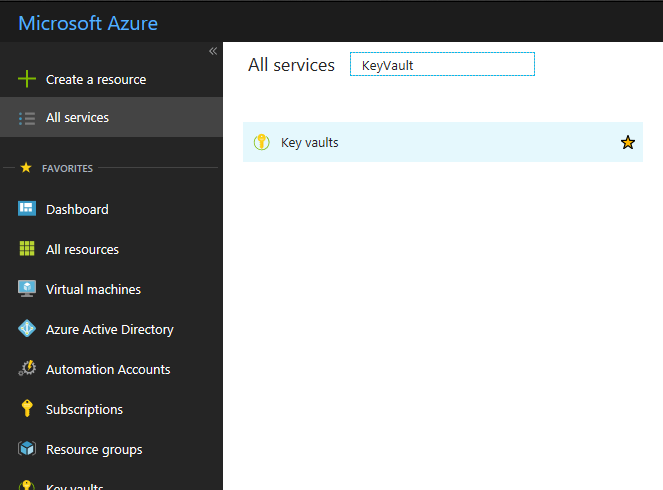
Step 2 : Click on Add and enter the following details and click on Create
- Key Vault Name
- Subscription
- Resource Group
- Pricing Tier
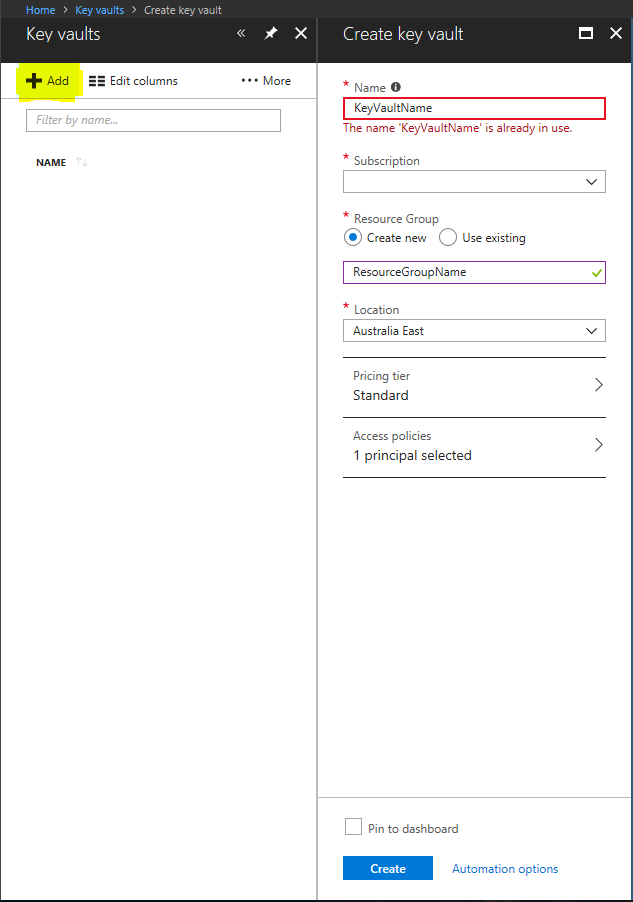
Step 3 : Select the Key Vault Name
Step 4 : Select Secrets
Step 5 : Click on Generate/Import
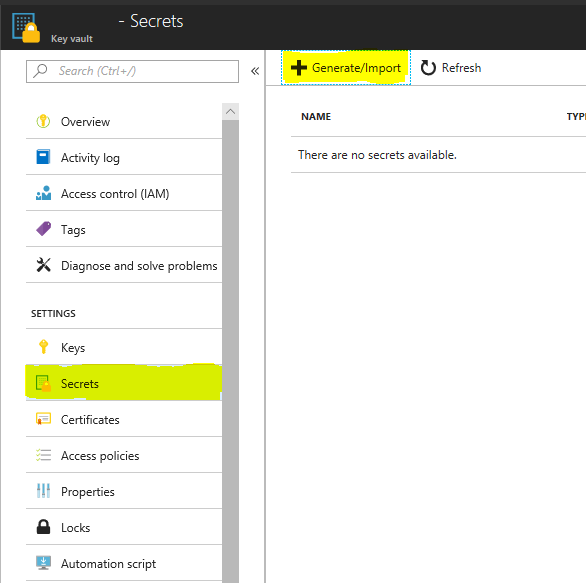
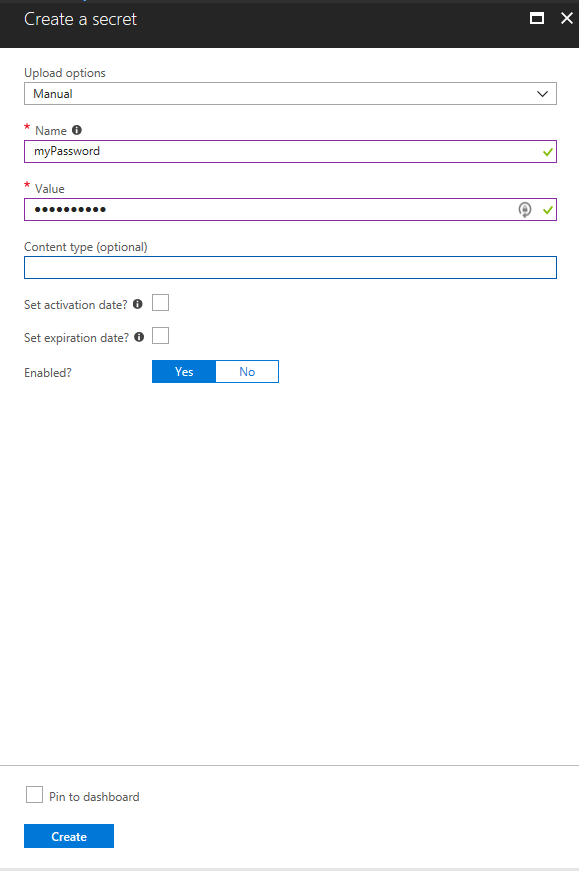
Step 6: Select Manual in upload options
Step 7: Enter the following information.
- Name of the Secret ( Like MyPassword )
- Value of the Secret ( example P@ssword1)
- Set Activation Date ( If required )
- Set Expiration Date ( If required)
Step 8 : Select Yes on the Enabled option
Step 9: Click on Create
Securing the Key Vault
Step 1: Select the Newly created Key Vault
Step 2: Select Access Policies
Step 3 : Select click to show advanced access policies
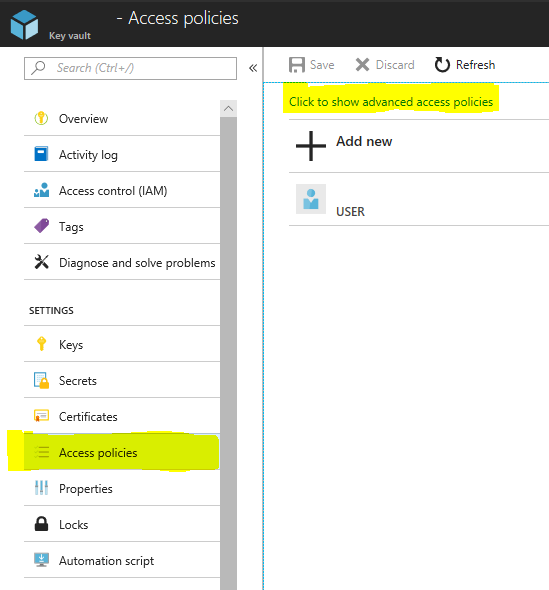
Step 4: Select the checkboxes as shown in the snapshot below.
Step 5: Click on Add New
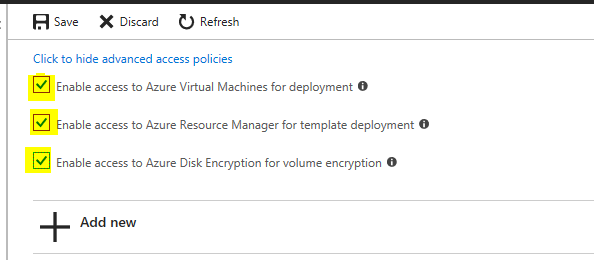
Step 6: Select Secret management in the configure from template option.
Step 7: Select the Principal ( name of the resource which needs access to the secret.)
Step 8: Select the permissions required from the Secret Permissions
Step 9: Select OK.
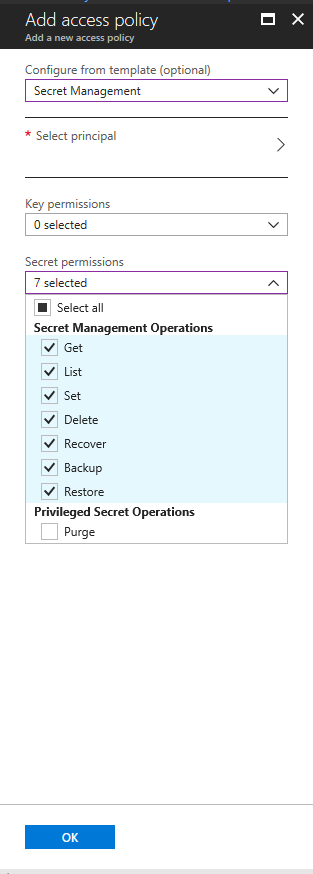
Referencing the Secrets.
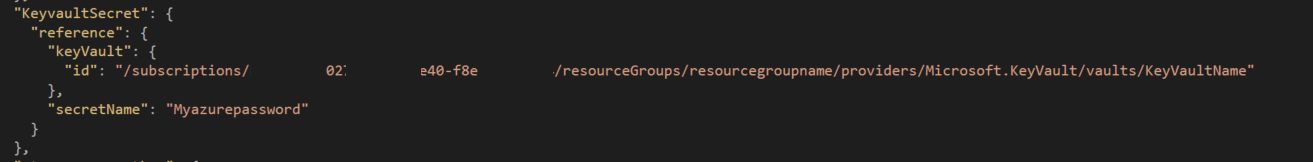
Currently we are referencing the secrets stored in the Key vault using the arm templates.
A parameter type “securestring” is created in the parameter section of the arm template armtemplate.json file
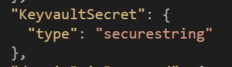
We add the parameter in the parameters file of the template armtemplate.parameters.json with the following details
- ID of the key vault ( resource ID of the KeyVault under the properties section )
- name of the secret to extract (Mypassword)
Summary:
Based on the above example , we achieved the following
- Secure information ( usernames and passwords ) are not mentioned anywhere in the template or the parameter files
- The secure values will be acquired when the template is running
- The values are only accessible to those who have access to the Key vault.
