Introduction
This blog is Part 01 of a 02 part series related to custom VPC configurations
Part 01 discusses the following scenario
- Creating a VPC with 02 subnets ( Public and Private )
- Creating a bastion host server in the public subnet
- Allowing the Bastion host to connect to the servers in the Private Subnet using RDP.
Part 02 will discuss the following
- Configuring NAT Instances
- Configuring VPC Peering
- Configuring VPC flow Logs.
What is a VPC
VPC can be described as a logical Datacenter where AWS resources can be deployed.
The logical datacenter can be connected to your physical datacenter through VPN or direct connect. Details (https://blog.kloud.com.au/2014/04/10/quickly-connect-to-your-aws-vpc-via-vpn/)
This section deals with the following tasks.
- Creating the VPC
- Creating Subnets
- Configuring Subnets for internet access
1 Creating the VPC
The following steps should be followed for configuring VPC. we can use the wizard to create a VPC but this document will focus on the detailed method where every configuration parameter is defined by the user.
Step 01.01 : Logon to the AWS console
Step 01.02 : Click on VPC
Step 01.03 : Select Your VPCs
Step 01.04 : Select Create VPC
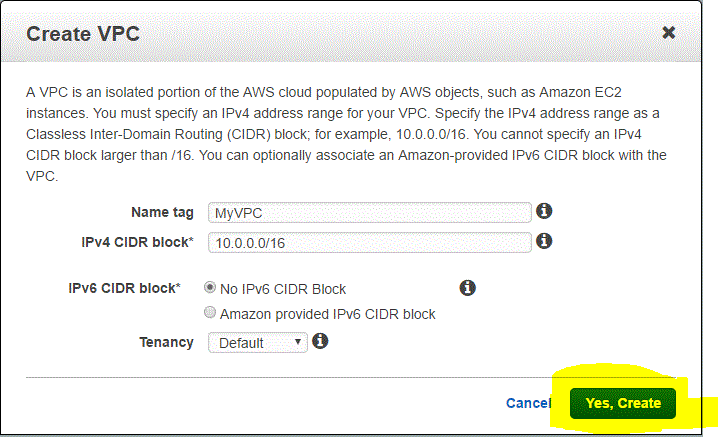
Step 01.05 Enter the following details in the Create VPC option
- Enter the details of the Name Tag
- Enter the CIDR Block. keep in mind that the block size cannot be greater that /16.
Step 01.06: Click on Yes,Create
We have now created a VPC. The following resources are also created automatically
- Routing table for the VPC
- Default VPC Security Group
- Network ACL for the VPC
Default Routing Table ( Route Table Id = rtb-ab1cc9d3)
Check the Routing table below for the VPC. If you check the routes of the route table, you see the following
- Destination :10.0.0.0/16
- target : Local
- Status: Active
- Propagated: No
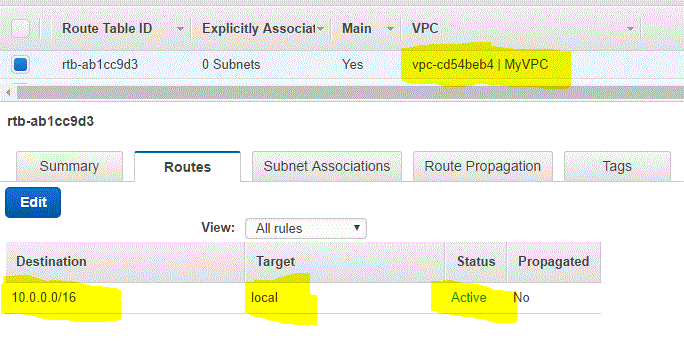
This route ensures that all the subnets in the VPC are able to connect with each other. All the subnets created in the VPC are assigned to the default route table therefore its best practice not to change the default route table. For any route modification, a new route table can be created and assigned to subnets specifically.
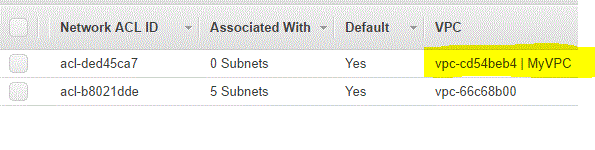
Default Network Access Control List ( NACL id= acl-ded45ca7)
Mentioned below is the snapshot of the default NACL created when the VPC was created.
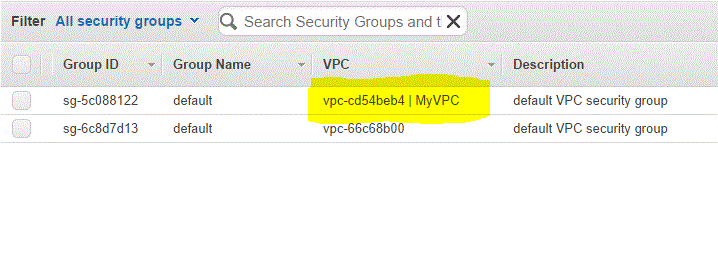
Default security group for the VPC ( Group id = sg-5c088122)
Mentioned below is the snapshot of the default Security Group created when the VPC was created.
Now we need to create Subnets. Keeping in mind that the considered scenario needs 02 subnets ( 01 Private and 01 Public ).1.
2 Creating Subnets
Step 02.01 : Go to the VPC Dashboard and select Subnets
Step 02.02 : Click on Create Subnet
Step 02.03: Enter the following details in the Create Subnet window
- Name Tag: Subnet IPv4 CIDR Block ) – “Availability Zone” = 10.0.1.0/24 – us-east-1a
- VPC : Select the newly created VPC = vpc-cd54beb4 | MyVPC
- Availability Zone: us-east-1a
- IPv4 CIDR Block :10.0.1.0/24
Step 02.04: Click on Yes,Create
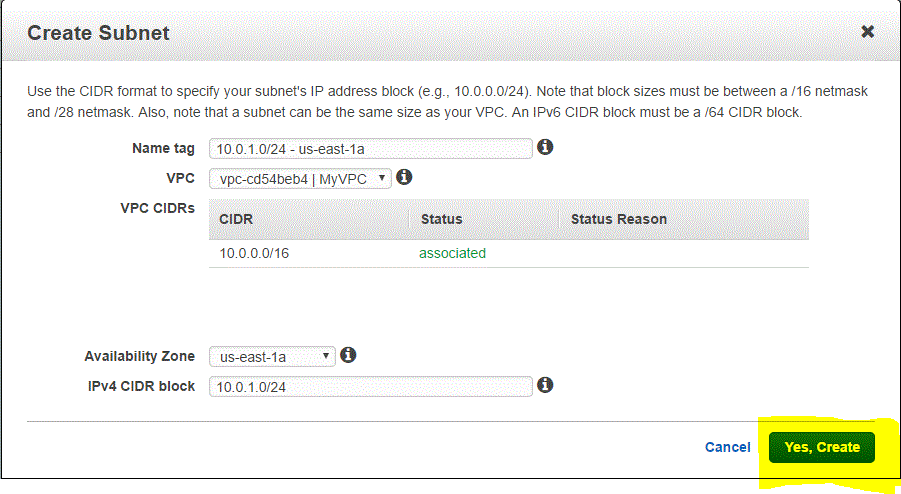
Now we have created subnet 10.0.1.0/24
We will use the same steps to create another subnet. 10.0.2.0/24 in availability zone us-east-1b
- Name Tag: Subnet IPv4 CIDR Block ) – “Availability Zone” = 10.0.2.0/24 – us-east-1b
- VPC : Select the newly created VPC = vpc-cd54beb4 | MyVPC
- Availability Zone: us-east-1b
- IPv4 CIDR Block :10.0.2.0/24
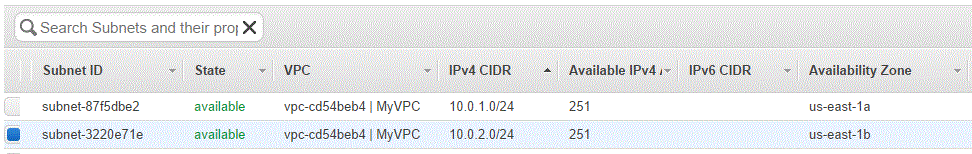
3 Configuring subnets
Now that we have 02 subnets and we need to configure the 10.0.1.0/24 as the public subnet and 10.0.2.0/24 as the private subnets. The following tasks need to be performed for the activity
- Internet Gateway creation and configuration
- Route table Creation and configuration
- Auto Assign Public IP Configuration.
3.1 Internet gateway Creation and Configuration ( IGW Config )
Internet gateways as the name suggest provide access to the internet. They are assigned to VPC and routing table is configured to direct all internet based traffic to the internet gateway.
Mentioned below are the steps for creating and configuring the internet gateway.
Step 03.01.01 : Select Internet Gateways from the VPC dashboard and click on Create Internet Gateway
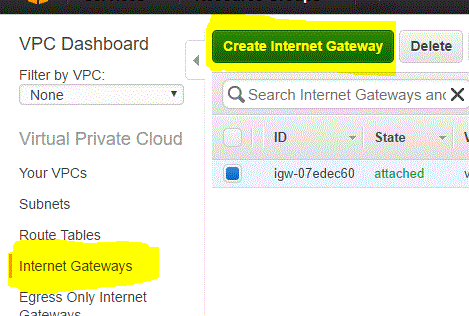
Step 03.01.02 : Enter the name tag and click on Yes,Create
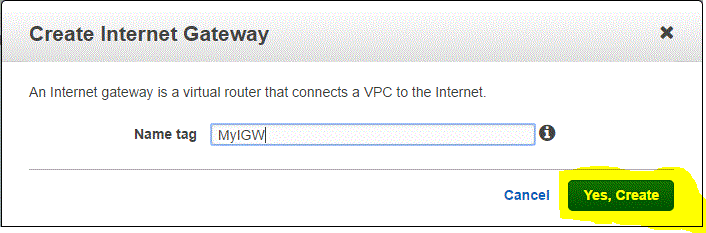
The internet gateways is created but not attached to any VPC.( internet gateway Id = igw-90c467f6)
Step 03.01.03: Select the Internet Gateway and click on Attach to VPC
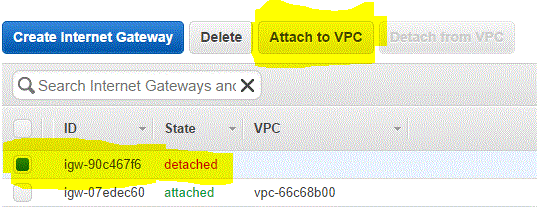
Step 03.01.04 : Select your VPC and click on Yes,Attach
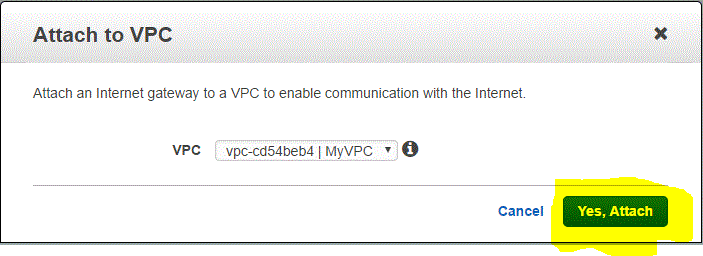
We have now attached the Internet Gateway to the VPC. Now we need to configure the route tables for internet access.
3.2 Route Table creation and Configuration ( RTBL Config)
A default route table ( with id rtb-ab1cc9d3) was created when the VPC was created. Its best practice to create a separate route table to internet access.
Step 03.02.01 : Click on the Route Table section in the VPC Dashboard and click Create Route table
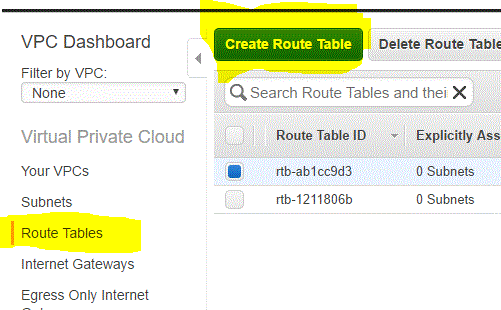
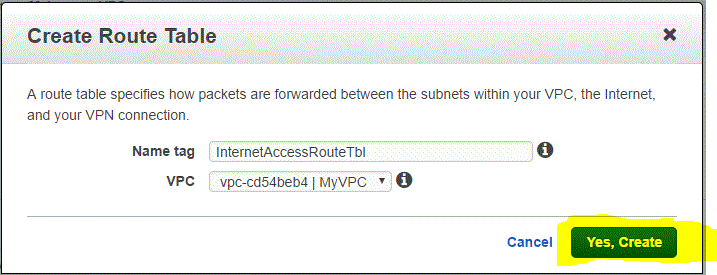
Step 03.02.02: Enter the following details in the Create Route Table window and click on Yes,Create
- Name tag: Relevant Name = InternetAccessRoutetbl
- VPC : Your VPC = vpc-cd54b3b4 | MyVPC
Step 03.02.03 : Select a newly created Route table( Route Table Id = rtb-3b78ad43 | InternetAccessRouteTbl) and Click Routes and then Edit
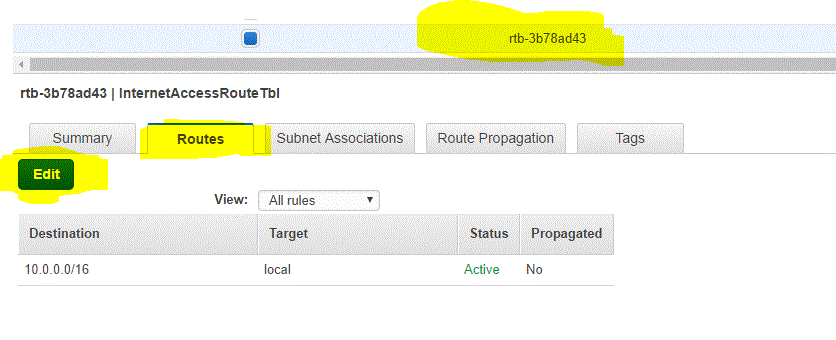
Step 03.02.04: Click on Add Another Route
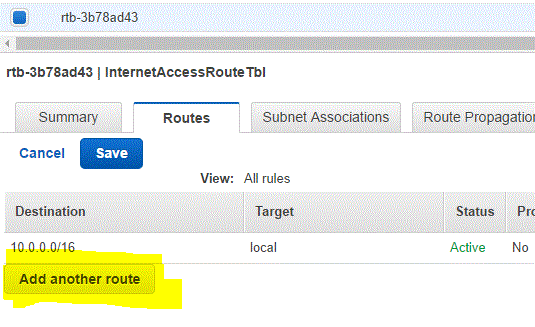
Step 03.02.05 : Enter the following values in the route and click on Save
- Destination: 0.0.0.0/0
- Target : Your Internet Gateway ID = igw-90c467f6 ( in my case )
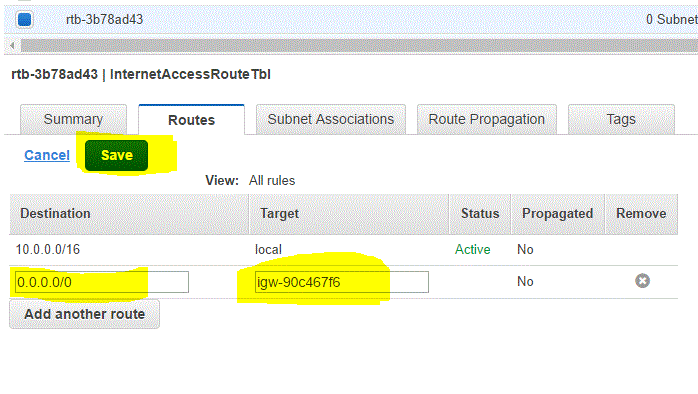
Route table needs subnet associations. The subnets which we want to make Public should be associated with the route table. In our case, we would associate Subnet 10.0.1.0/24 to the route table.
Step 03.02.06: Click on Subnet Associations
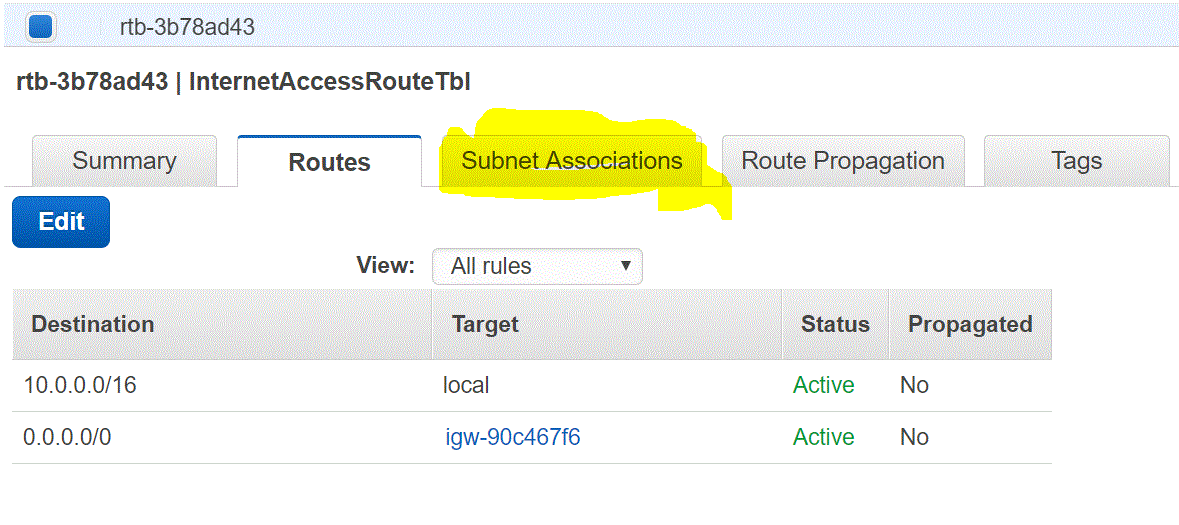
You should be able to see the message “You do not have any subnet associations”
Step 03.02.07: Click on Edit
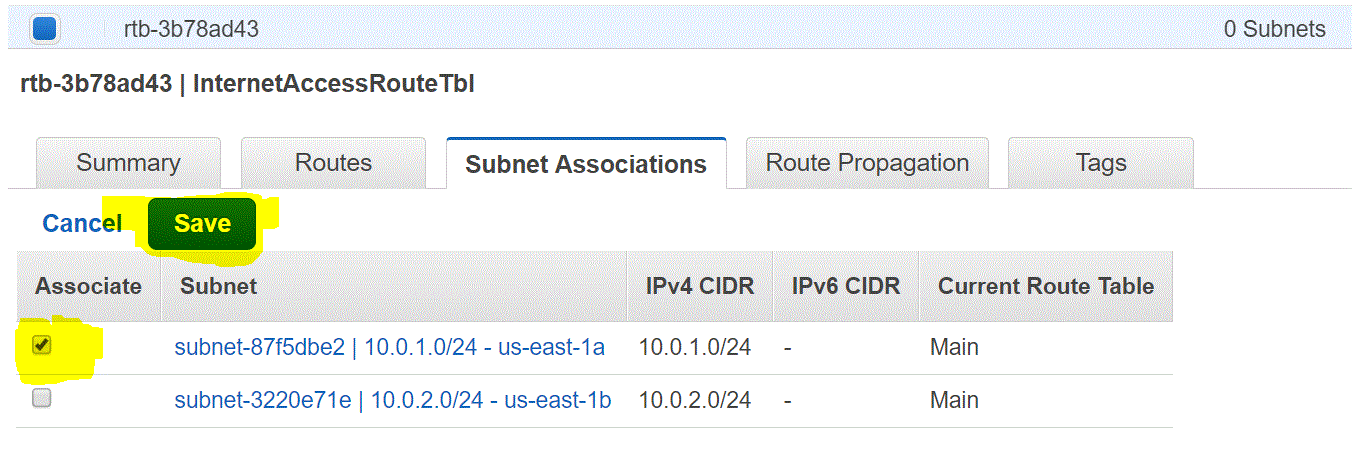
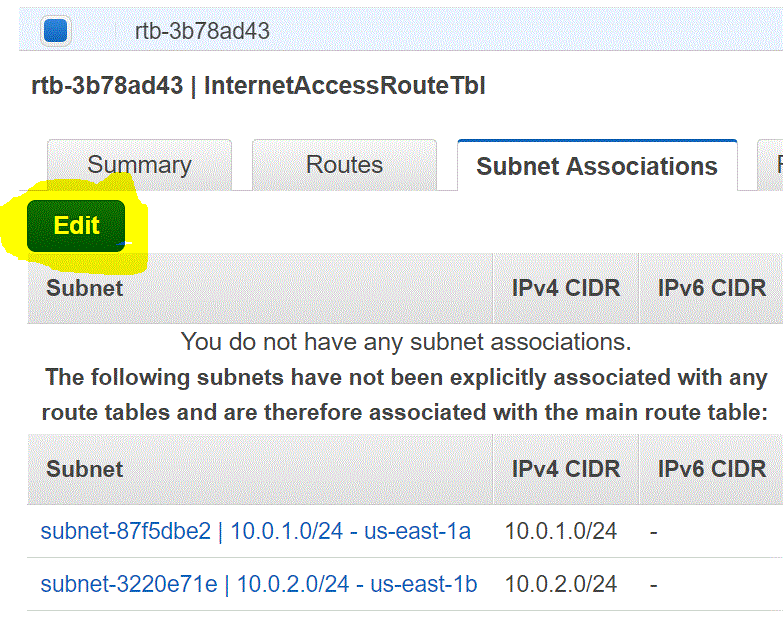 Step 03.02.08: Select the subnet you want to configure as a Public Subnet. In our case 10.0.1.0/24 and Click on Save
Step 03.02.08: Select the subnet you want to configure as a Public Subnet. In our case 10.0.1.0/24 and Click on Save
03.03 Auto Assign Public IP Configuration
Both the subnets created ( 10.0.1.0/24 and 10.0.2.0/24) will not assign public IP addresses to the instances deployed in them as per their default configuration.
We need to configure the public subnet ( 10.0.1.0/24 ) to provide Public IPs automatically.
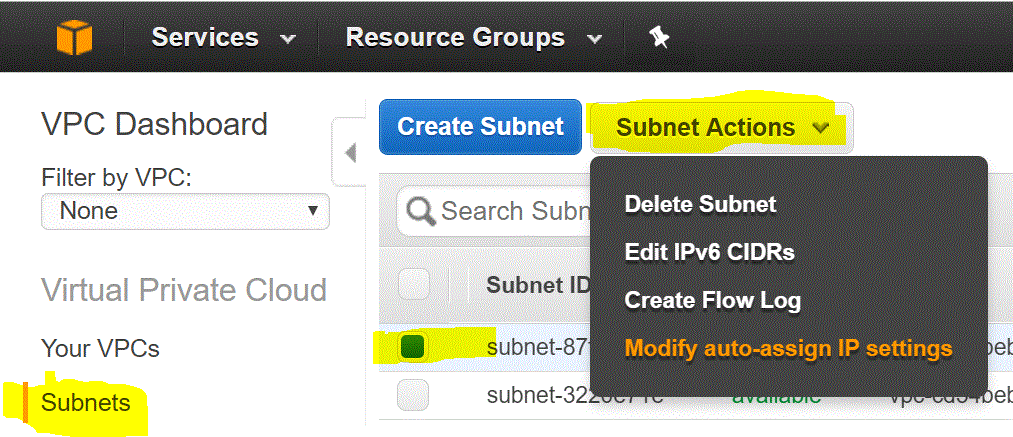
Step 03.03.01: Go to the Subnets section in the VPC dashboard.
Step 03.03.02: Select the Public Subnet
Step 03.03.03: Click on Subnet Actions
Step 03.03.04: Select Modify auto-assign IP Settings
Step 03.03.05: Check the Enable Auto-assign Public IPv4 Addresses in the Modify Auto-Assign IP Settings Window and click on Save
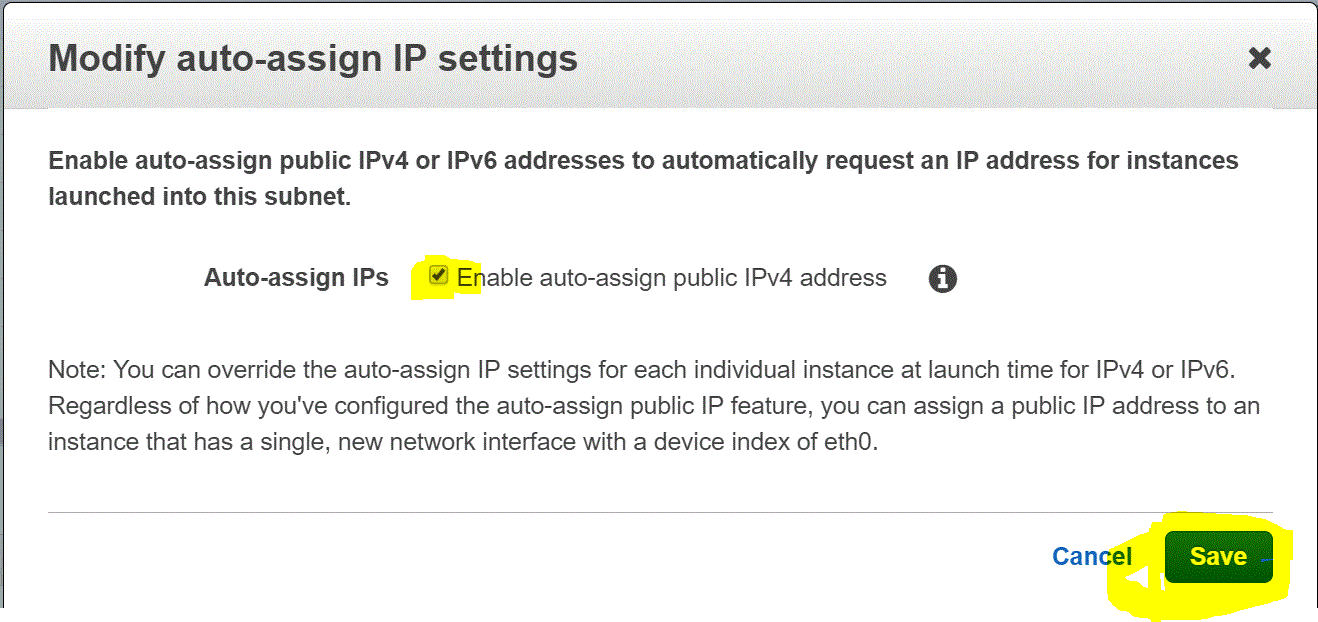
After this configuration, any EC2 instance deployed in the 10.0.1.0/24 subnet will be assigned a public IP.
4 Security
security group acts as a virtual firewall that controls the traffic for one or more instances. When you launch an instance, you associate one or more security groups with the instance. You add rules to each security group that allow traffic to or from its associated instances. You can modify the rules for a security group at any time; the new rules are automatically applied to all instances that are associated with the security group. When we decide whether to allow traffic to reach an instance, we evaluate all the rules from all the security groups that are associated with the instance.
We will create 02 security groups,
- Public-Private ( Will contains access rules from Public Subnet to Private Subnet )
- Internet-Public ( will contains the ports allowed from the internet to the Public Subnet )
Step 4.1Â : Click on Security Groups in the Network and Security section
Step 4.2 : Click on Create Security Group
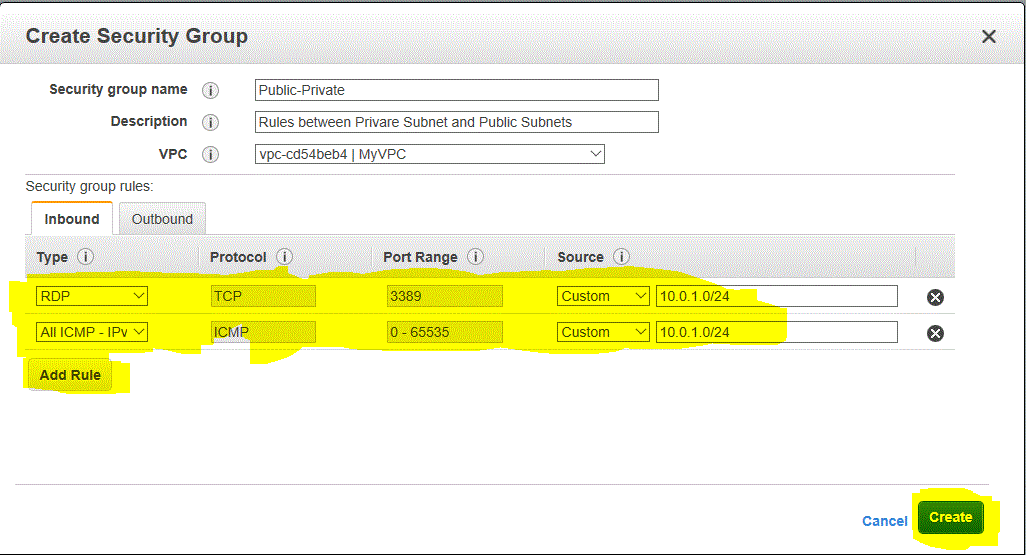
Step 4.3 : Enter the following details on the Create Security group Window and click on Create
- Security Group Name : Public-Private
- Description : Rules between Private subnet and Public subnets
- VPC : Select the VPC we created in the exercise.
- Click on Add Rules to Add the following rules
- Type = RDP , Protocol = TCP , POrt Range = 3389 , Source = Custom : 10.0.1.0/24
- Type = All ICMP – IPV4, Protocol = ICMP , Port Range = 0 – 65535 , Source = Custom, 10.0.1.0/24
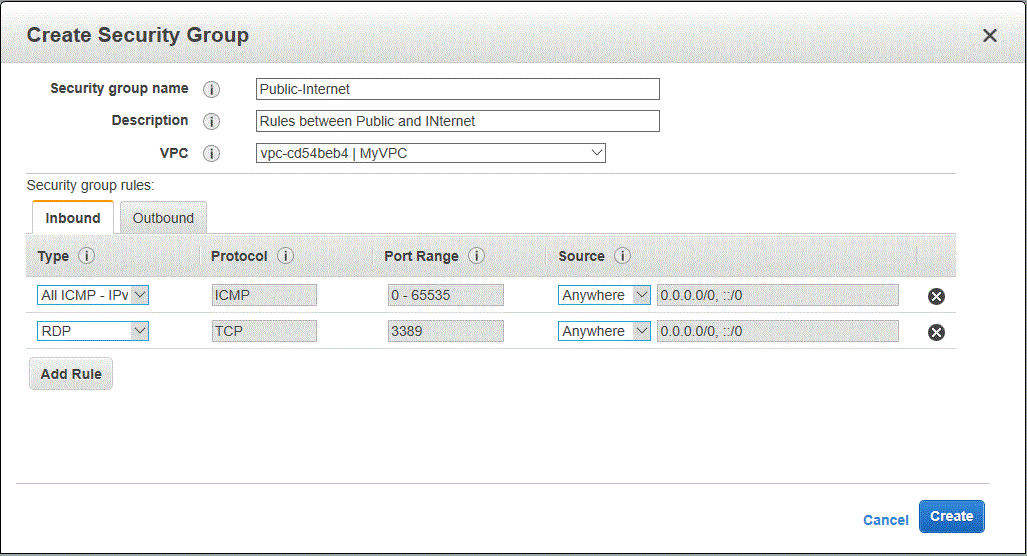
Step 4.4 : Enter the following details on the Create Security group Window and click on Create
- Security Group Name : Public-Internet
- Description : Rules between Public and the internet
- VPC : Select the VPC we created in the exercise.
- Click on Add Rules to Add the following rules
- Type = RDP , Protocol = TCP , POrt Range = 3389 , Source =Anywhere
- Type = All ICMP – IPV4, Protocol = ICMP , Port Range = 0 – 65535 , Source = Anywhere
4 EC2 installation
Now we will deploy 02 EC2 instances . One EC2 Instances Named PrivateInstance in the 10.0.2.0/24 subnet and one instance named PublicInstance in the 10.0.1.0/24 subnet.
Public Instance Configuration :
- Instance Name : Public Instance
- Network : MyVPC
- Subnet : 10.0.1.0/24
- Auto-Assign Public ip : Use subnet setting ( enabled )
- Security Group : Public-Internet security group
- IAM Role : As per requirement
Private Instance Configuration :
- Instance Name : Private Instance
- Network : MyVPC
- Subnet : 10.0.2.0/24
- Auto-Assign Public ip : Use subnet setting ( disabled)
- Security Group : Public-Private security group
- IAM Role : As per requirement
Once the deployment of the EC2 instance is complete, you can connect to the PublicInstance through RDP and from there connect further to the Private instances.
