I have been working for an organisation who had recently migrated to Exchange Online protection (EOP), and we had found that some of his important emails, from a legitimate email source, were getting blocked.
Upon investigation it turns out that a week before the customer’s organisation was hit by a Zero-Day virus which resulted in spoofed emails coming through and landing in the end user mailboxes. This resulted into a bit of chaos and a decision was taken to modify the Bulk email threshold (BCL) to a tighter level. Further investigation with the customer revealed that after setting BCL value to 5 the customer was planning to use Spam Notification emails to release quarantined messages from junk folder with the expectation that once they are marked as “Not Junk Email” in the notification, the sender address will automatically be White Listed by EOP.
The approach did not work and important emails sent from legitimate sources (some were customer orders) got trapped in quarantine folder and kept getting trapped even though the end users were releasing them into their inboxes and marking them as Not Junk. The whole idea of stopping emails at a global level and then allowing at granular level just fell apart.
Now let’s review the whole scenario again and try to clarify some caveats in between. Let’s start with BCL rating change. This was originally set to 7 which is a default value and if you go to this link Bulk Complaint Level values it explains the different threshold values for Bulk email in detail. An important thing to note here is that there is no standard value for every organisation. BCL will vary from organisation to organisation based on several factors and this is something every organisation has to learn over a period of time. To find the sweet spot where only junk email gets blocked and rest flows in.
The second important concept to understand here is the EOP spam notification. General understanding is that once you mark the email as not junk from quarantine mailbox, then it should always land in the inbox next time, just as we do in the Hotmail. However, in practice this is not the case. EOP only uses user input to pass on to Microsoft as an information to record. EOP just learns the user actions here and won’t necessarily take action. This input will vary from user to user, and EOP will only use it to learn about the reputation of the sender. As you can see in the below screenshot, Microsoft is using user input as information to be used in Analysis, and nothing else.

So what is the right thing to do to allow a sender land his mail in your inbox? The answer is in the below screenshot which provides you a tip which we most of the time we ignore but actually gives us a reasonable direction in terms of adopting the right method to ensure legitimate senders don’t get blocked.
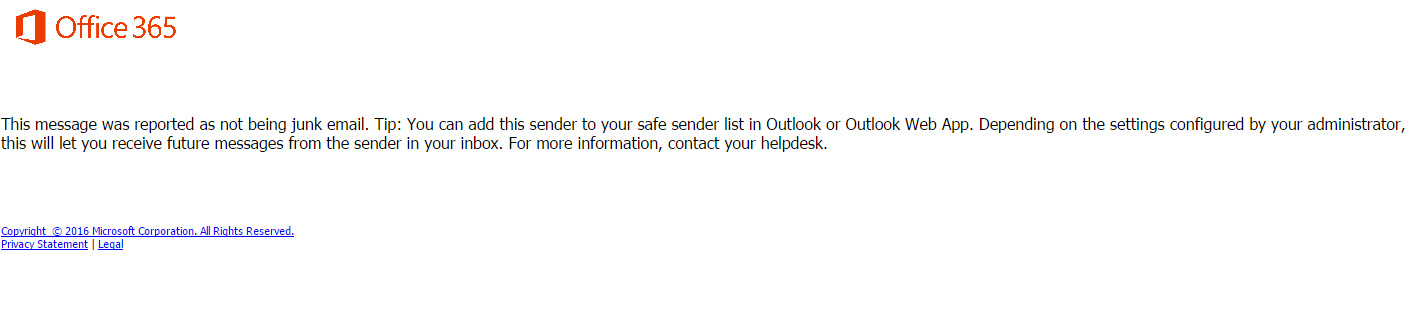
Yes, it’s the safe sender list which is maintained by every user. Though it sounds conventional and old school where every user is responsible to maintain his/her own allow list for their mailboxes but in actual fact it gives the real time protection with accurate data. Moreover, the safe sender allow/block list take precedence over EOP rules and policies set by administrator. This means that even if a sender is blocked by the administrator, if that sender is in the safe sender list of a user then this user will be able to receive emails explicitly from this sender while it remains blocked for rest of the organisation.
Talking about safe sender and blocked sender lists, your next argument would be as an administrator how can you ensure that it is managed by every user and you have control over it. To address this first step would be to actually educate the people about it and develop the understanding of how the whole process works. Secondly, you can leverage PowerShell to set up this list on a per user basis as well as for bulk users. Below are the PowerShell commands:
set up safe senders and blocked senders for a single user
Set-MailboxJunkEmailConfiguration -Identity <user@contoso.com> -BlockedSendersAndDomains “<domainA>.com”, “<user>@<domainB>.com”,”…” -TrustSendersAndDomains “<domainC>.com”,”<user>@<domainD>.com”,”…”
set up safe senders and blocked senders in bulk
Get-Mailbox | Set-MailboxJunkEmailConfiguration -BlockedSendersAndDomains “<domainA>.com”,”user@<domainB>.com”,”…” -TrustedSendersAndDomains “<domainC>.com”,”user@<domainD>.com”,”…”
A more detailed article for the above commands can be found here set up safe senders and blocked senders in Office 365
Lastly, I would like to discuss here how EOP policies and filters work alongside the safe/blocked senders list. EOP policies and filter provide the first level of defence at a broader level for any organisation. It contains all the known spam sources, black listed IPs/domains and bulk spam sources. It also provides protection against malware by blocking malicious attached files. The major benefit is that almost all spam is blocked outside the organisation’s network and does not overload or consume network resources.
To conclude the above discussion, I would like to lay down following guidelines when thinking in terms of protecting an organization from spam and malicious emails.
- EOP provides protection at the organisational level and follows industry standards and best practices to safe guard against known spam and malicious mail sources.
- Safe sender/block list provides a second, and more adjustable, level of control.
- Spam notifications sent by EOP only collect and send user data to the EOP engine and won’t necessarily allow/block the sender.
- Mail protection is a learning process for any organisation and requires updating the system regularly as the environment changes and learns.
- End user education is very critical in terms of them playing their role to help the organisation control email spam.
