I’ve been using Azure AD Identity for quite a while now. I thought it would be good to share the summary of Azure AD Identity features and gather some feedbacks.
Azure AD Identity
Azure Active Directory: A comprehensive identity and access management cloud solution for your employees, partners, and customers. It combines directory services, advanced identity governance, application access management, and a rich standards-based platform for developers.
Identity and access management License option: Azure Active Directory Premium P2 (E5), P1 (E3)
“Identity as the Foundation of Enterprise Mobility”
Identity and access management
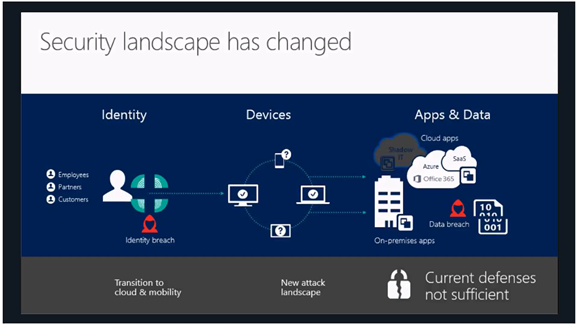
Protect at the front door: innovative and advanced risk-based conditional accesses, protect your data against user mistakes, detect attacks before they cause damage
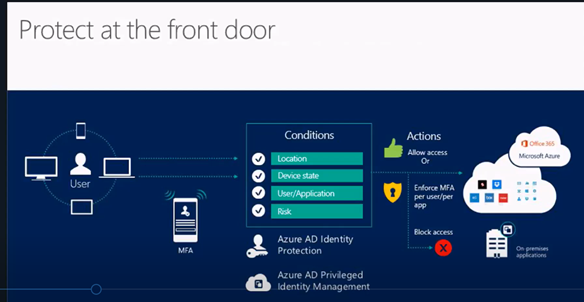
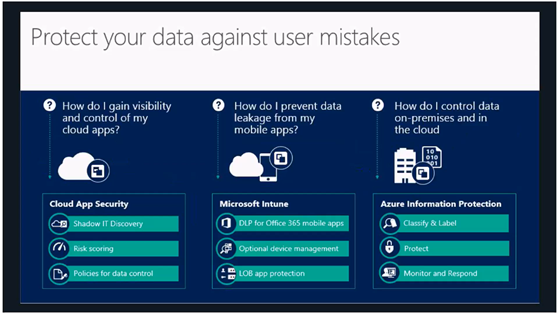
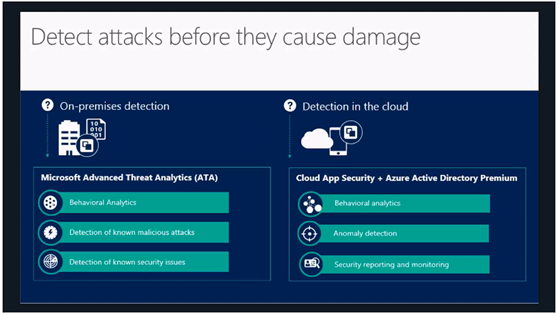
Identity and access management in the cloud:
- 1000s of apps, 1 identity: Provide one persona to the workforce for SSO to 1000s of cloud and on-premises apps.
- Enable business without borders: Stay productive with universal access to every app and collaboration capability.
- Manage access at Scale: Manage identities and access at scale in the cloud and on-premises, advanced user lifecycle management and advanced identity monitor tools
- Cloud-powered protection: Ensure user and admin accountability with better security and governance
Azure AD portal:
Configure users & groups, Configured SaaS applications identity, configure on-prem applications with Application proxy, license management, password reset, password reset notifications, password reset authentication methods, company branding, whether users can register/consent applications, whether users can invite external contacts, whether guest can invite external contacts, whether users can register devices with Azure AD, whether require MFA, Define whether use pass-through authentication or federation authentication.
Azure AD application integration:
3 types of applications integration:
- LOB applications: using Azure AD for authentication
- SaaS applications: configure SSO
- Azure AD Application proxy: we can publish on-prem applications to internet through Azure AD application proxy.
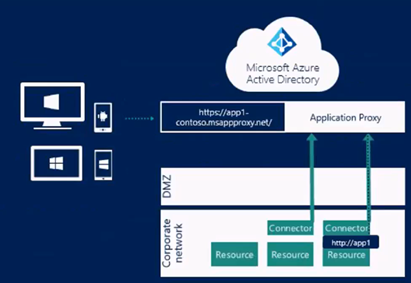
Inbound/outbound user provisioning to SaaS apps
User Experience with Integrated apps: Access Panel https://myapps.microsoft.com. Custom Branding? Load by appending your organization’s domain https://myapps.microsoft.com/company_domain_name. From Myapps, users can: change PW, Edit PW reset, MFA, view account details, view launch apps, self-management groups. Admins can configure apps to be self-service -users add apps by themselves.
Authentication (Front End & Back End) & Reporting (reporting access & alerts, reporting API, MFA)
|
Front End Authentication |
Back End Authentication |
Pass-thru authentication:
|
Pass-thru authentication:
|
|
Pre-Authentication
|
Kerberos/IWA
|
Azure AD Connect health
Monitor & Report on ADFS, AAD Sync, ADDS. Advanced logs for configuration troubleshooting.
Azure Identity protection (Azure AD premium P2)
- AIP dashboard is a consolidated view to examine suspicious user activities and configuration vulnerabilities
- Remediation recommendations
- Risk Severity calculation
- Risk-based policies for protection for future threats
If user is at risk, either we can block users or we can trigger MFA automatically
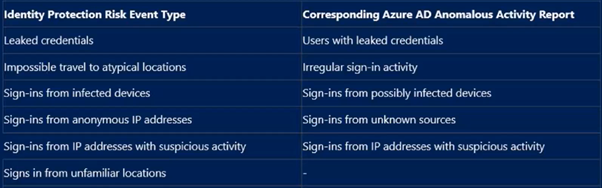
AIP can help to identify spoof attack happening or leak credentials, suspicious sign in activities. infected devices, configurations vulnerabilities, for example, when a user signed in from unfamiliar location, then we can trigger to reset his/her password or we can use user risk condition to allow user access to corporate resources with password change or block access straight away. Alternatively, we can configure the alert to send an approval request to admin.
Identity protection risk types and reports generated:
Azure AD privileged Identity Management
For examples, I am on leave for 2 days and I want my colleagues to become global admin for only two days. if I come back from leave and forget to remove the global admin permissions from that colleagues, he will still be global admin, this will be put company at risk, because potentially either global admin password can be compromised.
Just in time administrative access, we can use this to give only has 2 days “global admin” access
Securing Privileged access: just in Time administration
- Assume breach of existing AD forests may have occurred
- Provide privileged access through a workflow
- Access is limited in time and audited
- Administrative account not used when reading mail/etc.
Result = limited in time & capability

Thanks for this nice overview, great article