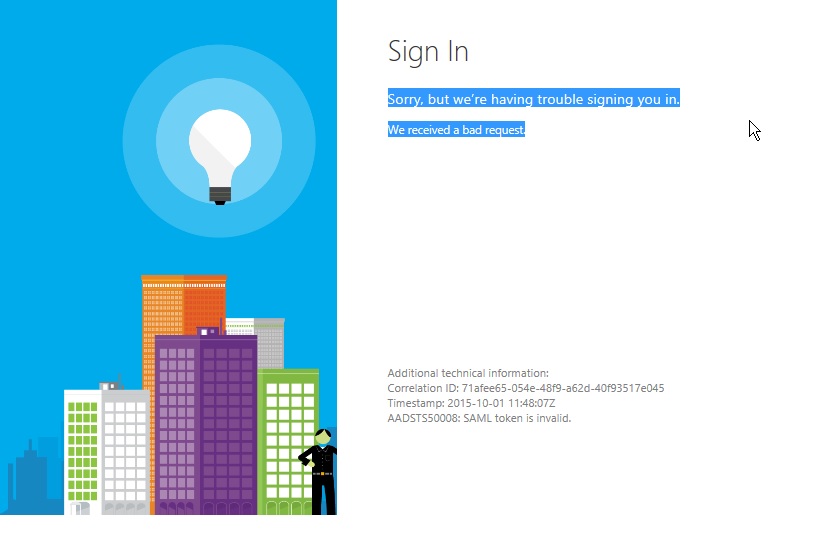
Office 365 – AADSTS50008: SAML token is invalid
If you’ve made it to this post because you are troubleshooting your AD FS sign in with Office 365 due to “AADSTS50008: SAML token is invalid” I still recommend you do all the standard troubleshooting steps provided in this article below the image:
 https://support.microsoft.com/en-us/kb/3015526
https://support.microsoft.com/en-us/kb/3015526
Generally speaking, if you’re getting issued a token from your AD FS server and Microsoft’s STS is stopping you from logging in, it would be because of your token signing certificate:
… [Keep reading] “Office 365 – AADSTS50008: SAML token is invalid”Has your Token-Signing Certificate changed since you last told Microsoft?
