I was recently working on a project implementing Microsoft Advanced Threat Protection (ATP) on Office 365 services for one of our clients and have come across a few lessons learnt that hopefully might become useful for others out there & also looking into this great new feature from Microsoft!
LESSON 1: ATP Anti-Phishing Policy Not Working due to existing Spam policies
We created a new ATP Anti-Phishing policy where we added a bunch of Executive team users to protect them from being impersonated by attackers under “Add Users to Protect” setting. Unfortunately, the policy did not work as expected and we were still able to spoof users defined in this policy in spite of adding them explicitly under the policy settings.
What we found was that the Exchange Online SMTP verified domain was in the “Allowed Domain” in their “Spam Filter Policy” which overrides the settings in Anti-Phishing policy and hence any spoofed messages would skip filtering and will get delivered.
Removing the SMTP domain as an “Allowed Domain” under “Spam Filter Policy” fixed the issue and the ATP Ant-Phishing policy blocked any spoofed messages from that point on.
This highlights the importance of reviewing your existing EOP policies that may have been created to help ‘alleviate’ user noise around false positives. While this original configuration certainly reduce false positives, it also significantly reduced the effectiveness of their spam detection!
Lesson 2: Post ATP Implementation, False Positives has increased
On the other side of the coin, after enabling ATP, it was noticed that a lot of emails were being marked as Spam/Spoof. As it turns out, this is expected behaviour where sender email systems will be scrutinised by ATP for SPF, DMARC & DKIM standards.
After some investigations into the increase ‘false positives’, many of the emails which were being marked as Junk were coming from domains missing SPF records and hence ATP marks such messages as Junk. One common way to verify this is analysing message header using Test Connectivity tool from Microsoft for the affected messages and looking at the X-Forefront-AntiSpam-Report header which indicates missing SPF records.
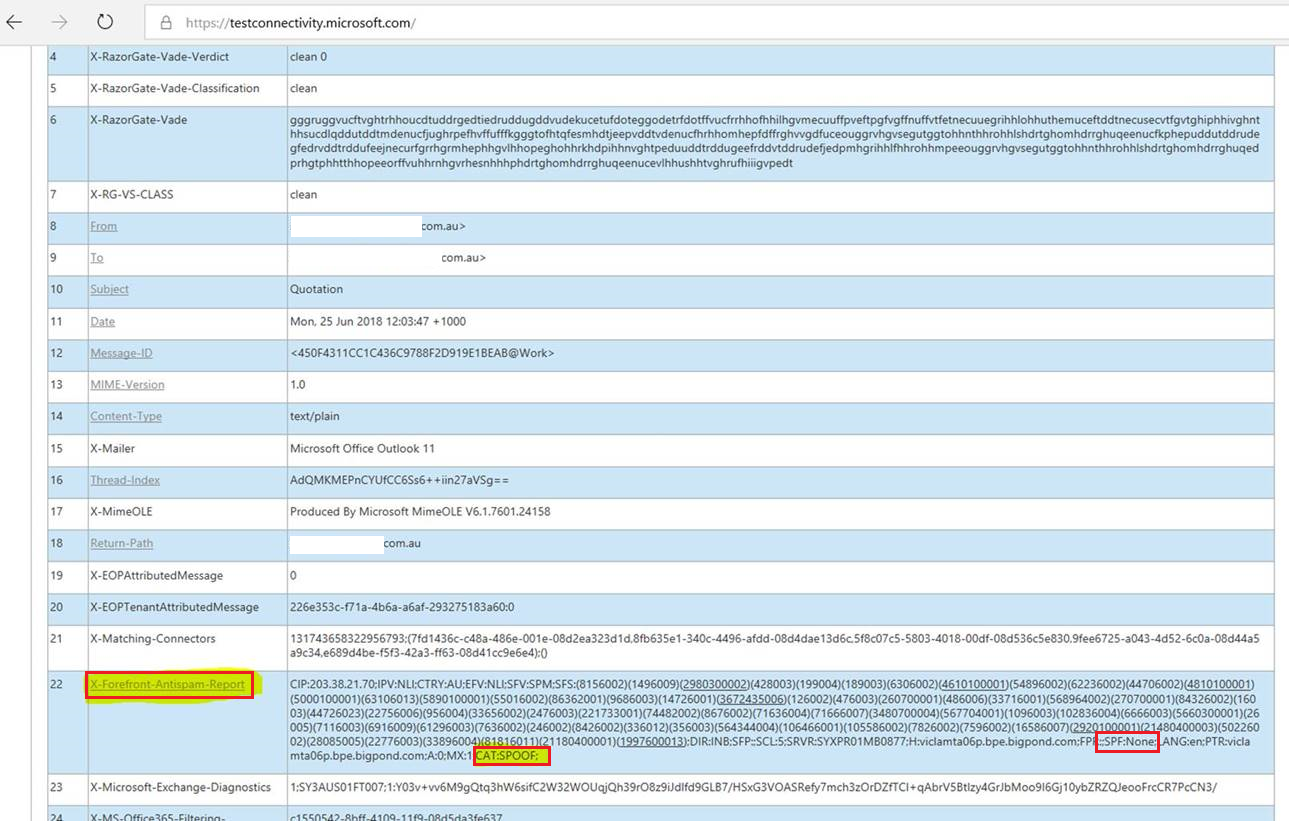
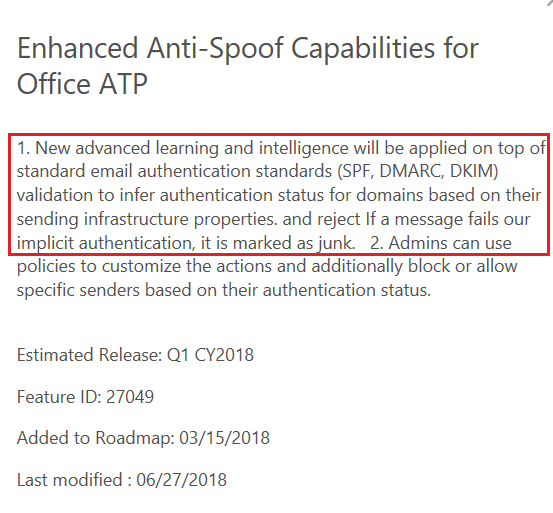
Microsoft acknowledges this can happen in the specific article:
https://products.office.com/en-us/business/office-365-roadmap?filters=%26freeformsearch=ATP#abc
This highlights the double-edge sword that Office ATP provides. It increases your sensitivity to spam email to protect your organisation, but it also relies on many technologies that fall in the realm of organizations to implement themselves to increase their own security and trust profile! SPF and DKIM are pretty much the standard in ‘increasing’ the reputation of your email domain and to protect your own email services, but it requires IT Admins to proactively configure it for their own domains, and many unfortunately still not reached that level of maturity!
Office ATP will certainly start showing you which of your partner organisations are still being ‘slack’ with their email security and should hopefully help you start the conversation to encourage them to do so!
~Cheers
HemantA
Category:
Uncategorized 