Introduction
In this post I will be talking about invalid cryptographic algorithm exception in web application. We have a multi-tenant single sign on asp.net application which connected with different identity provider to enable single sign on experience.
Background
Single sign-on multi-application scenario has been a soughed feature lately to make the user experience seamless across applications. In this case web application (service provider) was integrating with the ADFS 2.0 client hosted on Windows server 2012 R2 to implement single sign on experience for the end user on their network.
The application code written in C# uses component space helper facade to builds the http request using the Service provider configuration input parameters.
- Service provider name
- Assertion service endpoint url
- Service Provider sign on certificate and certificate password.
Certificate which was previously being used in the application for the assertion request had expired and new issued certificate which was when added to the ADFS server( Identity Provider) and the web application( Service Provider) when used was throwing an exception “Cryptographic Exception: Invalid Algorithm specified”.
On looking closely and debugging the code for the error I could notice exception “SAMLSignatureException: Failed to generate signature” was being thrown when it was stepping through the code segment where it was reading the certificate.
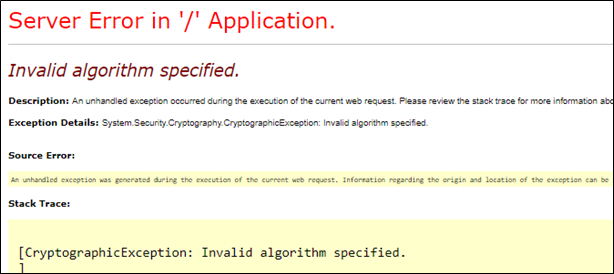
Resolution:
Certificate which has to be used by the assertion service expects to have Microsoft Cryptographic Service Provider (CSP) attribute set to “Microsoft Enhanced RSA and AES Cryptographic Provider”.
In this case the default certificate had the service provider configuration set as “Microsoft rsa schannel cryptographic provider”.
Difference is in the list of supported algorithms, key operations and key sizes. Microsoft RSA sChaneel Cryptographic provider doesn’t support the SHA-256 signature.
To check the certificate CSP we can check it using the below command and need to have open ssl on your system.
Command Prompt
\bin\openssl pkcs12 -in WebAppSelfSignedSSO.pfx
Make sure you point correct path to open ssl.
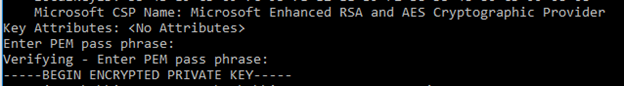
After the command is executed look for the Microsoft CSP Name attribute to confirm is if the CSP supports SHA-256 signature or not.
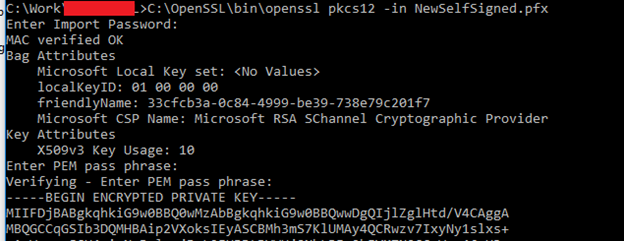
In this case we need to change the attribute to “Microsoft Enhanced RSA and AES Cryptographic Provider” to support SHA-256.
Then to update the CSP attribute to support SHA-256 signature in assertion request we need to run the below command to update the CSP.
-
Convert the pfx file to .pem from command prompt
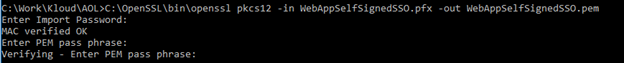
Once the command is execute successfully it will generate .pem file. -
Next convert the .pem back to pfx and update the CSP attribute property
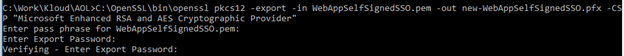
-
We can verify the CSP property has been changed to “Microsoft Enhanced RSA and AES Cryptographic Provider”
I hope this will help solve the issue. Happy Coding!!
