Azure Policy
Azure Policy is a service in Azure that you use to create, assign and, manage policy definitions. Policy definitions enforce different rules and actions over your resources, so those resources stay compliant with your corporate standards and service level agreements. Azure Policy runs an evaluation of your resources, scanning for those not compliant with the policy definitions you have.
Ref: https://docs.microsoft.com/en-us/azure/azure-policy/azure-policy-introduction
Mentioned below are the steps required for configuring Azure policies to monitor tags
Step 1 : Login on to the Azure Portal and search for Policy.
Step 2: Click on Definitions in the next screen.
Step 3 : Click on +Policy Definition.
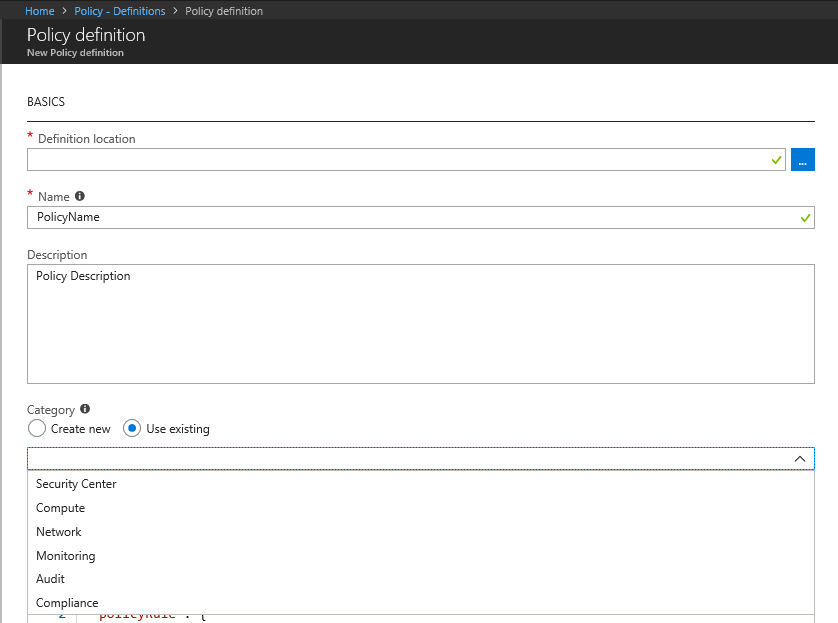
Step 4: Enter the following details in the next screen.
- Definition Location
- Policy Name
- Category
Step 5: Paste the below mentioned code in the Policy rules and Parameters section
( The code checks for all VMs with tags , and selects the VMS which do not have the tags mentioned in the script configured ).
Step 6 : Click on Save
{
"policyRule": {
"if": {
"allof": [
{
"field": "type",
"equals": "Microsoft.Compute/VirtualMachines"
},
{
"anyOf": [
{
"field": "tags.Tag1Name",
"exists": "false"
},
{
"field": "tags.Tag2Name",
"exists": "false"
},
{
"field": "tags.Tag3Name",
"exists": "false"
},
{
"field": "tags.Tag4Name",
"exists": "false"
},
{
"field": "tags.Tag5Name",
"exists": "false"
}
]
}
]
},
"then": {
"effect": "audit"
}
}
}
Step 7 : Click on Assignments
Step 8 : Click on Assign Policy
Step 9 : Complete the form with the following values.
- Scope ( Subscription / Resource Group/ Management Group )
- Exclusions ( Exclusions within the selected Scope )
- Select the policy definition just created.
- Enter an Assignment name
- Description of the Assignment.
- Name of the User ( by default it takes the name of the user account used for the assignment process.
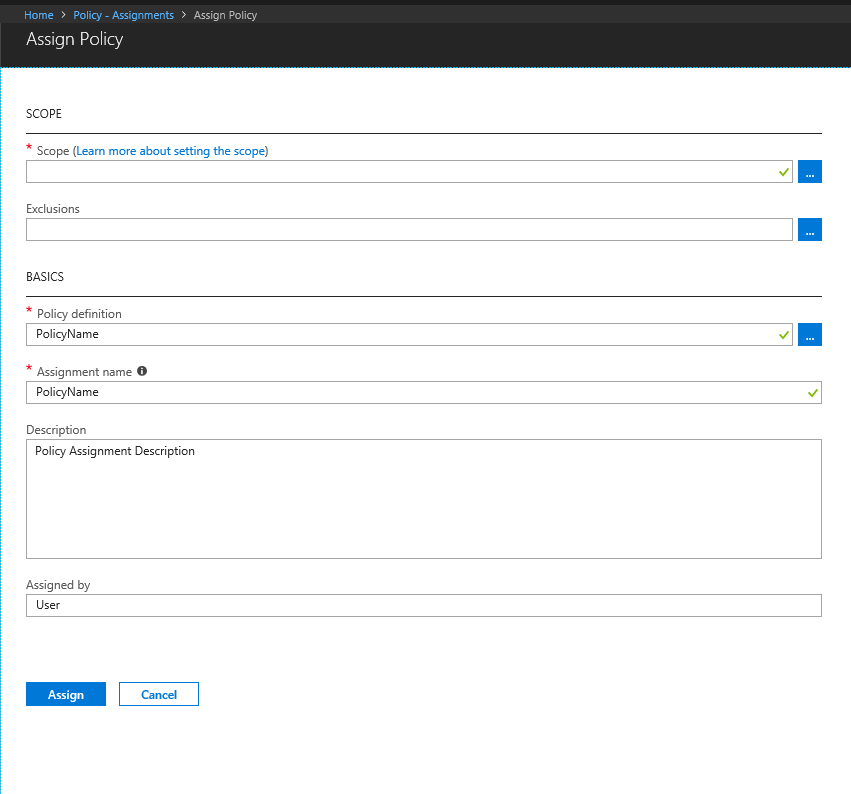
Step 10 : Click on Assign

Can you also describe the user experience and behavior of the policy. In my experience using policies have stopped admins manually deploying items into a resource group without using full ARM templating. i.e using the portal.
Hi Rob,
If the policy denies the creation of resources without TAGs, then that would indeed be the case.
In Azure , the resource creation wizard doesn’t provide an option for assigning tags due to which the validation check for the resource fails.
Thanks Syed. I ended up working around it in ARM with the following. I add the expressions with carets rather than single quotes. Not pretty, but effective:
{
“$schema”: “https://schema.management.azure.com/schemas/2018-05-01/subscriptionDeploymentTemplate.json#”,
“contentVersion”: “1.0.0.1”,
“parameters”: {},
“variables”: {
“^”: “‘”
},
“resources”: [
{
“name”: “auditTagExists”,
“type”: “Microsoft.Authorization/policyDefinitions”,
“apiVersion”: “2018-05-01”,
“properties”: {
“policyType”: “Custom”,
“mode”: “Indexed”,
“displayName”: “Audit that a tag exists”,
“description”: “Audit that the provided tag exists.”,
“policyRule”: {
“if”: {
“exists”: “false”,
“field”: “[trim(replace(‘ [concat(^tags.^, parameters(^tagName^))] ‘, ‘^’, variables(‘^’)))]”
},
“then”: {
“effect”: “[trim(replace(‘ [parameters(^effect^)] ‘, ‘^’, variables(‘^’)))]”
}
},
“metadata”: {},
“parameters”: {
“tagName”: {
“metadata”: {
“description”: “Name of the tag, such as ‘Owner'”,
“displayName”: “Tag Name”
},
“defaultValue”: “Owner”,
“type”: “String”
},
“effect”: {
“metadata”: {
“description”: “Effect if tag does not exist”,
“displayName”: “Effect”
},
“defaultValue”: “audit”,
“allowedValues”: [
“audit”,
“deny”,
“disabled”
],
“type”: “String”
}
}
}
}
],
“outputs”: {}
}
Can anyone help for creating Policy rules through ARM template to deploy through VSTS not in Azure Portal, Because i have Read access to the Policy Definition in Azure Portal