
Azure Application Security Groups (ASG) are a new feature, currently in Preview, that allows for configuring network security using an application-centric approach within Network Security Groups (NSG). This approach allows for the grouping of Virtual Machines logicaly, irrespective of their IP address or subnet assignment within a VNet.
They work by assigning the network interfaces of virtual machines, as members of the ASG. ASGs are then used within NSGs as either a source or destination of a rule, and this provides additional options and flexibility for controlling network flows of resources within a subnet.
The following requirements apply to the creation and use of ASGs:
- All network interfaces used in an ASG must be within the same VNet
- If ASGs are used in the source and destination, they must be within the same VNet
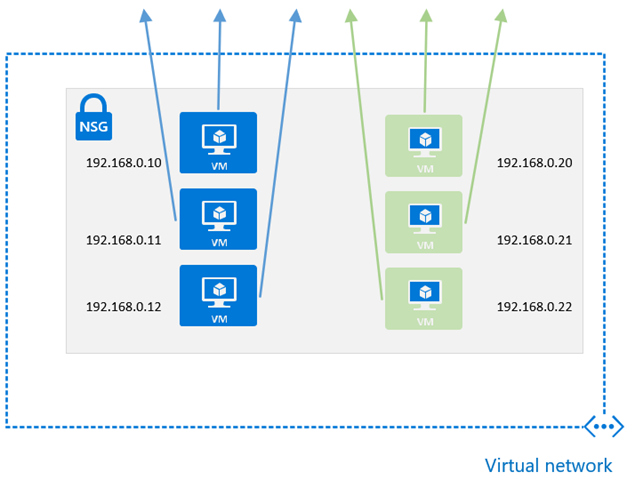
The following scenario demonstrates a use case where ASGs may be useful. In the below diagram, there are 2 sets of VMs within a single subnet. The blue set of VMs require outbound connectivity on TCP port 443, while the green set of VMs require outbound connectivity on TCP port 1433.
As each VM is within the same subnet, to achieve this with traditional NSG rules would require that each IP address be added to a relevant rule that allows the required connectivity. For example:
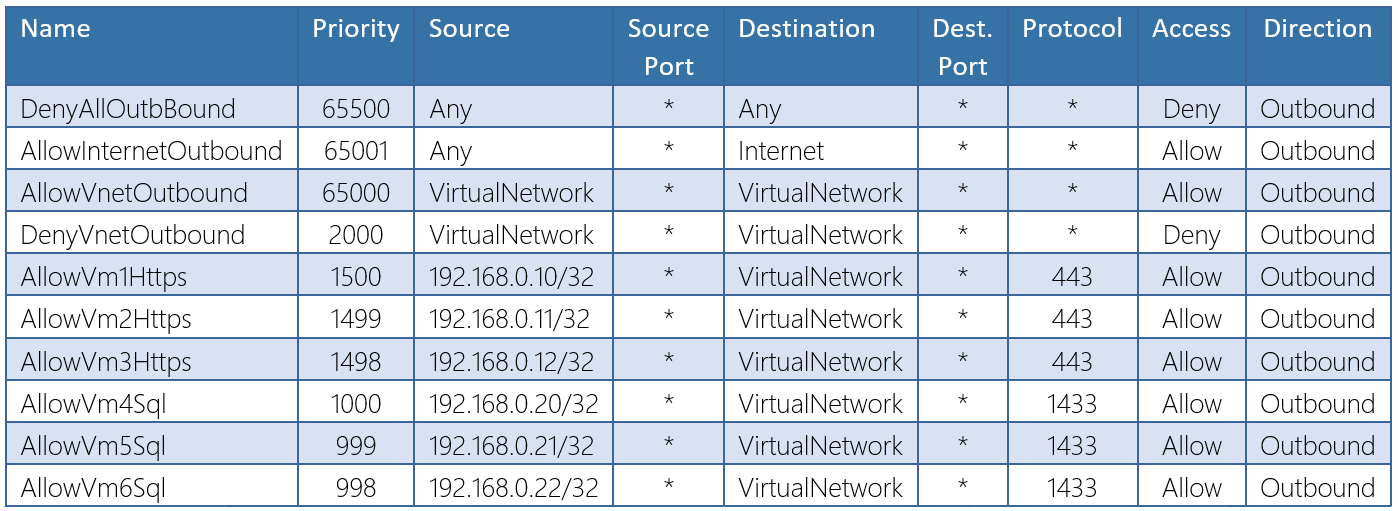
As virtual machines are added, removed or updated the management overhead that is required to maintain the NSG may become quite considerable. This is where ASGs come in to play to simplify the NSG rule creation, and continued maintenance of the rule. Instead of defining IP prefixes, you create an ASG and use the it within the NSG rule. The Azure platform takes care of the rest by determining the IPs that are covered within the ASG.
As network interfaces of VMs are added to the ASG, the effective network security rules are applied without the need to update the NSG rule itself.
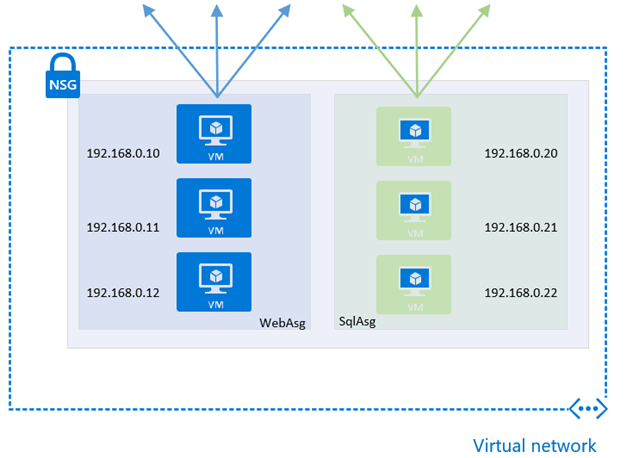
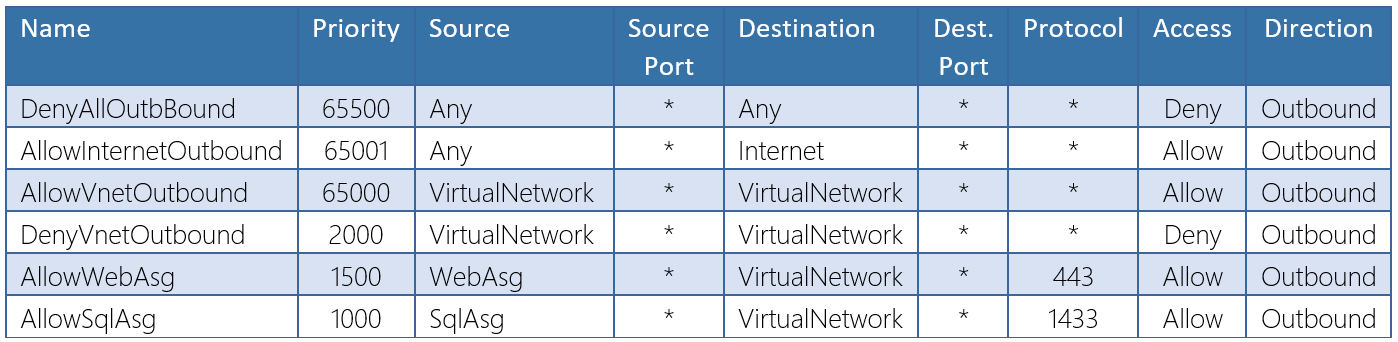
The following steps will demonstrate this process using 2 virtual machines.
Enable Preview Feature
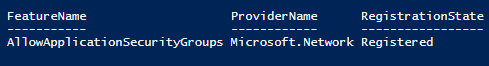
ASGs are currently in preview and the feature must be enabled. At present these are only available within US West Central.
Check the status of the registration, and wait for the RegistrationState to change to Registered.
Create Application Security Groups
We will create 2 application security groups
- WebAsg
- SqlAsg
Create security rules
In this example, we create rules that use the source as the application security group created in the previous step.
Create Network Security Group
Now that the ASGs are created and the relevant rules scoped to use the ASG as the source, we can create an NSG that uses these rules.
You can verify the rule from PowerShell, using Get-AzureRmNetworkSecurityGroup, and view the SecurityRules section. In there we can see that the reference to the ASG exists in SourceApplicationSecurityGroups:
Assign the NSG to a subnet:
Add network interfaces to ASG
The final step is to add the network interfaces of the VMs to the Application Security Group. The following example updates existing network interfaces to belong to the application security group. As network interfaces are added and removed the traffic flows will be controlled by the security rules applied to the NSG through the use of the ASGs, without further requirement to update the NSG.
You can verify this by viewing the network interface with Get-AzureRmNetworkInterface and checking the IpConfigurations properties. In there we can see the reference to the ASG memberships in ApplicationSecurityGroups.

Hi Micheal, is there any word from Microsoft around when the Application security groups feature will become Generally Available?
https://azure.microsoft.com/en-us/blog/applicationsecuritygroups/
GA’ed on April 2018
Just figured out you cannot reuse ASG’s across vnets, which is a big fail IMO as there are some settings you need applied to ALL VM’s regardless of what vnet they are located in, or am I architecting this the wrong way?